
What is payment card industry compliance? A Clear Guide for UK Businesses
Get Compliance Consultation
Ensure your payment processing meets UK regulations with Paytia's compliance experts.
Let’s cut to the chase. Payment Card Industry (PCI) compliance is a set of security rules created by the big card brands—think Visa, Mastercard, and the like—to protect customer card data.
It’s a bit like the mandatory food hygiene rating for a restaurant. If you want to accept card payments, you must follow these standards to keep customer details safe and prevent fraud. It's not optional.
Understanding the Fundamentals of PCI Compliance

At its core, PCI compliance is all about one thing: creating a secure environment for sensitive payment information. The whole framework was established by the Payment Card Industry Security Standards Council (PCI SSC), a body formed by American Express, Discover, JCB International, Mastercard, and Visa.
Their goal was to stop the wild west of payment security by creating a single, unified set of rules. This became the Payment Card Industry Data Security Standard (PCI DSS), the rulebook for any organisation that handles their cards.
A common mistake is thinking PCI DSS is a government law. Here in the UK, it’s actually a contractual requirement pushed down by the card schemes through your acquiring bank. Whether you're a sole trader taking payments over the phone or a massive contact centre, if you store, process, or transmit cardholder data, you have to comply. You can dig into the specifics for UK businesses on this detailed guide from securious.co.uk.
Who and What Does It Protect?
The rules apply to absolutely everyone. If you accept or process payment cards—no matter your size or how many transactions you run—you’re on the hook. The moment a customer hands you their card, reads the number over the phone, or types it into your website, you become responsible for protecting that information.
The standard is laser-focused on safeguarding two types of sensitive data:
- Cardholder Data: This is the basic stuff—the full card number (Primary Account Number or PAN), the cardholder's name, and the expiration date.
- Sensitive Authentication Data: This is the really critical info. It includes the full magnetic stripe data, security codes (CAV2/CVC2/CVV2/CID), and PINs. A huge rule here is that this data must never be stored after a transaction is authorised.
PCI compliance isn't just a technical checklist to tick off. It's about preventing data breaches that can lead to devastating financial losses, cripple a business's reputation, and completely erode customer trust. It’s a fundamental part of doing business today.
To make things a bit clearer, here's a quick rundown of the key concepts we've covered so far.
PCI DSS Core Concepts at a Glance
| Concept | Brief Explanation |
|---|---|
| PCI DSS | The Payment Card Industry Data Security Standard—the official rulebook for securing card data. |
| PCI SSC | The council, formed by major card brands, that manages and updates the security standards. |
| Cardholder Data | The primary account number (PAN), cardholder name, and expiration date. |
| Compliance Type | A contractual requirement in the UK, enforced by banks—not a government law. |
Think of this table as your cheat sheet for the foundational language of PCI. Understanding these terms is the first step toward getting your compliance strategy right.
Navigating the 12 Core PCI DSS Requirements

At first glance, the Payment Card Industry Data Security Standard (PCI DSS) looks like a monster of a document, full of dense, technical jargon. But don't be intimidated. Its 12 core requirements all boil down to common-sense security principles.
The easiest way to get your head around them is to forget the long checklist and think in terms of six logical goals. This simple shift in perspective turns a daunting list into a manageable strategy. Each goal groups related requirements, making it much clearer why each rule exists and how it contributes to keeping payments safe.
For a full breakdown of every point, check out our deep dive into the 12 requirements for PCI compliance.
Goal 1: Build and Maintain a Secure Network
This is your foundation. It’s all about creating a strong perimeter to keep threats out of your systems. Think of it as building a fortress wall around your sensitive data.
Requirement 1: Install and Maintain Network Security Controls. In simple terms, this means using firewalls. A firewall is the digital gatekeeper for your network, inspecting all the traffic coming in and out and blocking anything that looks suspicious. Understanding the importance of firewalls is step one for any business that takes payments.
Requirement 2: Apply Secure Configurations to All System Components. Default passwords and settings are a welcome mat for hackers. This rule is about changing all vendor-supplied defaults and getting rid of any software you don't need, effectively shutting and locking any unnecessary doors.
Goal 2: Protect Account Data
Once your network perimeter is secure, the next job is to protect the actual card data inside it, whether it’s sitting on a server or moving across the network.
