
Compliance in financial services industry: A Practical Guide
Get Compliance Consultation
Ensure your payment processing meets UK regulations with Paytia's compliance experts.
Compliance in the financial services world is far more than just a set of rules you have to follow. It’s the entire framework of laws, regulations, and internal policies that dictate how you operate. This isn't just about dodging hefty fines; it’s about upholding ethical conduct, championing consumer protection, and ensuring the stability of the entire financial system. For any business that takes payments, from a busy contact centre to a major bank, this is the very bedrock of your integrity.
Navigating the High Stakes of Financial Services Compliance
Think of financial compliance as captaining a ship through treacherous waters. The regulations are constantly shifting currents, the risks are hidden reefs, and one wrong move can have severe consequences for your business. This guide is your map and compass, designed to help you chart a safe and successful course through it all.

The first step is recognising the sheer scale of the challenge. The cost of just staying afloat is immense and growing. In the UK financial services sector, annual regulatory compliance costs have soared to over £33.9 billion. That's more than 13% of the average firm's yearly operating budget.
What’s more, a huge 84% of firms report that these costs have climbed in the last five years alone, making efficient compliance a critical priority for survival. You can dive deeper into these figures in TheCityUK's detailed report.
The Core Regulations You Can't Ignore
To navigate these waters safely, you need to know the key regulations and the bodies that enforce them. Here’s a quick overview of the main compliance pillars every UK financial business must understand.
| Key UK Financial Compliance Pillars at a Glance | |---|---|---| | Regulation | Primary Focus | Impact on Payment Handling | | PCI DSS | Securing cardholder data during processing, storage, and transmission. | Dictates how you must handle, store, and process payment card information to prevent fraud. | | GDPR | Protecting individuals' personal data and privacy rights. | Governs how you collect, use, and protect customer data, including names and addresses linked to payments. | | AML Regulations | Preventing the use of financial systems for illegal activities. | Requires you to verify customer identities and monitor transactions for suspicious activity. | | Consumer Duty (FCA) | Ensuring firms deliver good outcomes for retail customers. | Demands clear communication and fair treatment during all interactions, including payment processes. |
These frameworks aren't just abstract concepts for a legal team to worry about; they have real, daily implications.
For any business that handles payments, especially contact centres, these are not just suggestions. A single payment taken over the phone immediately brings your operations under the scope of multiple, overlapping regulations.
This guide will bridge the gap between these high-level rules and your day-to-day reality. We'll show you how secure, compliant payment handling is the foundation of customer trust, operational efficiency, and long-term business success. It's about transforming a regulatory headache into a strategic advantage that protects your customers and your bottom line.
Understanding the Core UK Financial Regulations
Diving into compliance for financial services can feel a lot like trying to read a foreign language. The regulations are thick with legal jargon, which makes it tough to see how they actually apply to your day-to-day work. Let's cut through the complexity and break down the essential rules that UK businesses have to follow.
Each regulation is designed for a specific job, but they all click into place the moment a customer makes a payment. Instead of seeing them as separate hurdles to jump over, think of them as interconnected layers of protection for your customers and, ultimately, for your business too.
PCI DSS: The Secure Recipe for Card Data
The Payment Card Industry Data Security Standard (PCI DSS) is the bedrock for handling card payments. The best way to think of it is like a secure recipe—one you must follow to the letter every single time you touch sensitive payment information. A chef wouldn't leave a secret recipe lying around, and in the same way, your business must guard card details against fraudsters.
This "recipe" gives you very specific instructions. For example, you must never write down the three-digit CVC code from the back of a card, and all systems that store or transmit card data have to be properly encrypted. For a contact centre, this means even a routine phone payment has to be handled with extreme care to stop data theft and keep customer trust intact.
GDPR: A Personal Data Guardianship
While PCI DSS is all about card data, the General Data Protection Regulation (GDPR) casts a much wider net, covering all personal information you gather. Think of GDPR as a kind of personal data guardianship. When customers share their name, address, or phone number, they're trusting you to look after it, and you have a legal obligation to do just that.
This means being completely open about what data you’re collecting and your reasons for doing so. This duty of care is especially important when you're taking payments. After all, payment details are directly tied to a specific person, putting your processes squarely under GDPR's watchful eye.
