
Card Not Present: Essential Guide to Preventing card not present Fraud
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
A card-not-present (or CNP) transaction is simply any payment where you don't physically hand a card over to the merchant. Instead of the familiar swipe, chip-and-pin, or tap, the customer provides their payment details from a distance. It's the engine behind modern e-commerce and any sale made over the phone.
What Are Card Not Present Transactions?

Think about the difference between paying for your weekly shop at the supermarket and ordering a pizza over the phone. At the checkout, the cashier sees your card, and you verify the purchase with your PIN. That’s a Card Present (CP) transaction—secure and straightforward.
But when you read your card number out to the pizza place, they have to take it on faith that you're the real cardholder. There’s no physical proof. That's the essence of a card-not-present transaction.
This distinction is more than just a technicality; it's a massive security issue. The physical card isn’t just a piece of plastic. Its embedded chip creates a unique, encrypted code for that single purchase, making it incredibly tough for fraudsters to copy. CNP payments don't have this physical safeguard. They rely only on the information printed on the card—the very details that get stolen in data breaches and phishing attacks.
Common Channels for CNP Payments
While online shopping is the most obvious example, card-not-present payments happen all the time across a few key channels. Each one has its own quirks and risks for businesses to manage.
- Online E-commerce: This is the big one. Customers type their card number, expiry date, and CVV code into a website's checkout page.
- Phone Orders (MOTO): Short for Mail Order/Telephone Order, this is when a customer gives their card details verbally to a contact centre agent or salesperson.
- Digital Chat and Messaging: A fast-growing channel where customers pay through web chats, SMS, or social media, usually by clicking a secure payment link.
Across every channel, the fundamental problem is the same: the business has to trust the person providing the details without any physical proof. This built-in vulnerability is precisely why CNP fraud makes up the lion's share of card fraud losses worldwide.
This pivot from physical to digital verification completely changes the risk game for merchants. The table below breaks down the key differences between the two transaction types.
Card Present vs Card Not Present at a Glance
| Feature | Card Present (CP) | Card Not Present (CNP) |
|---|---|---|
| Verification Method | Physical chip, PIN, signature | Card number, expiry date, CVV |
| Physical Card | Required and present | Not required or present |
| Fraud Risk | Lower | Significantly higher |
| Typical Environment | Retail stores, restaurants | Online stores, contact centres |
Why CNP Fraud Is a Growing Threat to Your Business

The convenience of digital and remote payments is undeniable, but it's brought a serious and fast-growing danger right to the doorstep of businesses everywhere. When a transaction is card not present, the physical security checks we take for granted—like chip-and-PIN—are completely off the table. This creates a golden opportunity for criminals.
They don't need to physically steal a card anymore. All they need is the information printed on it.
And getting that information is disturbingly simple. Fraudsters can buy huge lists of stolen card details on the dark web, often scooped up from massive data breaches. They also use clever phishing scams to trick people into giving up their financial details directly.
The Anatomy of a CNP Fraud Scheme
Once a fraudster gets their hands on a set of card details—the 16-digit number, expiry date, and the CVV code—they can easily pretend to be the genuine cardholder. Since a card not present transaction only needs this basic info for approval, a criminal can start making purchases online or over the phone with very little to stop them.
Think about it: a fraudster uses stolen details to buy a few expensive, easy-to-sell laptops from your online shop. To your payment system, everything looks fine. The transaction goes through. But sooner or later, the real cardholder will spot the charge on their statement and report it to their bank.
This is where the real headache starts for you. The bank triggers a chargeback, which yanks the funds straight back out of your account. Not only have you lost the money from the sale and the goods you shipped, but you also get slapped with a chargeback fee for your trouble.
"In the event of Card Not Present fraud, it is the merchant who bears the financial loss. This impact can be particularly substantial for retail establishments with narrower profit margins."
It’s a harsh reality. Unlike fraud with a physical card, where the bank often takes the hit, the liability for fraudulent CNP transactions nearly always lands squarely on the merchant.