Requirement 3: Protect Stored Account Data. The absolute best way to protect stored data is... not to store it at all. If you absolutely have to, this rule demands that you make it unreadable using tools like encryption, hashing, or tokenization. A Post-it note with a CVV number on it is a classic—and very dangerous—violation.
Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission. When card details travel across open networks like the internet, they must be encrypted. This is exactly what the little padlock icon in your browser address bar is for—it's a sign that the data is being scrambled to protect it from anyone trying to eavesdrop.
Goal 3: Maintain a Vulnerability Management Programme
Security isn't a one-and-done job. It’s a constant process of finding and fixing weaknesses before attackers can find and exploit them.
Requirement 5: Protect All Systems and Networks from Malicious Software. This is your anti-virus and anti-malware requirement. It’s about making sure this software is installed and, crucially, kept up to date on every system that could be a target.
Requirement 6: Develop and Maintain Secure Systems and Applications. When a software developer finds a security hole, they release a patch to fix it. This requirement is all about installing those security patches as soon as they’re available to close any known gaps in your defences.
A robust security posture is dynamic, not static. It requires continuous monitoring and adaptation to protect against emerging threats, turning compliance from an annual task into a daily operational habit.
Goal 4: Implement Strong Access Control Measures
This goal is all about making sure that only the right people can access sensitive data, working on the principle of ‘least privilege’.
Requirement 7: Restrict Access by Business Need to Know. An employee should only have access to the specific cardholder data they absolutely need to do their job. For example, a contact centre agent might need to process a payment, but they have no reason to see the entire transaction history database.
Requirement 8: Identify Users and Authenticate Access. No anonymous users. Every single person with access to your systems needs their own unique ID. This is non-negotiable for tracking who does what and preventing the security nightmare of shared accounts.
Requirement 9: Restrict Physical Access. This one moves from the digital world to the physical one. Any computer, server, or even paper file containing card data needs to be physically locked away in a secure room or cabinet.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you can't see. This goal focuses on actively looking for suspicious activity and regularly testing your defences to make sure they still work.
Requirement 10: Log and Monitor All Access. You need to keep detailed logs of everything that happens on your network. If a security incident does occur, these logs are absolutely vital for figuring out what happened, when, and how.
Requirement 11: Test Security of Systems and Networks Regularly. This means proactively looking for holes by running things like vulnerability scans and penetration tests. It’s about finding and fixing your own weaknesses before a criminal does.
Goal 6: Maintain an Information Security Policy
Finally, everything you do for security has to be wrapped up in a formal, documented policy that everyone in your organisation actually understands and follows.
- Requirement 12: Support Information Security with Organizational Policies. This policy is the master document for your company's security strategy. It makes sure everyone, from a new hire to the CEO, knows their responsibilities and helps build a culture where security is everyone's job.
Why Compliance Is Business-Critical for UK Contact Centres
For any business that takes payments, PCI compliance is on the radar. But for UK contact centres, it’s not just important—it’s a matter of survival. Your entire business model is built on conversations, and the moment those conversations involve payments, you become a prime target for fraud.
The reason is simple: contact centres are the epicentre of Card-Not-Present (CNP) transactions. Unlike a shop where a customer physically hands over their card, CNP payments happen over the phone or via webchat. This distance creates a security gap that fraudsters are more than happy to exploit.
The statistics paint a pretty stark picture. According to UK Finance’s 2023 Fraud Report, CNP fraud was responsible for over 70% of all card fraud in the UK, making it the dominant channel by a huge margin. The average cost of a UK data breach is forecast to hit around £3.2 million in 2025, and non-compliant businesses can be hit with monthly fines anywhere from £4,000 to £80,000.
The Unique Vulnerabilities in a Contact Centre
So, what makes a contact centre such a uniquely risky environment? It's the sheer number of places where sensitive cardholder data can be accidentally exposed or maliciously stolen. Every single conversation is a potential point of failure.
These vulnerabilities often hide in plain sight, embedded in everyday processes that seem completely harmless but are, in fact, compliance disasters waiting to happen.
Common weak spots include:
- Insecure Call Recordings: Standard call recording systems capture everything an agent hears, including a customer reading out their full card number and CVC. Storing these recordings means you’re storing raw, unprotected card data—a direct violation of PCI DSS.