These regulations don't exist in isolation. A single phone payment triggers your duties under both PCI DSS to protect the card number and GDPR to safeguard the customer's personal details linked to that transaction.
This overlap is where things can get tricky. An agent taking a payment has to follow the secure PCI DSS recipe while also upholding the guardianship principles of GDPR, all in the same conversation. It’s precisely why solutions that remove sensitive data from your environment are so valuable—they dramatically simplify these overlapping responsibilities.
The FCA Consumer Duty: A Fair Treatment Promise
On top of data protection, the Financial Conduct Authority (FCA) has introduced its Consumer Duty. This regulation is essentially a fair treatment promise that every financial services firm must make to its customers. It's all about making sure your processes are designed to deliver good outcomes for the people you serve.
This principle has a direct impact on how you handle payments. Are your payment methods clear and easy to use? Are you giving customers secure options that protect them from foreseeable harm, like fraud? Asking a customer to read out their card details in an open-plan office, for instance, would be a clear failure to meet this standard of care.
This regulation marks a shift in thinking, moving from just ticking boxes to proactively putting the customer's interests first. Its influence is massive, affecting everyone from insurance and utility companies to retailers and housing associations that take regular payments.
AML and CTF: The Financial Crime Shield
Finally, we have the Anti-Money Laundering (AML) and Counter-Terrorist Financing (CTF) regulations. These rules act as the industry's financial crime shield, built to stop criminals from using legitimate businesses to wash dirty money or fund illegal activities.
While they're less about the mechanics of taking a single payment, these regulations mean you need to know who your customers are and keep an eye out for strange transaction patterns. An unusually large payment, or a sudden burst of frequent payments, could be enough to trigger an alert.
These four pillars—PCI DSS, GDPR, Consumer Duty, and AML/CTF—are the foundation of compliance in the UK. Getting to grips with what each one does, and more importantly, how they all fit together, is the first real step toward building an operation that is both secure and genuinely customer-focused.
Spotting Common Compliance Gaps and Hidden Risks
Knowing the rules is one thing, but seeing where your own operation falls short? That’s a whole different ball game. Compliance gaps aren’t usually caused by big, dramatic failures. More often, they’re the result of small, everyday process flaws that silently create enormous liabilities, chipping away at the trust you've worked so hard to build.

Think of these gaps as tiny cracks in a dam. One on its own might seem harmless, but under constant pressure, it only takes one to cause a catastrophic breach. For any business taking payments over the phone, these cracks often appear in very common, seemingly innocent practices.
The Dangers Hiding in Manual Processes
One of the most common—and dangerous—gaps I see is a continued reliance on old-school, manual methods for taking payment details. We’re talking about agents jotting down card numbers on notepads or keying them into unsecured spreadsheets.
Every single handwritten note or unencrypted file is a compliance disaster waiting to happen. It’s a direct violation of PCI DSS, which strictly forbids storing sensitive authentication data like CVC codes after a payment is authorised. This isn't just a theoretical risk; a lost notepad or a compromised workstation can very quickly spiral into a major data breach, leading to crippling fines and a shattered reputation.
I worked with a housing association that learned this the hard way. A routine audit uncovered that their call recordings contained unencrypted payment card details read out by customers. This one oversight led to a major PCI DSS failure, forcing them into a costly and frantic overhaul of their entire payment system.
This just goes to show how quickly a tiny process flaw can snowball into a full-blown compliance crisis. The risks are real, immediate, and the consequences can be severe.
The Hidden Threat in Your Call Recordings
Even with the best intentions, call recordings create a massive, and often overlooked, compliance headache. When a customer reads out their full card number, expiry date, and CVC, all of that sensitive data is captured and stored right there in the audio file.
Suddenly, your entire recording infrastructure—and anyone who can access it—is dragged into PCI DSS scope. Trying to secure that kind of environment is incredibly complex and expensive. Without rock-solid controls like pause-and-resume systems (which are notoriously unreliable), you’re essentially building a library of toxic data that’s a goldmine for fraudsters.
And the regulators are paying closer attention than ever. The Financial Conduct Authority (FCA) recently commissioned 83 s166 skilled person reviews—a staggering 77% jump from the previous year. These reviews mean bringing in independent experts to pick your processes apart, often resulting in enforcement action. You can see more on the FCA's heightened focus on compliance and risk management and what it means for firms.