The Staggering Financial Impact
This isn't just a small cost of doing business; it’s a major threat to your bottom line that's getting worse. As e-commerce and remote payments grow, so does the scale of CNP fraud. The financial fallout is becoming more and more severe, especially in digitally-focused economies.
Take the UK, for example. Card-Not-Present (CNP) fraud is now the biggest payment threat, accounting for roughly 70% of all card fraud losses. In 2024, these losses hit record highs, jumping 11% from the previous year and putting the UK at the top of the European leaderboard for CNP fraud. You can get more detail on this worrying trend from FICO's European Fraud Map analysis.
More Than Just Money Is at Stake
The damage from CNP fraud goes well beyond the immediate financial loss. Every incident eats away at something far more precious: your reputation and the trust your customers place in you.
Here’s a look at the hidden costs that start to pile up:
- Eroded Customer Trust: A customer who gets hit by fraud after buying from you will think twice before doing it again. They’ll worry that their data isn't safe with you.
- Operational Strain: Your team has to waste valuable time and energy investigating and fighting chargebacks, pulling them away from growing the business.
- Higher Processing Fees: Too many chargebacks will get you flagged as a high-risk business. Payment processors can then hit you with higher transaction fees or, in the worst-case scenario, shut down your merchant account entirely.
Ultimately, ignoring the risks of card not present fraud simply isn't an option. It's a direct attack on your revenue, your operational efficiency, and the customer relationships you've worked so hard to build.
Understanding PCI DSS Compliance in CNP Environments
When your business starts accepting card not present payments, you’re stepping into a world governed by some very strict security rules. The big one is the Payment Card Industry Data Security Standard (PCI DSS). This isn't a gentle suggestion; it's a mandatory set of controls for any organisation that handles, processes, or even just comes close to customer card details.
A common mistake is thinking these rules only apply to your website checkout page. In reality, PCI DSS applies everywhere sensitive payment information exists. That definitely includes your contact centre where agents take card details over the phone, and it can even include your web chat logs if customers misguidedly type their card numbers there.
The High Cost of an Expanded Scope
Think of your business operations as a house. Any room where you keep valuables—in this case, sensitive card data—needs a serious, expensive security system. For businesses, this security system is your PCI DSS compliance programme. The more "rooms" (your systems, people, and processes) that touch card data, the larger your security footprint, or PCI scope, becomes.
Outdated card not present payment processes can blow this scope up to an unmanageable size. The moment a call centre agent hears a customer read out their card number, your entire contact centre infrastructure is instantly dragged into scope.
This means everything is now a potential risk:
- Call Recordings: Those audio files now contain highly sensitive authentication data, turning them into a massive liability.
- Agent Desktops: The computers your agents use are now in scope, demanding heavy-duty security controls.
- Network Infrastructure: The parts of your network carrying that voice traffic fall under PCI DSS rules.
- The Agents Themselves: Your own staff become part of the compliance burden, requiring specialised training and background checks.
Expanding your PCI scope is like deciding to store cash in every room of your house. Suddenly, you don't just need a safe in the office; you need reinforced doors, barred windows, and security cameras everywhere. The complexity, cost, and effort for your annual audit just multiplied.
Navigating the Compliance Maze
Achieving and maintaining compliance in such a high-scope environment is a constant headache. It means rigorous annual audits, penetration testing, and meticulous documentation to prove that every single touchpoint is secure. Failing to comply can lead to severe penalties, including eye-watering fines and, in the worst cases, having your ability to process card payments revoked entirely. The principles of securing financial data aren't unique to PCI DSS; they're foundational across many regulations. Exploring broader cybersecurity compliance frameworks like Sarbanes-Oxley (SOX) can offer valuable perspective on these shared security requirements.
This is why modern businesses are flipping the script. Instead of trying to secure a sprawling, ever-expanding environment, they’re laser-focused on shrinking their PCI scope from the get-go. The goal is to stop sensitive card not present data from ever touching their systems in the first place. By implementing technologies that completely isolate the payment process, you effectively remove the "valuables" from most of your operational "rooms." You can learn more about this approach by exploring solutions for achieving PCI DSS compliance that slash your risk and audit burden from day one. It’s a proactive strategy that not only simplifies compliance but builds a far stronger, more resilient security posture for your business.