- Unencrypted Digital Channels: When agents take payments via webchat or messaging apps, they often ask customers to just type their details into the chat window. This unencrypted text gets logged, stored, and is easily compromised.
- Manual Data Entry: An agent keying card details into a virtual terminal is a high-risk activity. The process exposes the agent to sensitive data, creating opportunities for both accidental leaks and internal fraud.
- Makeshift Storage: Think of spreadsheets used to track payments, sticky notes with card numbers jotted down for a callback, or details saved in an unsecured CRM notes field. Each one is a ticking time bomb.
The Rise of Remote Work Adds Complexity
The massive shift to remote and hybrid working has thrown another spanner in the works. When agents work from home, that secure, controlled office environment simply vanishes.
They’re operating on less secure home networks, often using personal devices, and are outside the direct physical supervision of their managers. This decentralised model exponentially increases the attack surface for criminals. Trying to ensure payment security across dozens, or even hundreds, of individual home offices is a monumental task without the right technology. For financial businesses especially, dedicated IT Services for Finance: A Guide to Security and Compliance become paramount to protect sensitive payment data in these distributed environments.
For a modern UK contact centre, failing to secure payment channels is no longer just a compliance issue. It's a direct threat to your business continuity, financial stability, and the trust you've worked so hard to build with your customers.
The consequences of a breach go far beyond fines. The reputational damage can be irreversible, leading to a mass exodus of customers who no longer feel safe sharing their details with you. In a competitive market, that loss of trust can be fatal. This is why a proactive strategy, using purpose-built call centre payment security solutions, is not just a best practice but a business necessity.
How to Master Your PCI Scope and Assessment
Getting your head around PCI scope is the single most important thing you can do to simplify your compliance journey. If you get this part right, everything that follows becomes easier, cheaper, and faster. Get it wrong, and you’re signing up for a huge, expensive, and frankly never-ending security project.
Think of your PCI scope as a ‘blast radius’. At the very centre is your customer's card data. Every single person, system, process, or bit of technology that touches that data—or is even on the same network—gets pulled into this radius. The bigger that radius, the more complex and costly your compliance becomes.
So, your number one goal should be to make this blast radius as small as humanly possible. A smart PCI strategy isn't just about securing the data; it’s about radically shrinking the number of things that need securing in the first place.
Defining Your Assessment Level
In the UK, the intensity of your PCI assessment boils down to your transaction volume. The major card brands (Visa, Mastercard, etc.) group businesses into different levels, and while the exact numbers can vary a bit between them, the structure is generally the same.
Most businesses will find themselves in one of four levels:
- Level 1: This is the highest level, reserved for merchants processing over six million card transactions a year. These businesses face a rigorous annual audit from a Qualified Security Assessor (QSA).
- Level 2: For businesses that handle between one and six million transactions annually.
- Level 3: Typically for e-commerce merchants processing between 20,000 and one million transactions.
- Level 4: For smaller merchants processing fewer than 20,000 e-commerce transactions or up to one million transactions through other channels.
Businesses in Levels 2, 3, and 4 can usually prove their compliance by completing a Self-Assessment Questionnaire (SAQ). But which SAQ you have to fill out depends entirely on how you handle cardholder data—which brings us right back to scope.
Demystifying the Self-Assessment Questionnaires
The SAQ is simply a reporting tool you use to document where you stand with PCI DSS. The thing is, there are several different versions, each designed for a specific business model. For a contact centre, the difference between the easiest and hardest SAQ is night and day.
The type of SAQ you are required to complete is a direct reflection of your risk profile. A simpler SAQ signifies that you have successfully shifted the risk of handling card data to a compliant third-party provider, dramatically reducing your own compliance burden.
For contact centres, two SAQs represent the opposite ends of the compliance spectrum. On one side, you have SAQ D, the behemoth—it's the most comprehensive and difficult questionnaire by a long shot. On the other, you have SAQ A, the simplest form, designed for businesses that have almost completely outsourced their card payment processing.
The image below highlights the common risks that pull a contact centre into the punishing scope of SAQ D.
