
Securely Accept Card Payments Over the Phone Your Complete Guide
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
To take card payments over the phone securely, you need a solution that stops sensitive card details from ever touching your business systems. This is the golden rule. Technologies like DTMF suppression or secure payment links are designed to do exactly that, keeping your operations out of the line of fire.
By preventing card data from being heard by agents or captured in call recordings, you drastically shrink your PCI DSS compliance scope. It’s the cornerstone of modern, secure phone payments.
Why Taking Payments by Phone Still Matters
With all the focus on slick online checkouts, it's easy to think that taking card payments over the phone is a thing of the past. That's a huge misconception. For many businesses, it's a vital, human-first channel that digital methods simply can't replicate.
Think about it. That direct conversation builds trust and delivers a personal touch that customers often need and appreciate.
Loads of industries depend on phone payments for a significant chunk of their revenue. Here are just a few everyday examples:
- Hospitality and Travel: A guest rings up a hotel to book a specific room with a sea view, giving their card details right there and then to the booking agent.
- Professional Services: A law firm takes a deposit over the phone to confirm a new client's first consultation. It's quick, direct, and gets the relationship started.
- Telesales and Subscriptions: A sales agent has a customer on the line, excited about a new software subscription. Taking payment immediately seals the deal before the customer's attention wavers.
- Utilities and Debt Collection: A support agent helps someone clear an overdue utility bill, providing a straightforward and reassuring way to settle their account.
The Card-Not-Present Challenge
The technical term for a phone payment is a Card-Not-Present (CNP) transaction. Unlike a shop where you can tap your card on a terminal, a CNP transaction relies on the customer reading out their card details. This is where the security headaches begin.
The biggest risk with phone payments is simple: the card number, expiry date, and CVV code can be heard by agents, stored in call recordings, and filter into other company systems. This exposure blows up your PCI DSS responsibilities and opens the door to data theft or even accidental leaks.
And we're talking about a massive volume of transactions. In the UK alone, debit cards were used for a staggering 26.1 billion payments in a single recent year. While a lot of that is contactless, sectors like telesales, charities, and hospitality rely heavily on phone payments to capture business they'd otherwise lose. For a deeper dive into these figures, check out the UK Finance payment markets report.
The real trick is to balance a smooth, convenient customer experience with iron-clad security that keeps card data completely out of your environment. Get that right, and you've built a phone payment system people can trust.
Choosing the Right Secure Payment Architecture
Deciding how to accept card payments over the phone isn’t a one-size-fits-all situation. It’s about finding the perfect fit for your business, your customers, and how your team actually works. Get this right, and you’ll improve the customer experience, boost team efficiency, and—most importantly—slash your PCI DSS compliance headache.
There are a few well-established ways to handle phone payments securely. Each has its own pros and cons. The main goal, always, is to pick an architecture that stops sensitive card data from ever touching your environment. This protects your customers, and it protects you.
This simple flowchart can help you see if phone payments are a major channel for your kind of business.