Key Technologies That Secure CNP Payments
Knowing the risks of card-not-present fraud and compliance is one thing. Actually solving the problem requires a specific set of tools.
Fortunately, there’s a whole suite of powerful technologies designed to neutralise these risks by stopping sensitive data from ever entering your business operations in the first place. Instead of trying to build taller walls around your systems, these solutions prevent the valuable data from ever getting inside.
Let's break down the core technologies that form the backbone of modern CNP payment security.
Understanding DTMF Suppression And Masking
When a customer pays over the phone, the biggest risk is an agent hearing—and your call recorder capturing—the raw card numbers. This is where DTMF suppression, often called masking, comes into play. DTMF stands for Dual-Tone Multi-Frequency, which are the unique sounds each key on a telephone keypad makes.
Think of it like this: your agent and customer are talking, but when it’s time to share the card number, the customer steps into a soundproof booth to enter their details privately. All the agent hears is a flat, neutral tone confirming that numbers are being entered. Those sensitive tones are captured and sent straight to the payment processor, completely bypassing your agent's ears and your recording systems.
This single piece of technology is a game-changer for contact centres. It means your call recordings remain free of toxic data, and your agents are never exposed to sensitive information. This dramatically cuts down both internal and external fraud risks. You can get a much deeper look into the mechanics in our guide on .
This flowchart shows exactly how handling card data directly pulls your business systems into PCI scope, driving up risk and compliance costs.
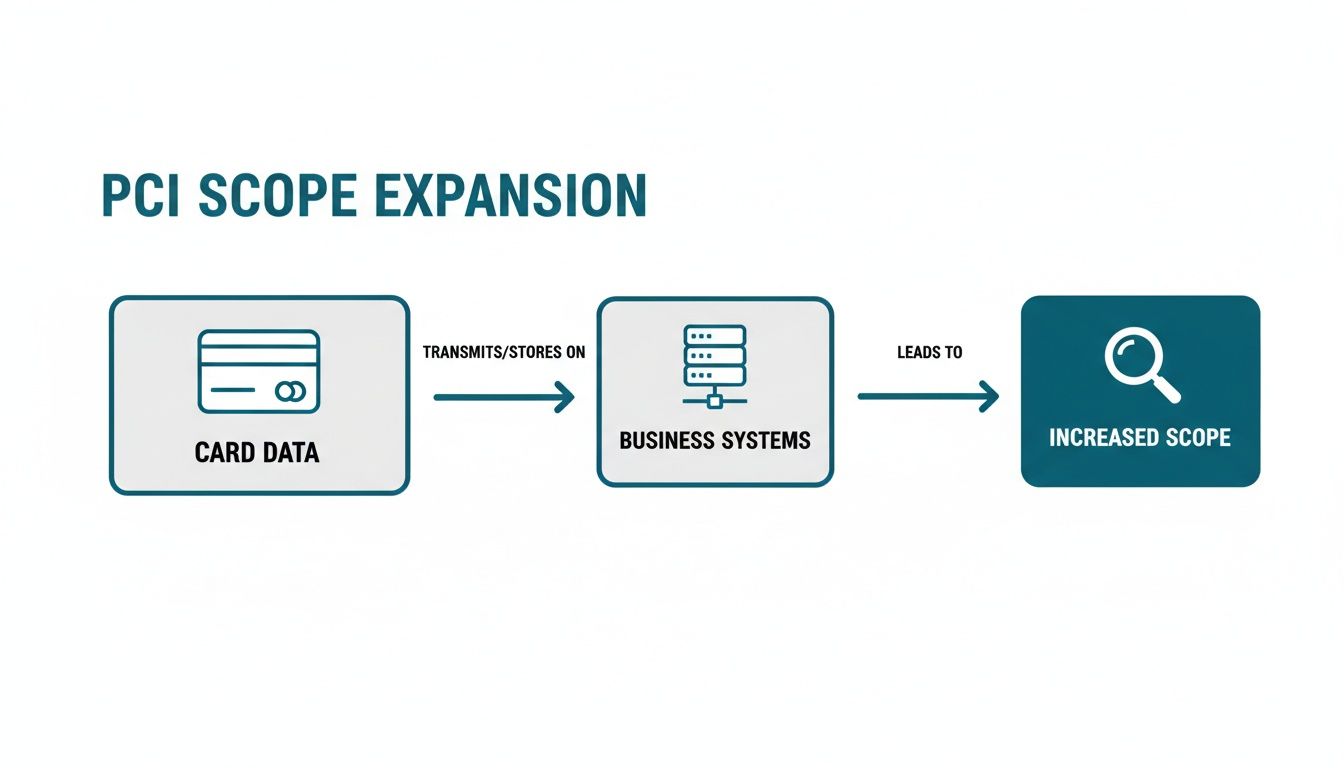
The key takeaway is simple: the moment payment data touches your environment, your compliance burden explodes.
