
Securing the Card Not Present Transaction A Complete Guide
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
Whenever a customer pays for something without physically handing over their card, that’s a card-not-present transaction. It’s the engine behind online shopping, phone orders, and subscription payments—basically, any time card details are keyed in remotely instead of being swiped, dipped, or tapped on a machine.
Understanding the Card-Not-Present Transaction Landscape

Welcome to the world of modern business, where the ‘card-not-present’ (or CNP) transaction is king.
Think of it this way: paying in a shop is like giving someone a physical key to unlock a door. A CNP transaction, on the other hand, is like granting secure, one-time digital access without the key ever changing hands. It's this remote approach that has become the default for a huge slice of the global economy, delivering the convenience we all now take for granted.
The Foundation of Modern Commerce
Thanks to the explosion of eCommerce, card-not-present transactions are now far more common than their in-person counterparts. But their reach extends well beyond the online shopping basket. These transactions are the backbone for:
- Subscription Services: From streaming platforms to software-as-a-service (SaaS) products.
- Telephone Payments: Allowing contact centres to take orders, settle bills, and handle donations right over the phone.
- Mobile App Purchases: Fuelling in-app payments for everything from games to groceries.
- Recurring Billing: Automating regular payments for utilities, memberships, and instalment plans without anyone lifting a finger.
This flexibility opens up massive opportunities for businesses to connect with customers anytime, anywhere. But this convenience comes with a trade-off: a unique set of security challenges.
Because the cardholder isn't physically there to be verified, CNP transactions are inherently more vulnerable to fraud. This increased risk is a critical reality for any business that accepts payments remotely.
Getting to grips with the security protocols for a card-not-present transaction isn’t just a good idea—it's non-negotiable. It’s the bedrock on which customer trust is built. Without solid security, businesses aren’t just risking financial loss; they’re risking their reputation. As we’ll explore, taking a proactive approach to securing these payments is fundamental to sustainable growth.
Card Present vs. Card Not Present: A Tale of Two Transactions
To really get a feel for the security gap between different ways of paying, let’s imagine two different customers, Sarah and David. They’re both buying something, but how they pay puts the businesses they’re dealing with in two completely different spots when it comes to risk. Their stories perfectly illustrate why a card not present transaction needs so much more care and attention.
The Card-Present Journey: A Physical Handshake
Sarah is at her favourite high-street shop, buying a new coat. When she gets to the till, she pops her card into the terminal. That one simple action kicks off a whole sequence of physical, hardware-based security checks that happen in the blink of an eye.
First, the terminal reads the card’s embedded EMV microchip—a tiny, secure computer that’s a nightmare for criminals to clone. The machine then asks for her PIN. This is the classic "something you know" security step, a secret code confirming she's the person who rightfully owns the card. The transaction gets the green light in seconds, and Sarah walks out with her new coat.
In this Card Present (CP) world, the security is layered and tangible:
- Physical Card: The actual, real-life card is there.
- EMV Chip: This provides powerful, encrypted data that makes the transaction safe.
- PIN Verification: Sarah’s unique PIN proves it’s really her.
The fraud risk here is incredibly low. A thief would need to have pinched the physical card and somehow know the PIN to pull it off. This visible, robust security gives the shop and its bank a huge amount of confidence.
The Card-Not-Present Journey: A Conversation of Trust
Meanwhile, David is on the phone with his insurance provider to renew his policy. He’s not standing in front of a card machine; instead, he’s reading his card details out loud to a contact centre agent. This is a textbook card not present transaction.
The agent types the details into their system: the long card number, the expiry date, and the three-digit CVV code from the back. To add a bit more security, they might also ask for his billing postcode to run an Address Verification Service (AVS) check.
Unlike Sarah's straightforward purchase, David's entire transaction relies on bits of information that can be easily stolen in a data breach or a phishing attack. There's no physical card, no chip, and no PIN. The business has to trust that the data being provided is genuine. This total reliance on sensitive information is exactly what makes CNP payments such a juicy target for fraudsters.