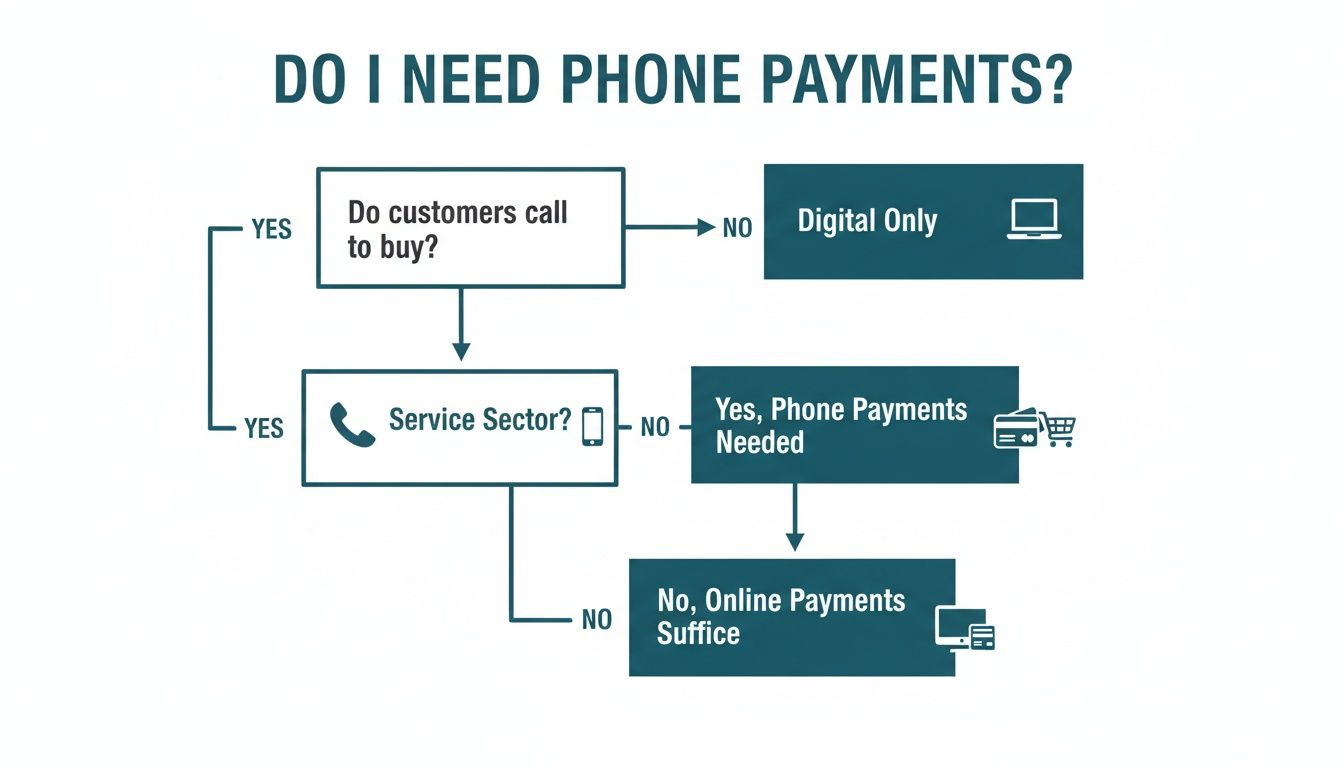
As you can see, businesses in the service industry are prime candidates. Purely digital outfits? Probably not so much. Let's dig into the main options you'll be weighing up.
Agent-Assisted Payments with DTMF Masking
This is one of the most popular and effective methods out there, especially for contact centres. The beauty of it is that the customer stays on the line with a real person, keeping that human connection intact.
When it's time to pay, the customer simply taps their card number, expiry date, and CVV into their telephone keypad. This is where the magic happens: DTMF (Dual-Tone Multi-Frequency) masking technology intercepts those beeps before they can reach your agent or your call recording system. The agent just hears flat, muffled tones, meaning they are completely shielded from the card details.
The DTMF data zips directly to the payment gateway for authorisation. All the agent sees on their screen is a simple success or fail message.
Where Does This Shine?
- Complex Sales or Support: It’s perfect when an agent needs to talk a customer through a tricky purchase, add on services, or sort out an issue before taking the payment.
- High-Touch Customer Service: Think bespoke travel agents or professional service firms. Any business that values personal interaction will find this model a natural fit.
- Debt Collection: This approach allows for a sensitive, guided payment process, which can make all the difference in these conversations.
Automated IVR Payments
For routine transactions, an automated Interactive Voice Response (IVR) system is a game-changer. It gives customers a self-service option to pay 24/7, without ever needing to speak to an agent.
A customer just calls a dedicated number, follows the voice prompts, and enters their account and card details using their keypad. The whole thing is automated, secure, and completely removes your team and infrastructure from the payment process.
By funnelling all your routine payments through an IVR, you not only shrink your PCI DSS scope to almost nothing but also free up your best agents to focus on more complex, valuable customer conversations.
Secure Payment Links via Phone
Here we have a smart hybrid approach that mixes a live conversation with a smooth digital checkout. While on the phone with a customer, your agent can generate a unique, time-sensitive payment link on the spot.
They then send this link to the customer via SMS or email. The customer clicks it on their smartphone, opening a secure, branded payment page where they can enter their card details privately.