The Power Of Tokenization
Another pillar of CNP security is tokenization. The best analogy is a valet key for a car. You wouldn't hand a valet the master key that can open the boot and glove compartment; you give them a limited-use key that only starts the ignition.
Tokenization works the same way with payment data. When a customer pays for the first time, their actual card number (the Primary Account Number or PAN) is sent to a secure payment vault. In return, the vault sends back a unique, non-sensitive "token"—a random string of characters that acts as a stand-in.
This token can be safely stored in your systems for things like recurring billing or one-click checkouts. If a data breach ever occurs, fraudsters only get the useless tokens, not the actual card numbers that can be used for fraudulent card not present transactions. The real, valuable data remains locked away.
This approach is essential for any business with repeat customers, as it secures future payments without repeatedly exposing sensitive card details.
To help you decide which technology fits your needs, here's a quick comparison of the main security tools available for protecting CNP payments.
Comparing CNP Security Technologies
This table breaks down the core function and primary benefit of each security technology, helping you understand which solution addresses specific risks.
| Technology | How It Works (Analogy) | Primary Security Benefit |
|---|---|---|
| DTMF Suppression | A soundproof booth for keypad tones, blocking agents and recorders from hearing sensitive numbers. | Prevents live agent exposure and keeps card data out of call recordings. |
| Tokenization | A valet key for payment data; a stand-in that works for specific tasks but has no real value if stolen. | Protects stored card data for recurring billing, preventing use if a database is breached. |
| E2EE | An armoured truck that locks the data at the customer's end and only unlocks it at the payment processor. | Secures data in transit across networks, making it unreadable to anyone in the middle. |
| Secure Channels | A dedicated, private tunnel that bypasses your main office systems entirely for payment processing. | Removes your entire business environment from the flow of sensitive data, shrinking PCI scope. |
Each of these technologies plays a crucial role, and the most robust security strategies often combine them to create multiple layers of defence.
Leveraging Secure, Isolated Payment Channels
The most effective strategy brings these technologies together within a secure, isolated payment channel. This approach ensures that from the moment a customer starts to enter their details, the entire process is completely separated from your business's core infrastructure.
Whether it’s over the phone, via a payment link in a web chat, or through an online portal, the customer interacts directly with a secure platform like Paytia. This platform handles the entire transaction—capturing the data, processing it with the bank, and confirming the outcome—all without the data touching your systems.
This method delivers several huge benefits:
- Drastic Scope Reduction: Since your systems never store, process, or transmit cardholder data, your PCI DSS audit scope can be reduced by up to 95%.
- Enhanced Security: By keeping card details out of your environment, you eliminate the primary target for data thieves.
- Improved Trust: Customers feel more secure knowing their information isn't being read aloud or typed into insecure chat windows.