Inadequate Training and the Human Factor
Of course, technology and processes are only ever half the story. Your agents are the human firewall, the frontline of your compliance efforts. Without proper, ongoing training, human error quickly becomes your single biggest vulnerability.
Some of the most common training gaps include:
- Mishandling sensitive data: Agents simply don't realise why they can't ask a customer to send card details over email or web chat.
- Poor social engineering awareness: A lack of training makes agents easy targets for fraudsters trying to trick them into revealing customer information.
- Forgetting the ‘why’: When agents don’t truly grasp the real-world impact of a data breach, they’re far less likely to follow security protocols to the letter.
At the end of the day, these common gaps—manual data capture, insecure recordings, and insufficient training—create a perfect storm of risk. They expose sensitive data, violate the core principles of PCI DSS and GDPR, and completely undermine the promise of fair treatment at the heart of the Consumer Duty. Finding these weak spots in your own operation is the first critical step toward building a payment environment that is genuinely secure and compliant.
Putting Technology to Work for Ironclad Security
Once you’ve identified the risks lurking in manual processes and shaky systems, the next step isn’t to pile on more manual checks. Real compliance in financial services means using smart technology to design sensitive data out of your environment from the very start. This is where modern solutions come in, not as complex add-ons, but as foundational tools for genuine security.
Let's break down the key technologies that can transform your payment handling from a high-risk liability into a secure, efficient, and compliant part of your operation. We’ll use some simple analogies to explain how they work and what they look like in a real contact centre.
The ‘Cone of Silence’: DTMF Suppression
Imagine your agent is on the phone, helping a customer make a payment. In a traditional setup, as the customer reads out their card number, every digit is captured on the call recording. That's a huge PCI DSS risk right there. This is exactly what DTMF (Dual-Tone Multi-Frequency) suppression is designed to prevent.
Think of it as a ‘cone of silence’ that activates the moment a payment is being made. The customer simply uses their telephone keypad to punch in their card number, CVC, and expiry date. While the agent stays on the line to help, the tones are masked—all the agent and the call recording hear is a flat, monotonous sound.
The actual, sensitive data travels directly from the customer’s keypad to a secure, PCI DSS Level 1 certified platform like Paytia. It completely bypasses your internal systems. This one technique ensures cardholder data never even touches your environment, which makes proving compliance a whole lot simpler.
The ‘Secure Valet Key’: Tokenization
After the payment data is captured securely, the next piece of the puzzle is tokenization. If DTMF suppression is the ‘cone of silence’, then tokenization works like a ‘secure valet key’ for your customer’s payment information. A valet key can start the car and move it, but it can’t open the boot or the glove box where the valuables are kept.
In the same way, tokenization replaces the customer's real 16-digit card number (the Primary Account Number, or PAN) with a unique, non-sensitive substitute—the token.
This token lets you do all the essential things—process the payment, issue a refund, or set up a recurring bill—without ever holding the actual, high-risk card details yourself. The real data is locked away safely in the payment provider's vault.
By working with tokens instead of raw card numbers, you slash your risk profile. If your systems were ever breached, all the criminals would find are useless tokens, not valuable card data they can sell or misuse. It’s a fundamental strategy for shrinking your PCI DSS scope.
Creating Secure Tunnels with Channel Separation
Another really effective technique is channel separation. Picture a busy motorway. Your normal business conversation between the agent and customer is the main flow of traffic. When it's time to pay, channel separation essentially creates a dedicated, secure express lane just for that payment data.
This is done by redirecting the payment part of the conversation through a completely separate, highly secure pathway. For instance, an agent can send a customer a secure payment link via SMS or web chat. When the customer clicks the link, it opens a secure, branded payment page on their own device.
The entire payment is completed inside this isolated, encrypted tunnel, totally separate from the agent's computer, your CRM, and your call or chat logs. This method works brilliantly across voice, chat, and even video calls, making sure that sensitive data never contaminates your core business systems.
Comparing Modern Controls to Traditional Methods
It’s clear these technologies represent a major shift away from older, high-risk practices. When you look at them side-by-side, the difference in security, cost, and the sheer effort of compliance is night and day.