The agent can usually track the payment status on their screen in real-time and confirm once it's done, all while staying on the line to help if needed.
The Virtual Terminal Approach
Think of a virtual terminal as a web-based credit card machine. Your agent logs into a secure website and manually types in the card details as the customer reads them out over the phone.
While this method has been around for years, it carries the highest level of risk and the biggest PCI DSS compliance burden of all the options. Because your agent hears and handles the full card data, your entire contact centre—agents, computers, networks, call recordings, the lot—is dragged into the scope of a PCI DSS audit.
Honestly, you should only even consider this if your transaction volume is incredibly low and you have rock-solid, audited security controls in place. Modern solutions offer far safer and more efficient ways to get the job done.
Comparing the Payment Architectures
Getting to grips with the subtleties of each method is the key to making the right call. It’s usually a balancing act between security, operational cost, and the kind of experience you want to give your customers.
Here's a side-by-side look to help you compare.
Comparing Secure Phone Payment Methods
A side-by-side look at the main approaches for accepting card payments by phone, focusing on security, customer experience, and PCI DSS scope.
| Method | How It Works | Best For | PCI Scope Impact | Customer Experience |
|---|---|---|---|---|
| DTMF Masking | Customer enters card details via keypad; agent hears masked tones. Data goes directly to the payment gateway. | High-touch service, complex sales, and support calls. | Massively Reduced. Card data never enters your environment. | Excellent. Seamless and secure, with a human agent available throughout. |
| Automated IVR | Customer uses a fully automated phone system to make a payment without an agent. | High-volume, routine payments like bill pay or subscription renewals. | Minimal. The system is isolated and managed by a compliant provider. | Good. Convenient for 24/7 self-service but lacks a personal touch. |
| Secure Payment Links | Agent sends a link via SMS/email during the call for the customer to complete payment on their device. | Customers comfortable with mobile payments; businesses with an omnichannel approach. | Reduced. The payment happens outside your systems on a secure webpage. | Very Good. Modern and gives the customer control over data entry. |
| Virtual Terminal | Agent manually types card details read by the customer into a web portal. | Very low-volume merchants with strict internal security controls in place. | Maximum. Puts your entire agent environment and infrastructure in scope. | Average. Relies entirely on the customer's trust in the agent and company. |
In reality, many businesses end up using a mix of these methods. You might use an IVR for after-hours bill payments while your daytime team uses DTMF masking for sales and support. By looking into advanced strategies like channel separation, you can isolate payment traffic even further from your core communications, building a much more secure and compliant setup. This gives you the flexibility to use the perfect tool for every customer interaction.
Getting to Grips with PCI DSS for Phone Payments
When you start to accept card payments over the phone, the Payment Card Industry Data Security Standard (PCI DSS) often feels like the biggest hurdle. But here's the thing: with the right strategy, it's far from insurmountable. Your primary goal should be to shrink your "compliance scope" as much as possible.
Think of your PCI scope as everything in your business—people, technology, processes—that comes into contact with cardholder data. The smaller you can make that footprint, the simpler, cheaper, and less painful compliance becomes. Luckily, modern payment solutions are built to do exactly that.

Shrinking Your Scope: The Smartest Compliance Move
The most effective way to tackle PCI DSS is to stop sensitive card data from ever touching your environment in the first place. It’s a strategy called "de-scoping." When payment details never cross your network, land on your agents' computers, or get captured in call recordings, you essentially remove all those components from your list of compliance worries.
Two brilliant pieces of tech make this a reality for phone payments:
- DTMF (Dual-Tone Multi-Frequency) Masking: This is a genuinely clever fix. It lets a customer type their card numbers into their phone's keypad while on a live call. The system catches these tones before they reach your agent, who just hears a flat, neutral sound. The real data zips straight to the payment gateway, bypassing your business entirely.
- Tokenization: This is another game-changer. It works by swapping a customer's real card number (the PAN) for a unique, non-sensitive stand-in called a "token." You can then use this token for things like recurring billing or refunds without ever exposing the actual card details. Even if a token were stolen, it's completely useless to a fraudster.
Using these tools builds a secure wall between your business and the toxic liability of handling raw card data.