Because the merchant can’t physically check the card or the person holding it, the liability for any fraud nearly always lands on the business, not the bank. This shift in responsibility is one of the biggest financial risks of taking CNP payments.
This built-in vulnerability is also why payment processors charge higher fees for every card not present transaction—they're baking in the cost of covering the much higher risk of fraud and chargebacks.
Key Differences Between Card Present and Card Not Present Transactions
The gap between these two worlds—in terms of both risk and cost—is massive. For any business leader or contact centre manager, understanding these differences isn't just a technical detail; it's fundamental to protecting your revenue and your customers.
Let's break it down side-by-side.
| Feature | Card Present (CP) Transaction | Card Not Present (CNP) Transaction |
|---|---|---|
| Verification Method | EMV chip and PIN, physical card inspection | CVV, Address Verification Service (AVS) |
| Fraud Risk Level | Very low | High |
| Liability for Fraud | Typically rests with the card-issuing bank | Typically rests with the merchant |
| Processing Fees | Lower | Higher |
| Core Principle | Authenticating the physical card and the person | Authenticating data provided from a distance |
When you boil it down, Sarah’s transaction was like showing her passport at a border control desk—a clear, physical check. David’s was more like trying to verify someone’s identity over the phone using only the details written on their passport, without ever seeing the document or the person. This is why securing the card not present transaction isn’t just a good idea; it’s a critical business priority.
The Escalating Threat of Card-Not-Present Fraud
The sheer convenience of a card-not-present transaction comes with a heavy price: it’s an open invitation for fraud. When you remove the physical card and its owner from the equation, remote payments become a soft target for criminals. This isn't just a small headache; it's arguably the single biggest security challenge for any business that takes payments online or over the phone.
The scale of the problem is genuinely staggering. Back in 2022, card-not-present fraud was responsible for a massive 81% of all UK card fraud cases, with losses hitting £396 million. That figure alone shows just how vulnerable these payment channels are. Fraudsters have become incredibly adept at exploiting stolen card details, and while banks are fighting back, the sheer volume of attacks means businesses are often left on the financial front line.
The Anatomy of a CNP Fraud Attack
Fraudsters don't just get lucky; they run a well-oiled machine. They follow a predictable playbook that starts with getting their hands on payment data and ends with them cashing out. Understanding how they operate is the first step to shutting them down.
It all begins with data acquisition. Criminals use a few common tactics to harvest sensitive card information:
- Phishing Schemes: Deceptively clever emails or text messages designed to trick people into entering their card details on a fake website.
- Data Breaches: Large-scale hacks on company databases that can expose millions of customer records at once, including payment info.
- Social Engineering: Manipulating employees—often in contact centres—to bend the rules or bypass security protocols, giving them access to sensitive data.
Once they’ve got the card number, expiry date, and CVV code, the real damage begins. A fraudster will often ‘test’ the card with a small, insignificant purchase just to see if it’s active. If that goes through, they’ll quickly move on to much larger transactions, typically buying high-value goods they can easily sell for cash.
This flow chart perfectly illustrates the security gap between taking a payment in person versus remotely, highlighting exactly why CNP channels are so much more exposed to these kinds of attacks.