To make this crystal clear, let's compare these modern, secure methods against the old way of doing things.
Comparing Compliance Scope Reduction Techniques
| Control Method | How It Works | PCI-DSS Scope Impact | Typical Use Case |
|---|---|---|---|
| DTMF Suppression | Masks keypad tones so agents and recordings never capture card data. | Massive Reduction as data bypasses your entire phone system. | Agent-assisted phone payments in contact centres. |
| Tokenization | Replaces sensitive card numbers with a non-sensitive 'valet key' token. | Significant Reduction by removing raw card data from storage. | Any system that needs to process repeat or future payments. |
| Channel Separation | Uses secure links or pages to create an isolated payment tunnel. | Massive Reduction by keeping the payment interaction off your network. | Multi-channel payments via web chat, SMS, or video. |
| Pause-and-Resume | Manually or automatically stops call recording during payment. | Minimal Reduction as it's prone to human error and still exposes agents. | Legacy contact centres with limited security options. |
Ultimately, adopting these modern controls means you’re no longer just managing risk—you’re actively eliminating it. This is the cornerstone of building an ironclad security posture that will satisfy regulators, protect your customers, and let your business grow with confidence.
Your Roadmap to a Compliant and Efficient Operation
Transitioning to a fully compliant operation can feel like a mountain to climb, but it doesn't have to be a frantic, all-at-once scramble. A strategic, step-by-step roadmap turns this complex challenge into a series of manageable milestones. This is about more than just plugging in new technology; it’s about carefully weaving together your processes, people, and platforms to create an environment that is secure by design.
Think of this as an investment in efficiency and trust, not just an expense. The FCA's push for faster, more transparent processes is impossible to ignore, especially when you look at its enforcement actions. With the largest single penalty hitting a staggering £44 million—the highest since 2022—the financial and reputational cost of getting it wrong has never been greater. For a closer look at the current climate, it's worth reading up on the latest UK financial services enforcement trends. The message is clear.
Stage 1: Assessment and Scoping
First things first: you need to know exactly where you stand right now. It's time to conduct a thorough, honest assessment of your current payment environment. Map out every single channel where you take payments—over the phone, via web chat, through your IVR—and pinpoint every touchpoint where sensitive cardholder data is handled, stored, or transmitted.
This initial scoping phase is absolutely critical for uncovering your specific vulnerabilities. Are agents scribbling down CVC numbers on notepads? Are call recordings capturing full card details? This deep-dive audit gives you a crystal-clear picture of your PCI DSS scope and flags the high-risk areas that need your immediate attention.
Stage 2: Solution Selection and Business Case
Once you understand your weak points, you can start looking for the right tools to fix them. You're searching for a platform that not only solves your immediate security problems but also integrates smoothly with the systems you already rely on, like your telephony and CRM software.
The real goal here is to find a solution that removes sensitive data from your environment entirely. This often involves technology that scrambles keypad data as it's entered and converts it into a secure token before it ever touches your systems.
Getting your stakeholders on board requires a compelling business case. Don't just talk about compliance; focus on the tangible return on investment (ROI). Frame the investment around these key benefits:
- Reduced Compliance Costs: Quantify the hours and resources you'll save on manual audits, evidence gathering, and remediation work.
- Lower Fraud Risk: Highlight the direct financial protection you gain by getting that toxic data out of your network.
- Improved Agent Efficiency: Show how taking agents out of the payment-handling loop frees them up to focus on what they do best—providing great customer service.
This diagram shows how modern secure payment technology works to protect data from the moment it's captured.