For more advanced protection, businesses are also exploring sophisticated tools outlined in this guide on AI Fraud Detection. By layering these technologies, you can build a resilient defence that protects your revenue, reputation, and customer data from the ever-present threat of card not present fraud.
How to Securely Handle Payments with Remote Teams

For any business with remote teams, especially contact centres, taking a card not present payment can feel like walking a tightrope. The old-school methods of handling these transactions aren't just clunky; they’re a gaping hole in your security and a compliance nightmare waiting to happen.
To really see why a change is needed, it helps to put the old, risky way side-by-side with the modern, secure approach. You'll quickly realise how the right technology doesn't just patch a problem—it completely transforms your operations from high-risk to highly secure.
The Old Way: A Recipe for Disaster
For far too long, the standard way to take a payment over the phone has been dangerously simple. The agent asks the customer to read out their full card number, expiry date, and the three-digit code on the back. Then, the agent types it all into a payment system.
This single, everyday interaction sets off a chain reaction of security risks. Suddenly, that sensitive card data is exposed at multiple points inside your organisation.
- The Agent: Your employee has just seen and heard everything needed to commit fraud. This creates an immediate risk, whether it's malicious or just accidental exposure.
- Call Recordings: Most contact centres record calls for training and quality. But this means you're now storing toxic payment data in your audio files, a direct violation of PCI DSS rules.
- Agent Desktops: The data literally travels through the agent’s computer, pulling their hardware, software, and even the local network into the scope of a PCI audit.
To manage this massive risk, businesses have had to resort to costly and awkward workarounds. Think "clean room" policies, where agents can't have pens, paper, or even their mobile phones at their desks. These measures are a drag on efficiency and foster a culture of mistrust.
The New Way: Secure by Design
Modern payment technology flips this entire process on its head. Instead of pulling sensitive data into your environment, it completely isolates the payment from your infrastructure. This new workflow doesn't just solve the security problem; it makes things better for both the customer and the agent.
So, how does it actually work? When it's time to pay, the agent doesn't ask for any card details. Instead, they kick off a secure, automated process.
- Initiation: The agent lets the customer know that for their security, they'll be prompted to enter their details directly.
- Secure Capture: The customer uses their telephone keypad to type in their card number. DTMF masking technology stops the agent from hearing the tones, replacing them with a flat, neutral sound.
- Direct Processing: The sensitive data travels straight from the customer to the payment processor, completely bypassing the agent, their computer, and all your business systems.
This secure flow can be adapted for any channel. If you're on a web chat, for instance, the agent simply sends a secure payment link. This opens a separate, PCI-compliant page where the customer can complete the transaction on their own.
Comparing Operational Workflows
The difference between these two approaches is night and day. The old way is all about containing risk, while the new way is about eliminating it entirely.
| Aspect | Traditional Method (High Risk) | Modern Method (Low Risk) |
|---|---|---|
| Data Handling | Agent verbally collects and manually types in card details. | Customer enters details directly using their keypad or a secure link. |
| PCI Scope | Drags agents, desktops, call recordings, and your network into scope. | Limited to the secure payment provider; your business stays out of scope. |
| Security Measures | "Clean room" policies and unreliable pause-and-resume recording. | DTMF suppression, tokenization, and end-to-end encryption. |
| Customer Experience | Awkwardly reading sensitive details aloud, which feels insecure. | Smooth, professional, and builds genuine trust with the customer. |
By taking your team and your infrastructure out of the data flow, you make policies like "clean rooms" completely obsolete. This shift does more than just lighten your PCI compliance burden; it lets your team get back to focusing on what they do best—serving customers, not policing desks. Moving to a secure-by-design model for card not present payments is a strategic decision that strengthens security, boosts efficiency, and builds the kind of customer trust that lasts.
How Modern Platforms Slash Your PCI Scope
Bringing in modern security for card-not-present payments isn’t just about adding another tool to your stack. It’s about fundamentally changing your relationship with risk. By using a secure payment platform, you strategically remove sensitive card data from your business environment altogether. The knock-on effect? Your PCI DSS scope shrinks dramatically, and your entire compliance headache gets a whole lot smaller.