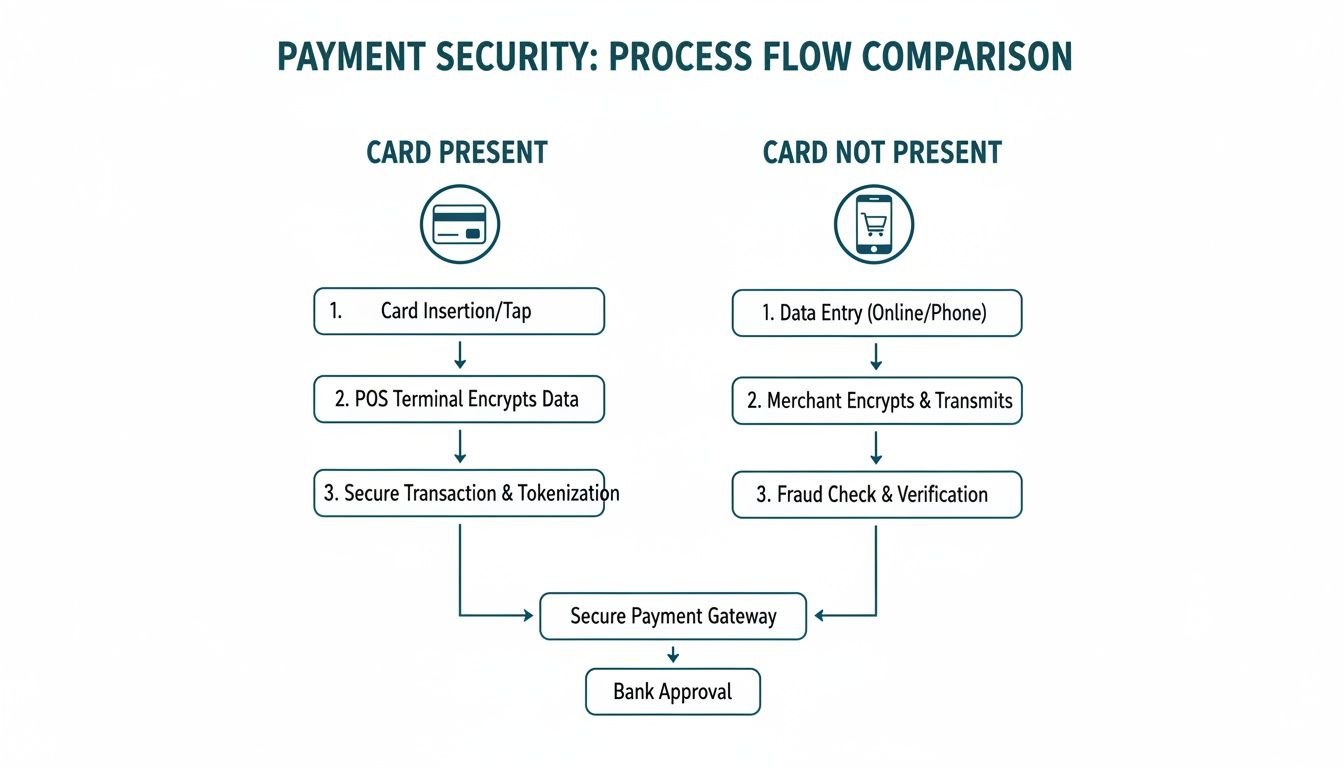
You can see the stark contrast between the robust, multi-layered security of an in-person payment and the purely data-reliant nature of a remote one.
The Ripple Effect on Your Business
The impact of CNP fraud goes way beyond the loss from a single bogus transaction. It kicks off a damaging ripple effect that can strain your operations, drain your resources, and tarnish your reputation for years to come.
A single fraudulent transaction is never just one loss. It's the start of a costly chain reaction involving chargeback fees, operational headaches, and the slow erosion of customer trust that is incredibly difficult to win back.
The first, most immediate hit is the chargeback. When the real cardholder spots the fraudulent charge, their bank will reverse the payment. Because the merchant is held liable in a card-not-present transaction, you’re left out of pocket for the sale, you've lost the goods you shipped, and you get slapped with an extra chargeback fee from your payment processor.
But the pain doesn’t stop there. Your business will also have to deal with:
- Operational Strain: Your team has to burn valuable time investigating fraudulent claims and navigating the complicated chargeback dispute process.
- Reputational Damage: A customer who experiences fraud after buying from you will lose faith in your security. They’ll likely share that negative experience, scaring away potential new customers.
- Increased Scrutiny: A high chargeback rate can get your business flagged as high-risk by payment processors, leading to higher fees or, in the worst-case scenario, the termination of your merchant account.