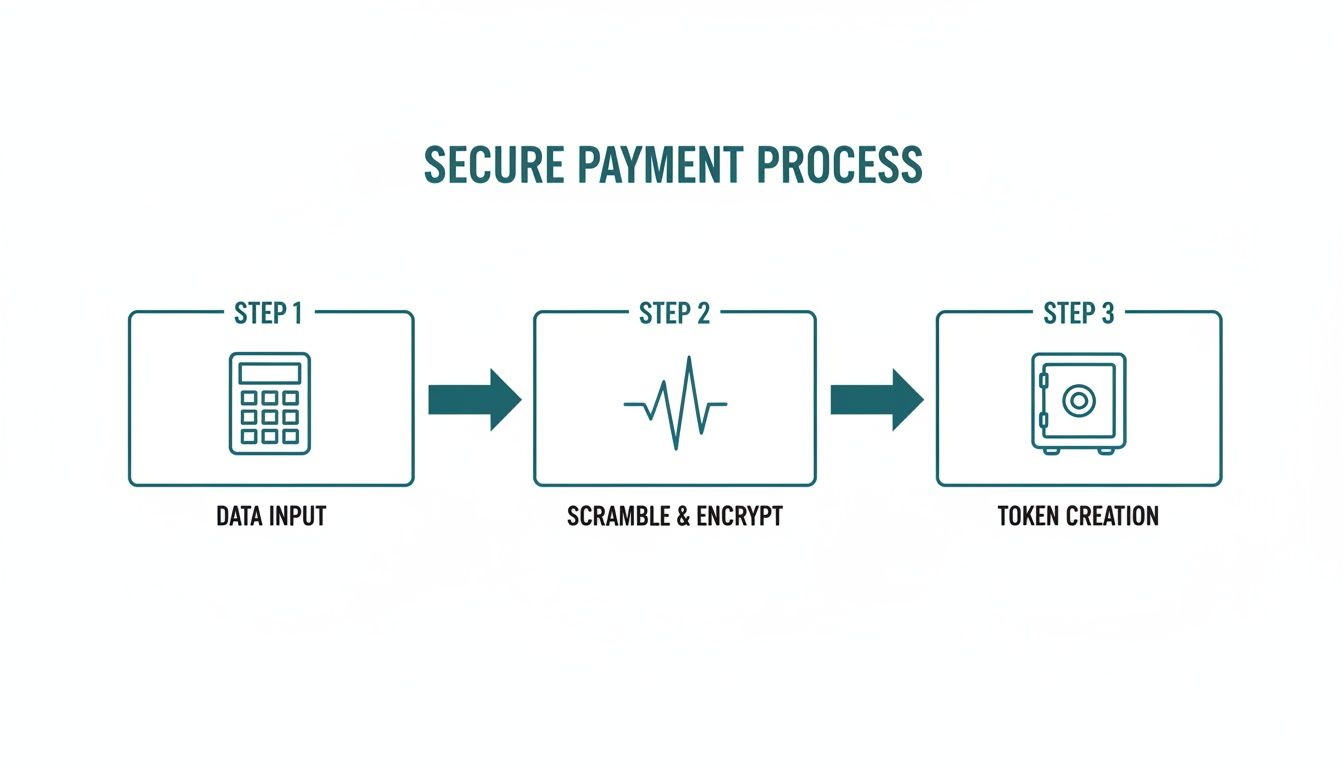 As you can see, the process ensures raw card details are scrambled and converted into a secure, non-sensitive token, meaning the original data never even enters your systems.
As you can see, the process ensures raw card details are scrambled and converted into a secure, non-sensitive token, meaning the original data never even enters your systems.
Stage 3: Phased Rollout and Training
Whatever you do, avoid a disruptive "big bang" implementation. A phased rollout, starting with a small pilot team, is always the smarter move. This approach lets you identify and iron out any process kinks in a controlled environment before deploying the solution across the entire organisation.
Training is also paramount. Modern systems are designed to be intuitive, but you need to ensure your agents understand not just how to use the new tools, but why they are so important. Good training reinforces the security-first culture that is absolutely essential for long-term compliance in the financial services industry.
Stage 4: Continuous Monitoring and Improvement
Compliance isn't a destination you arrive at; it's an ongoing discipline. Once your new system is live, use its reporting and analytics tools to keep a constant eye on your processes. These tools provide a crucial audit trail and give you the insights needed to refine your workflows over time.
Regularly review performance metrics to make sure the system is delivering on its promises of better efficiency and security. This continuous feedback loop transforms compliance from a reactive burden into a proactive strategy for operational excellence, keeping you secure, efficient, and always ready for scrutiny.
How Do You Know If You’re Actually Succeeding at Compliance?
Getting compliant isn’t a one-and-done deal. Think of it less like crossing a finish line and more like keeping a garden; it needs constant attention to thrive. The real goal is to stop treating compliance as a mad scramble for the annual audit and start embedding it into the very fabric of your daily work.