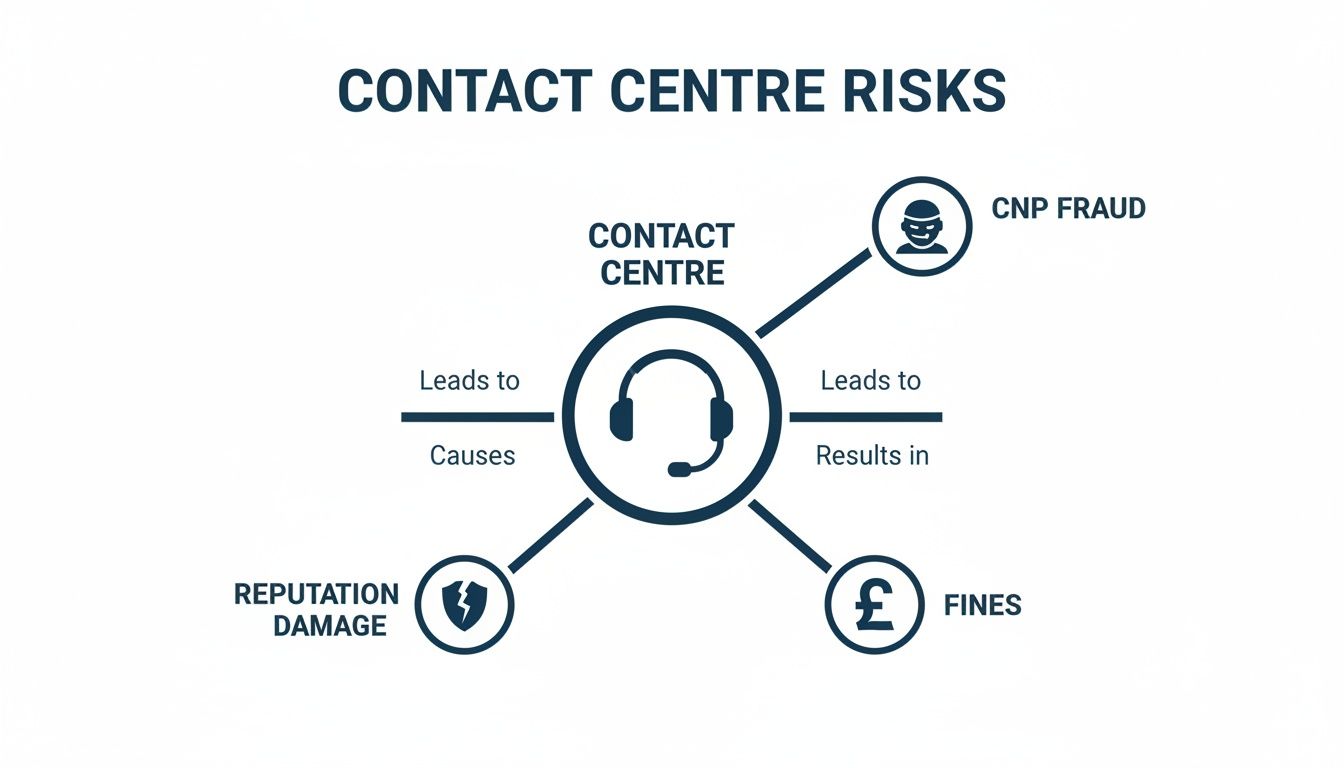
As you can see, any direct contact with card data introduces massive risks like fraud and eye-watering financial penalties. These are the very things a wider PCI scope is meant to prevent.
The difference in effort between these two questionnaires is staggering. SAQ D requires you to prove compliance with all 329 applicable PCI DSS requirements. In contrast, SAQ A slims this down to just 22 requirements, which focus almost entirely on how you manage your payment provider relationship.
This table really puts the difference into sharp focus.