For contact centres handling MOTO (Mail Order/Telephone Order) payments, these risks are even more pronounced. You can learn more about these specific challenges in our in-depth guide on MOTO payments. Ultimately, ignoring CNP fraud doesn’t just cost you money; it chips away at the trust your business is built on.
Navigating PCI DSS Compliance for CNP Payments
For any business taking a card not present transaction, compliance is much more than a regulatory box-ticking exercise. It's the very bedrock of customer trust. The rulebook we all have to follow is the Payment Card Industry Data Security Standard (PCI DSS), a set of non-negotiable requirements built to keep sensitive cardholder data safe from criminals.
To make this simple, think of your business as a large building. PCI DSS provides the blueprints for a high-security bank vault inside it. The part of your business that has to follow these incredibly strict rules is what we call your PCI scope.
Everything and everyone inside that vault—your people, computers, phone lines, and software—must meet the highest security standards. As you can imagine, building and maintaining that vault gets very expensive and complicated, very fast.
The Problem with Traditional Phone Payments
So what happens when a customer reads their card details out loud to one of your contact centre agents? You’ve just created a huge security headache.
In an instant, the agent, their computer, the call recording system, and probably the entire office network are all exposed to live payment card data. In our analogy, that one phone call has just dragged the entire contact centre inside that high-security vault.
This massively expands your PCI scope, creating an enormous operational burden. To stay compliant, you’d be forced to implement a whole range of expensive and disruptive controls:
- Secure Agent Desktops: Every computer must be locked down tight, preventing agents from installing unauthorised software or even using copy and paste.
- Call Recording Management: You have two bad options: either stop recording calls during payment (a clunky process called 'pause-and-resume') or buy expensive tech to blank out the card numbers from the audio files.
- Continuous Staff Training: Agents need constant training on security protocols and are often subjected to background checks and intense monitoring.
- Network Segmentation: Your IT team faces the complex task of building digital walls to isolate the contact centre network from the rest of the business.
Understanding the True Cost of a Wide Scope
The price of this expanded scope isn't just measured in pounds and pence. It grinds operations to a halt, slows down customer service, and puts a heavy compliance weight on your team. Managing this environment is a constant battle against both external threats and the simple risk of human error.
The larger your PCI scope, the greater your risk of a data breach and the higher the cost of maintaining compliance. Traditional methods of taking a card not present transaction over the phone maximise this scope, making security both expensive and incredibly difficult to manage effectively.
This is the core operational pain that so many businesses live with. They're forced to treat their entire payment environment like a fortress, all because sensitive data is allowed to enter it in the first place. This approach is not only inefficient but also increasingly out of step with modern security solutions.
A Smarter Path to Compliance
The real goal of modern payment security isn't just to build a bigger fortress. It's to drastically shrink—or 'de-scope'—your environment from these strict PCI DSS rules altogether.
By using technologies that stop agents from ever seeing, hearing, or touching cardholder data, you can effectively shrink your high-security vault down to almost nothing. This doesn't just make compliance easier; it makes your business genuinely more secure. For a deeper dive into the specific controls, you can explore our practical guide to PCI DSS requirements.
This shift in strategy is fundamental to protecting your business and your customers in a world now dominated by CNP payments.
Modern Solutions That Secure Every CNP Transaction

The immense compliance burden of a wide PCI scope forces a critical question: what if sensitive card data never entered your business environment in the first place?
That’s the core principle behind modern security solutions designed to protect every card-not-present transaction. Instead of trying to fortify your entire contact centre, these technologies build a shield around your operations, ensuring payment details bypass your systems completely.
This approach is all about ‘de-scoping’ your business from the most demanding PCI DSS requirements. By preventing your people, technology, and recordings from ever seeing, hearing, or storing cardholder information, you effectively shrink your security responsibilities down to almost nothing. The goal is to make top-tier security the default, not an expensive, complicated add-on.