Success means being audit-ready, always. When a regulator knocks on your door, you shouldn’t need a three-week fire drill to pull together the right documents. The right tools give you the data you need on demand, helping you not only satisfy auditors but also uncover genuine ways to make your business run better and safer.
The KPIs That Really Matter
To know if your compliance efforts are paying off, you need to track a few key numbers. These Key Performance Indicators (KPIs) are what turn vague compliance goals into hard, provable results, showing everyone from the board to your frontline agents how your security investments are making a difference.
Here are a few powerful KPIs to get you started:
- Percentage Reduction in PCI DSS Scope: This is the big one. By using technology that keeps sensitive card data out of your environment entirely—like the solutions from Paytia—you can slash your audit scope by an incredible 90-95%. That’s a direct and immediate saving in audit costs, not to mention a massive reduction in your risk profile.
- Time Saved on Manual Compliance Tasks: Add up the hours your team used to spend on soul-destroying tasks like listening back to call recordings for compliance checks or manually compiling audit evidence. When you automate that, you’re not just saving time; you’re freeing up your best people to do more valuable work.
- Reduction in Chargeback Incidents: Better security and smoother, clearer payment processes almost always lead to fewer customer disputes. Every chargeback you avoid is money straight back to your bottom line.
By focusing on these KPIs, you change the conversation. Compliance in the financial services industry stops being a cost centre and becomes a clear strategic advantage that drives efficiency, builds customer trust, and makes the whole business stronger.
Ultimately, measuring success is about having proof. It’s about having the data to show auditors, your leadership, and your customers that you’re not just ticking boxes. You’re actively protecting them, day in and day out. This evidence-based approach is what separates the organisations that are genuinely secure from those just going through the motions.
Got Questions About Financial Compliance? We've Got Answers
When it comes to the nitty-gritty of financial compliance, a lot of practical questions tend to pop up. We get it. So, we’ve put together some straight answers to the most common queries we hear from businesses trying to lock down their operations and keep customer data safe.
How Can We Cut Our PCI DSS Scope Without Ripping Everything Out and Starting Again?
This is the big one, isn't it? The best way I’ve seen is to stop the sensitive card data from ever touching your own environment in the first place. Think of it like a secure airlock for payments.
Technologies like DTMF masking and secure digital payment links do just that. They let the customer tap their card details directly into a system that’s already a validated, PCI DSS Level 1 certified platform. The data is then immediately tokenised – swapped for a meaningless code – long before it gets anywhere near your agents, your call recordings, or your CRM. This simple shift can slash your PCI DSS scope by up to 95%. The best part? It bolts onto your existing phone and CRM systems, so you get maximum security without the headache of a complete system overhaul.
What's the Real Difference Between Being Compliant and Being Secure?
It's a crucial distinction, and one that trips a lot of people up. Think of it this way: compliance is about ticking the boxes to pass the test—meeting the minimum requirements set out in a standard like PCI DSS. Security, on the other hand, is a much bigger mindset. It’s the ongoing, active work of defending your data and systems against every possible threat out there.
You can be compliant but not actually secure if you’re only ever doing the bare minimum. A genuinely secure business, however, is almost always compliant by default because its defences are already so strong. The real goal shouldn't just be to pass an audit; it should be to build a true culture of security, using compliance rules as your roadmap.
How Does the FCA's Consumer Duty Change How We Should Handle Payments?
The FCA Consumer Duty is all about making sure you’re delivering good outcomes for your customers. When it comes to taking payments, this means the whole experience has to be secure, straightforward, and fair. Are you offering a range of secure ways to pay that suit different people, like over the phone with an agent, through an automated IVR, or via a simple payment link?
More importantly, the duty means you must protect customers from "foreseeable harm"—and fraud from a dodgy data capture process is a classic example. Using a verified, secure payment platform is a clear signal that you’re taking your duty to protect their financial wellbeing seriously. At the end of the day, solid security is one of the most powerful ways to show your customers you truly care.
Ready to stop worrying about compliance risks and make your payment process seamless? With Paytia, you can shrink your PCI DSS scope by up to 95% and lock down every single transaction. See how our certified platform can completely change the way you operate by visiting Paytia’s official website today.
Ready to Simplify Compliance?
Get expert guidance on UK payment regulations and PCI DSS compliance. Contact us today.