Why Your Call Recording Setup is So Critical
One of the easiest—and most dangerous—mistakes a business can make is accidentally saving card details in its call recordings. PCI DSS Requirement 3.2 is crystal clear: you are strictly forbidden from storing sensitive authentication data after a transaction is authorised. That includes the three or four-digit security code (CVC/CVV).
If your system records a customer reading out their card number, including that CVC code, you've just committed a direct PCI DSS violation. This one slip-up can pull your entire recording system, and maybe your whole network, into the full scope of a PCI audit.
The solution is an automated "pause and resume" feature for your recordings. A truly compliant system will automatically stop recording the second the payment process starts and kick back in the moment it’s done. This guarantees no sensitive data ever gets captured.
For businesses that manage a high volume of transactions, like contact centres, digging deeper into ensuring security compliance in BPOs for standards like PCI DSS can offer invaluable, broader insights.
Finding the Right Self-Assessment Questionnaire (SAQ)
To prove you're compliant, you'll need to fill out a Self-Assessment Questionnaire, or SAQ. The version you use is determined entirely by how you handle card data. By de-scoping your operations, you can radically simplify this task, qualifying for a much shorter and less intense questionnaire.
Here’s a quick rundown of the most common SAQs for businesses taking phone payments:
- SAQ A: This is the holy grail. It's the simplest form, available to businesses that have completely outsourced all cardholder data functions to a PCI-compliant third party. If you're using DTMF masking or a secure IVR, this is what you should be aiming for.
- SAQ A-EP: This is for e-commerce merchants who outsource payments but have a website that could still influence the security of the transaction—for instance, if you send secure payment links to customers during a call.
- SAQ C-VT: This one's for businesses using a virtual terminal on a single, isolated computer to manually key in card details. The rules are tighter because an employee is handling the data directly, which puts their workstation in scope.
- SAQ D: The big one. This is the most detailed and demanding SAQ for everyone who doesn't fit into the other categories. If raw card data touches any part of your network, you'll almost certainly land here, facing hundreds of security controls.
Ultimately, your goal is to put a solution in place that lets you confidently complete SAQ A. With big changes on the horizon, it's also wise to get prepared. Our guide on the https://www.paytia.com/resources/blog/pci-dss-4-0-1-telephone-payments-march-2025-compliance-requirements offers a detailed look at what's coming. By making a strategic choice to de-scope, you can turn PCI DSS from a daunting operational headache into a straightforward, manageable process.
Integrating Systems for Seamless Payment Operations
Putting a secure system in place to accept card payments over the phone is a great first step, but its real value comes alive when it’s properly connected to the other software that runs your business. A standalone payment tool just creates more manual work, disconnected data, and missed opportunities. The goal is true operational efficiency, and that comes from a seamless integration between your payment solution, your phone system, and your Customer Relationship Management (CRM) platform.
This isn't just about keeping the IT department happy; it's about building a smarter, smoother workflow. When these systems talk to each other, a payment's outcome can instantly update a customer’s record. Your agents get a complete picture of every interaction, and your finance team gets accurate data without having to piece together spreadsheets.
Making Your CRM the Central Hub
Your CRM should be the heart of your customer data, and your payment system needs to feed it information without ever putting it at risk. The idea is to post payment outcomes—like "success" or "declined," the transaction amount, and a unique reference ID—directly onto the customer’s record. But here's the crucial part: this has to happen without any sensitive card details ever touching your CRM.
So how does that actually work? When a payment is processed using a de-scoped solution like DTMF masking, the secure platform sends a notification straight back to your CRM through an API. This little packet of data contains only non-sensitive information:
- Customer Identifier: To link the payment to the right person.
- Transaction Status: A simple confirmation of whether the payment went through.
- Payment Token: A secure, non-sensitive reference for any future billing or refunds.
- Amount and Currency: The value of the transaction.
This automated update means your agents don’t have to manually copy and paste payment details, which kills human error and frees up their time. It also gives you a complete audit trail right there in the customer's history.
Connecting with Your Telephony and VoIP Systems
For a method like DTMF masking to work its magic, your payment solution has to be integrated with your phone system. This applies whether you're running a traditional PBX or a modern VoIP platform from providers like RingCentral or 8x8. This integration is what allows the secure technology to sit in the middle of the call.