Let’s explore the game-changing technologies that make this a reality.
Dual-Tone Multi-Frequency (DTMF) Suppression
Imagine a phone conversation where anytime someone says a sensitive word, it’s automatically bleeped out, just like on television. That’s the simple but brilliant idea behind DTMF suppression.
When a customer needs to pay over the phone, they use their keypad to enter their card numbers. DTMF suppression intercepts these tones before they can reach the agent or your call recording system. The agent stays on the line to guide the customer, but all they hear is a flat, monotonous tone instead of the distinct beeps that correspond to card numbers. The actual data is sent directly and securely to the payment processor, completely bypassing your infrastructure.
This powerful method achieves several key goals:
- Protects Call Recordings: No card data is ever captured, getting rid of clunky and unreliable pause-and-resume systems for good.
- Secures the Agent Environment: Your staff never hear the card details, removing the risk of both malicious and accidental data exposure.
- Maintains Customer Experience: The agent remains on the line throughout the payment, providing support without interruption.
Payment Tokenization
If DTMF suppression is like bleeping out sensitive words, then tokenization is like using a secret code. It works by replacing a customer's actual Primary Account Number (PAN) with a unique, non-sensitive placeholder called a 'token'.
Think of it as a secure valet ticket for your payment data. You hand over your valuable car keys (the card number) and get a simple ticket (the token) in return. That ticket is useless to anyone else, but the valet (your payment processor) knows exactly which car it belongs to.
You can then safely store this token in your systems for things like recurring billing or managing customer accounts. Even if a data breach happened, thieves would only get a handful of worthless tokens. The actual card details are locked away securely by the payment gateway.
This process dramatically reduces your risk and compliance scope because you are no longer storing the raw, sensitive data that PCI DSS is designed to protect.
Putting It All Together in Modern Payment Flows
These foundational technologies are woven into a variety of modern solutions that make securing a card-not-present transaction both simple and highly effective. They adapt to how your customers want to pay, providing a secure pathway in any channel.
For example, modern solutions go beyond just fraud detection. They include robust systems for preventing unauthorized transactions through OTP protection, which is particularly vital in fighting phone-based scams.
These secure payment flows typically include:
- Secure Interactive Voice Response (IVR) Systems: Automated, 24/7 payment lines where customers can pay bills using their phone keypad without ever speaking to an agent. This is perfect for high-volume, routine payments.
- Payment Links for Web Chat and SMS: Agents generate a unique, secure payment link and send it to the customer via chat or text. The customer clicks the link, enters their details on a secure page, and the agent receives a real-time payment confirmation. You can learn more about how Paytia’s secure payment links streamline this process.
- Agent-Assisted Payment Capture: This combines the security of DTMF suppression with a human touch. The agent guides the customer through the payment process on the phone, ensuring a smooth and supportive experience while the technology handles all the security in the background.
Platforms like Paytia are engineered specifically to deliver these outcomes. By integrating these de-scoping technologies into a single, seamless solution, they remove the complexity and cost of PCI DSS compliance. This lets you focus on what you do best—serving your customers—not managing a security fortress.
How to Reduce PCI Scope and Protect Your Business
Connecting security technology to real business results is where the magic happens. Think about a contact centre bogged down by a massive PCI scope, clunky manual processes, and the constant worry of fraud. Now, imagine that same operation running securely, compliantly, and efficiently.
This isn't just a hypothetical. You can achieve this by fundamentally changing how you handle a card-not-present transaction.
The trick is to stop sensitive payment data from ever touching your environment in the first place. By using solutions with channel separation technology, you can slash your PCI DSS scope—often by as much as 95%. This approach walls off the payment process from your agents, your systems, and even your call recordings, drastically shrinking your security headache.
From High Risk to High Efficiency
For businesses in sectors like insurance, utilities, and non-profits, this shift brings powerful, tangible benefits. It’s not just about ticking compliance boxes; it’s about building a smarter, safer way to work.