Let's go back to our house security analogy. The old way of taking payments is like stashing cash and valuables in every single room. Suddenly, your entire house—from the attic down to the basement—is a high-risk zone that needs expensive alarms, reinforced windows, and constant surveillance. This is exactly what happens when card data touches your agents' screens, your call recordings, and your network.
A modern platform, on the other hand, acts like a secure, off-site vault. When it’s time to get paid, you don’t bring the valuables into your house at all. Instead, they are transported directly and securely to the vault, completely bypassing your property.
Removing the Valuables from Every Room
This is precisely what solutions like Paytia are built to do. They create a secure channel that ensures sensitive cardholder data never even enters your systems in the first place.
- Over the phone: DTMF suppression intercepts keypad tones before they can ever reach your agent or your call recording system.
- Via chat or email: Secure payment links shift the entire transaction over to a dedicated, PCI-compliant payment page.
The result is a huge reduction in your PCI scope. Your call recordings are no longer toxic assets holding sensitive data. Your agent desktops are clean. Your network is out of the firing line. The audit process becomes simpler, faster, and far less expensive because there are simply fewer "rooms" you need to prove are secure.
The core idea is simple but incredibly powerful: you can't lose what you don't have. By preventing card data from ever entering your environment, you eliminate the primary target for criminals and drastically reduce the burden of protecting it.
More Than Just Avoiding Fines
This strategy goes far beyond simply ticking a compliance box. It’s about building a sustainable foundation of trust and security. With card-not-present fraud constantly evolving, a proactive defence is the only one that works.
Recent data really brings home the urgency. In the first half of 2025, UK Finance reported that card-not-present fraud incidents surged by a staggering 22%, making it one of the fastest-growing types of financial crime. This alarming trend shows that criminals are relentlessly targeting remote payment channels, turning robust security from a luxury into a necessity. You can find more details in the UK Finance fraud report.
By implementing a platform that de-scopes your environment, you shield your business from the immense financial and reputational fallout of a data breach. You also create a seamless and reassuring payment journey for your customers, showing them you take their security seriously. Our guide on using payment by link solutions explores one popular method for achieving this.
Ultimately, shrinking your PCI scope isn't just a technical fix—it's a smart, strategic move that strengthens your business from the inside out.
Common Questions About CNP Security
Getting to grips with card not present security always brings up a few practical questions. Let's walk through some of the most common ones we hear from businesses looking to make their payment processes safer.
Does a Secure Payment Platform Get Rid of Our PCI DSS Responsibilities?
Not completely, but it makes a massive difference. While a secure platform like Paytia can slash your PCI DSS scope by as much as 95%, you'll still need to complete an annual Self-Assessment Questionnaire (SAQ).
The good news? That process becomes dramatically simpler, faster, and cheaper. Because your systems no longer touch, store, or see sensitive cardholder data, the scope of your audit shrinks to a fraction of what it was.
How Does DTMF Masking Actually Work on a Live Call?
It's a clever bit of tech that's surprisingly simple in practice. When a customer taps their card details into their telephone keypad, DTMF masking technology steps in and intercepts those tones before they can reach your agent or get picked up by your call recording system.
Your agent just hears a flat, monotone beep to confirm a key was pressed, but the actual sensitive tones are routed directly and securely to the payment processor. This is a game-changer because it means the card data for the card not present transaction never even enters your environment.
Can We Really Take Payments Securely Through Web Chat?
Absolutely. The old way of asking a customer to type their card details into the chat window is a huge security and compliance nightmare. Instead, a modern approach allows an agent to generate and send a secure payment link right in the chat.
The customer clicks the link, which pops open a secure, branded payment page where they can finish the transaction. This keeps all sensitive data completely separate from the chat log and your business systems. It’s a simple switch that turns a high-risk interaction into a completely secure and compliant one.
Ready to take the risk and complexity out of card-not-present payments? See how Paytia can shrink your PCI scope and secure every single transaction. Explore our solutions today.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