It intelligently intercepts the audio stream the moment the customer starts keying in their card details. The system captures the DTMF tones, sends them directly to the payment gateway for processing, and completely masks them from your agent's ears and your call recordings. The conversation flows without interruption, making for a much smoother customer experience.
This telephony integration is the technical linchpin of de-scoping your call centre. Without it, you can't prevent card data from flowing through your agents' headsets and into your recording archives, which puts you right back in the middle of a major PCI DSS compliance headache.
Choosing the Right Payment Gateway
Not all payment gateways are built the same, particularly when it comes to phone payments. Your gateway is the final link in the chain, the part that actually gets the transaction authorised with the card networks. When you're picking a provider, you need to be sure it fully supports the features your secure phone payment method relies on.
Here’s a practical checklist to run through:
- Full Tokenization Support: This is a big one. The gateway must be able to create and store tokens, which lets you charge customers again in the future without ever having to handle their raw card details.
- CNP Transaction Features: It should be built for Card-Not-Present (CNP) transactions, offering solid fraud protection tools like AVS (Address Verification Service) and CVV checks.
- Broad Compatibility: Make sure it integrates cleanly with your chosen secure payment platform. Any good provider will have a list of pre-certified gateways they work well with.
- A Flexible API: A powerful and well-documented API is your best friend for building custom workflows and ensuring data passes cleanly between all your systems. If you want to get into the weeds, understanding the details of a payment gateway API integration is time well spent.
A smart integration strategy turns your phone payment channel from a simple transaction tool into a fully connected part of your business, boosting efficiency and security all at once.
Keeping Your Phone Payment Channel Running Smoothly
Getting a secure system in place to accept card payments over the phone is a great first step, but it’s really just the beginning. The true measure of your setup is how you manage it day-to-day. Strong, consistent practices are what will ultimately minimise your risk, keep your operations ticking along nicely, and make sure your customers feel secure every time they call.

The key here is being proactive, not reactive. You need solid fraud controls, a clear playbook for handling disputes, and a constant watch on your performance data.
Fortifying Your Defences Against Fraud
Let's be blunt: Card-Not-Present (CNP) transactions, which include all phone payments, are a prime target for fraudsters. They don't need a physical card, which makes your first line of defence absolutely critical.
Your payment gateway isn't just a tool for taking money; it's your security guard. Make sure it's configured to run these essential checks on every single transaction, without fail:
- Address Verification Service (AVS): This is a basic but powerful check. It compares the billing address the customer gives you with what their bank has on file. A mismatch is a classic red flag.
- Card Verification Value (CVV): Always, always ask for the three or four-digit code on the back of the card. A successful CVV check is a good sign that the person on the phone actually has the card in their hand.
- Transaction Velocity Limits: You need automated rules to spot suspicious patterns. Think about flagging things like multiple payments from the same card in a few minutes, or an unusual number of failed attempts from one caller.
For an even tighter layer of security, you might look into more advanced tools like Voice Biometrics, which can help verify a caller’s identity before a payment is even attempted.
Handling Chargebacks Effectively
Chargebacks are an unfortunate reality when you accept card payments. A customer disputes a charge, their bank reverses it, and you're left to prove the transaction was legitimate. CNP payments are especially vulnerable to "friendly fraud," where a genuine customer simply doesn't recognise a charge on their statement and disputes it.
Your best defence against chargebacks is meticulous record-keeping. Always send a detailed receipt or confirmation email immediately after a successful payment. This document should include your business name, the date, the amount, and a clear description of the goods or services purchased.
When a chargeback notice lands on your desk, act fast. Pull together all the evidence you have—transaction IDs, AVS/CVV results, notes from the call—and submit it promptly. A swift, well-documented response is your best shot at winning the dispute.
Using Reports to Uncover Actionable Insights
Don't let your payment gateway's reporting dashboard gather digital dust. It’s a goldmine of information that can tell you a lot about your customers and your own operations. Regularly reviewing these reports isn't just about balancing the books; it’s a strategic move.