Seamless integration with your existing CRM and payment gateways is key. The right solution should slot into your current setup, not demand a complete, painful overhaul. This means you can get top-tier security without disruptive projects or weeks of agent retraining.
The results speak for themselves:
- Dramatically lower compliance costs: When you shrink your PCI scope, you get to ditch expensive security measures like call recording redaction and locked-down agent desktops.
- Stronger customer trust: Customers feel more confident when they know their data is safe. That confidence builds loyalty and strengthens your brand.
- Streamlined payment processes: Agents can guide customers through payments professionally and smoothly without ever seeing or hearing sensitive information, which makes everything more efficient.
Facing the Reality of Rising Fraud
Taking a proactive stance on security has never been more critical, especially in the UK. The latest figures show a worrying 22% jump in card-not-present fraud, with criminals pocketing over £600 million in the first half of 2025 alone. This surge underscores the huge risks lurking in remote channels like phone and web chat, where fraudsters can easily impersonate legitimate customers. You can dig deeper into these trends on the official UK Finance website.
The ultimate goal is to make PCI DSS Level 1 compliance a straightforward and cost-effective part of your business operations, not an ongoing source of stress and expense. By de-scoping your environment, you move from a defensive position to one of control.
Modern platforms tackle these threats head-on with end-to-end encryption and clever solutions like Identity Verified Pay by Bank, which uses open banking to automate collections without the usual fraud risks. This lets you secure every single card-not-present transaction, protect your reputation, and get back to focusing on growing your business.
Common Questions About Card Not Present Transactions
When you're dealing with CNP payments, a few questions always seem to pop up around security, compliance, and just the day-to-day running of things. Getting straight answers is key to protecting your business and making smart choices about how you handle payments.
Here are some of the most common queries we hear.
What's the Difference Between CNP Fraud and a Chargeback?
It's easy to get these two mixed up, but they're not the same thing.
Think of CNP fraud as the crime itself—it's the illegal, unauthorised use of someone's stolen card details to buy something. A chargeback, on the other hand, is the result. It’s the formal process where a cardholder’s bank reverses a transaction.
While fraud is a huge reason for chargebacks, they can also happen for other reasons, like a customer disputing a legitimate charge (sometimes called "friendly fraud") or being unhappy with a service. The better your security is, the stronger your proof that a transaction was genuinely authorised, which helps you fight off fraud-related chargebacks.
Tough economic times often make things worse. The latest UK card data reveals a worrying trend: credit card balances are on the rise while spending is down. This creates a perfect storm for scammers, leading to more disputes and, ultimately, more chargebacks. This toxic environment was a major factor in the £572.6 million lost to card fraud in the UK in 2024, with the vast majority coming from remote CNP attacks. You can get more detail on these trends from FICO's analysis of UK card data.
Can We Still Record Calls While Taking Secure Payments?
Absolutely, and you should. Modern secure payment platforms are built for this exact scenario. They use clever tech like DTMF masking (or suppression) to ensure that when a customer types in their card details on their keypad, those sensitive numbers never actually enter the call audio or your systems.
This means you can keep recording your calls for quality control and training, confident that you’re not accidentally capturing any cardholder data. It’s the best of both worlds: you get your valuable recordings, and you stay fully compliant with PCI DSS rules.
How Difficult Is It to Integrate a Secure Payment Solution?
You’d be surprised how straightforward it can be. The best platforms are designed to slot into your existing setup with minimal fuss.
Many come with pre-built integrations for the big-name telephony systems, CRMs, and payment gateways. They're built with an API-first mindset, which basically means they're designed to connect to other software easily. This approach minimises disruption, allowing your team to start processing secure payments quickly, often without having to change their daily workflows much at all.
By taking card details completely out of your environment, a dedicated platform like Paytia helps businesses massively reduce their PCI DSS scope. This not only cuts down on compliance headaches but also slashes fraud risk and builds a huge amount of trust with your customers.
Find out how Paytia can help you protect every single card-not-present transaction.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