SAQ D vs SAQ A A Comparison for Contact Centres
When a contact centre successfully de-scopes its operations, the compliance workload shrinks dramatically. The shift from an SAQ D to an SAQ A isn't just a small step; it's a giant leap in simplifying security management.
| Compliance Aspect | SAQ D (Full Scope) | SAQ A (De-Scoped) |
|---|---|---|
| Number of Controls | Over 300 PCI DSS requirements | Approximately 22 PCI DSS requirements |
| Effort Required | Extremely high; requires deep technical expertise, extensive documentation, and rigorous testing of all systems in scope. | Very low; focused on ensuring your payment service providers are compliant and your processes don't bring card data into your environment. |
| Internal Systems | All systems, networks, and applications that store, process, or transmit card data are in scope and must be secured. | No internal systems handle card data. Your environment is completely isolated from the payment process. |
| Typical Scenario | Agents manually key card details into a virtual terminal; call recordings capture sensitive data; chat logs store PAN/CVC. | All payments are handled by a third-party solution like Paytia; card data never enters your systems, network, or applications. |
This comparison isn't just an academic exercise; it represents a fundamental strategic choice. Actively working to de-scope your environment from an SAQ D to an SAQ A is the single most effective way to cut costs, minimise risk, and make PCI compliance a manageable, sustainable process instead of an annual headache.
Using Technology to Simplify Your Compliance Journey

Managing PCI scope can feel like a relentless defensive battle, constantly plugging holes and watching for threats. But what if you could change the rules of the game? By far the most effective strategy is to stop sensitive card data from ever touching your environment in the first place.
This is where modern payment technology really shines. Instead of building taller walls around your existing systems, these solutions create secure tunnels that completely bypass your network. They act as a protective buffer between your business and raw card details, dramatically shrinking your PCI scope and simplifying what was once a complex security headache.
Ultimately, these technologies are the key to moving from a high-risk, high-effort SAQ D to a much simpler, low-effort SAQ A.
Tokenization: The Digital Casino Chip
Picture yourself in a casino. You don’t walk around with wads of cash; you swap it for chips. Inside the casino, those chips have value. But if a thief snags them, they’re just worthless plastic discs outside.
That’s exactly how tokenization works. When a customer gives you their card details, a secure system intercepts that information and immediately swaps the sensitive Primary Account Number (PAN) for a unique, non-sensitive string of characters—a token.
This token can then be safely used for processing that payment or even setting up recurring billing, all without ever exposing the real card number. If a data breach happened, all the hackers would find are these useless tokens, not valuable financial data.
End-to-End Encryption: The Armoured Truck
Now, imagine moving money between banks. You wouldn't just toss it in a regular van. You’d use a locked, armoured truck that can only be opened by an authorised person at the final destination.
End-to-end encryption (E2EE) provides that level of security for card data on the move. From the instant a customer enters their details, the information is scrambled into an unreadable format. It travels across your networks and the internet in this protected state and can only be decrypted by the authorised payment processor at the very end of its journey.
The real power of these technologies is that they remove the ‘human factor’ and system vulnerabilities from the equation. By ensuring card data never touches your environment, you eliminate the single biggest risk in your payment process.
Securing Phone and Chat Payments
These principles become absolutely vital in contact centres, where taking payments over the phone and via chat introduces unique vulnerabilities. Two key technologies are designed to tackle these specific risks head-on.
- DTMF Suppression: When a customer uses their phone keypad to enter card details (a process using Dual-Tone Multi-Frequency), this tech masks the tones. Instead of the tell-tale beeps that give away the numbers, your agent hears only a flat, monotone sound, and the call recording captures nothing of value.
- Channel Separation: For payments made through webchat or messaging, this approach creates a separate, secure digital channel. The customer types their details into a secure form that is completely isolated from the agent's screen and your chat logs, keeping the data entirely out of your systems.
By adopting these solutions, you fundamentally de-scope your agents, their computers, your phone systems, and even your call recording archives from PCI requirements. This is what modern payment card industry compliance is all about—using smart tools to minimise your risk profile. You can learn more about how Paytia helps with PCI compliance by putting these very technologies to work for you.
Building a Modern and Resilient Compliance Strategy
It’s tempting to look at PCI DSS as just another item on a long, tedious compliance checklist. But that narrow view misses the bigger picture entirely. Payment compliance isn't some isolated chore anymore; it’s a core piece of your organisation's entire data protection strategy.
Think of your security posture as a single, interconnected ecosystem. A weakness in one spot—like your payment channels—can send a shockwave through the whole system. A breach that starts with a single stolen card number can quickly spiral, exposing entire customer databases and putting your entire business at risk.
Unifying Security Frameworks
This interconnectedness means PCI DSS compliance doesn't exist in a vacuum. It sits right alongside other critical frameworks that govern data security and privacy, such as the UK's GDPR and international standards like ISO 27001.