Make a habit of checking these key metrics:
- Authorisation Rates: What percentage of your payments are going through successfully? If this number starts to drop, it could point to a technical issue or a spike in fraud attempts.
- Decline Reasons: Dig into why payments are failing. Are lots of customers getting their expiry date wrong? Are you seeing a high number of "Do Not Honour" messages from banks? This can help you tweak agent scripts or adjust your fraud settings.
- Transaction Volume Trends: Look for patterns. Are you busiest on Monday mornings? Do certain agents process more payments? This data is invaluable for scheduling staff and planning resources.
The context here is crucial. With electronic payments now dominating the market—cash recently dropped below 10% of all payments for the first time, while cards alone made up 64% of transactions—the sheer volume means robust controls are non-negotiable. Consistent management is what transforms your phone payment channel from a simple utility into a secure, efficient, and data-rich asset for your business.
Your Top Questions About Phone Payments Answered
When you start looking into taking payments over the phone, a lot of questions pop up. It's totally normal to wonder about everything from security and costs to how it all works on a daily basis. We’ve been there, so we’ve put together answers to the most common queries we hear.
Getting this right is about more than just ticking a compliance box; it's about creating a payment process that your customers trust and your team finds easy to use.
How Much Does It Really Cost to Take Card Payments by Phone?
There isn't a single price tag, as the costs are usually split into a few different buckets. You're typically looking at a combination of initial setup fees, a monthly subscription for the secure payment technology, and the transaction fees charged by your payment gateway.
Be prepared for phone payment transaction fees—known as Card-Not-Present (CNP) transactions—to be a bit higher than what you'd pay for an in-person sale. The risk of fraud is considered higher when the physical card isn't there, so processors charge a little more. This is usually a small percentage of the transaction value plus a fixed fee.
Often, the biggest factor influencing your total cost is the secure payment platform you choose. A basic virtual terminal might look like the cheap option at first glance, but the hidden "cost" of a huge PCI DSS scope and greater fraud risk can quickly dwarf those initial savings.
If I Use a Third-Party Provider, Am I Off the Hook for PCI Compliance?
Not completely, but it makes a massive difference. Using a secure, specialised provider like Paytia is undoubtedly the best way to tackle compliance, but it doesn’t remove your responsibility entirely. What it does is dramatically reduce your compliance scope.
When you use a solution with DTMF masking or secure payment links, you stop sensitive card data from ever hitting your network. This is a game-changer. It means you can often qualify for the most straightforward PCI DSS validation, the Self-Assessment Questionnaire A (SAQ A), which is far shorter and less complex than the other versions. Your main job is to ensure your chosen provider is compliant, but the heavy lifting is taken off your shoulders.
Can My Agents Just Jot Down Card Details for a Moment?
Absolutely not. This is one of the most critical rules to follow and, unfortunately, one of the most common mistakes. The second an agent writes down card details—even on a sticky note they plan to shred immediately—your entire physical environment, that agent, and all your internal procedures fall under the full, rigorous scope of PCI DSS.
It’s a massive security hole. That little piece of paper can be misplaced, photographed, or stolen, paving the way for a data breach. The core principle of modern phone payment security is simple: your agents should never see, hear, or handle raw card data. Period.
What’s the Safest Way to Take a Card Payment Over the Phone?
The most secure methods are always the ones that completely remove your business from the flow of sensitive data. Two approaches stand out as the industry gold standard:
- DTMF Masking: Your customer types their card numbers into their phone's keypad. The tones are captured before they reach your agent, masked, and sent straight to the payment gateway. Your agent stays on the line, but they hear nothing but flat tones, and nothing is captured by your call recording.
- Secure Payment Links: During the call, your agent sends a unique payment link to the customer via SMS or email. The customer opens it on their smartphone, enters their details on a secure page, and completes the payment themselves.
Both of these methods ensure the full card number (the PAN) and the CVV code never enter your systems, which is exactly where you want to be for maximum security and minimal compliance hassle.
Ready to build a phone payment system that's secure, compliant, and efficient? Paytia offers a suite of solutions, from DTMF masking to secure payment links, designed to protect your business and your customers. Explore our secure payment solutions and see how you can shrink your PCI scope today.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