GDPR Alignment: At their heart, both PCI DSS and GDPR are about protecting sensitive data. While GDPR casts a wide net over all personal information, PCI DSS provides a highly specific, prescriptive rulebook for protecting the very card data that falls under GDPR's umbrella. A rock-solid PCI strategy directly supports your GDPR obligations.
ISO 27001 Synergy: This framework gives you a blueprint for building, running, and improving an Information Security Management System (ISMS). The tough controls demanded by PCI DSS map directly onto many of the security domains within ISO 27001. This means your PCI efforts are also a major step towards broader cybersecurity certification.
Recent UK incidents and regulatory chatter show this convergence is only getting faster. A 2025 compliance benchmark found that 85% of UK respondents expect their strategy to change because of new regulations. A similar number plan to chase an ISO 27001 audit to get their cyber-risk programmes in order. You can dig deeper into how UK businesses are adapting by reviewing these key findings on retail cyber-attacks.
From Reactive Chore to Strategic Pillar
This shift in thinking requires a proactive, unified approach. Stop treating compliance as a reactive chore—a box-ticking marathon you run once a year. Instead, position it as a strategic pillar of your business resilience.
Adopting a certified, secure payment solution is more than a quick compliance fix. It's a strategic decision that strengthens your entire security posture, reduces organisational risk, and builds the lasting customer trust that is essential for long-term success.
When you de-scope your environment and get toxic card data out of your systems, you're not just making an audit easier. You are actively shrinking your attack surface, slashing the risk of a catastrophic data breach, and sending a clear message that you are serious about protecting your customers. This reframes the whole conversation from a cost of doing business to a direct investment in your brand's reputation and resilience.
Answering Your Top PCI Compliance Questions
As you start digging into payment card compliance, a few common questions and myths always seem to pop up. Let's tackle some of the ones we hear most often, giving you clear, straightforward answers to separate fact from fiction.
Getting these details right is crucial, especially when you’re navigating the realities of modern business, like remote teams and complex payment channels.
PCI DSS vs GDPR: What’s the Difference?
It’s easy to get these two confused since they both deal with data protection, but they play very different roles. Think of it like this: GDPR is a broad, sweeping law that protects all personal data for people in the UK and EU—everything from names and email addresses to website browsing habits.
PCI DSS, on the other hand, is laser-focused. It’s a specific security standard created by the card brands purely to protect payment card data. While being PCI compliant is a huge step towards protecting financial data under GDPR, it doesn't automatically make you GDPR compliant, and vice versa. They're two separate challenges you need to solve.
The key takeaway is this: GDPR is a wide-ranging privacy law enforced by government regulators, while PCI DSS is a specific security standard enforced by the card brands. You need a plan for both.
Can Our Agents Be Compliant While Working from Home?
Yes, absolutely—but only if you have the right technology in place. The single biggest risk with remote agents is sensitive card data leaking into their home environment. We’re talking about their personal computers, their home Wi-Fi networks, or even just the numbers being spoken aloud where family members might overhear.
This is where de-scoping solutions become essential. By using tech like DTMF suppression or secure digital payment links, the card data completely bypasses the agent's home setup. The customer enters their details directly and securely into the payment system, meaning the agent never sees, hears, or touches the sensitive information. This makes remote work compliance not just possible, but incredibly straightforward.
Is Using a Compliant Payment Gateway Enough on Its Own?
This is probably the most persistent and dangerous myth in the world of PCI compliance. Simply using a big-name, compliant payment gateway like Stripe or Adyen is not enough to make your entire business compliant.
Why? Because if you handle the raw card data at any point before it gets to that gateway, you're in scope. For instance, if your agent takes a card number over the phone and manually types it into a virtual terminal, your agent, their computer, your network, and your phone systems are all in scope. The payment journey has to be secure from start to finish. If you touch the data, you’re responsible for protecting it.
Achieve effortless PCI compliance and secure every payment channel with Paytia. Our Secureflow platform removes your systems from the scope of PCI DSS, protecting your customers and your reputation. Discover how Paytia can simplify your security at https://www.paytia.com.
Ready to Simplify Compliance?
Get expert guidance on UK payment regulations and PCI DSS compliance. Contact us today.
