
A Guide to Secure Payment Over The Phone
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
Taking a payment over the phone is simply when a business processes a customer's credit or debit card during a live conversation. For many industries, it’s still the most trusted and direct way to close a sale or resolve an issue, especially when personal interaction is part of the service.
Why Phone Payments Still Matter in a Digital World

With digital wallets and one-click checkouts everywhere, you might think taking payments over the phone is a bit old-fashioned. But the truth is, this direct, human-to-human connection remains a cornerstone of great customer service and a vital revenue stream for countless businesses. Sometimes, an online form just can't replace a real conversation.
Think about businesses built on trust and careful discussion—like settling an insurance claim, paying a complex medical bill, or finalising a big B2B order. A phone call gives customers the reassurance they need to complete a major transaction. That personal touch is often the deciding factor for people who are wary of entering sensitive details online or just need a bit of guidance.
The Human Element in an Automated Age
While the UK has seen a huge shift towards digital payments—digital wallet use jumped from just 14% in 2017 to 47% by 2022—these methods don't fit every scenario. Phone payments fill the gaps perfectly. They’re essential for things like taking an insurance premium from a client who’s on the move or processing tuition fees from a parent who has a few last-minute questions. You can find more details in the UK Finance Payment Markets Report.
At its heart, taking a payment over the phone offers unique value because it can:
- Build Trust: A real conversation with a helpful agent can instantly calm a customer's worries about security.
- Solve Problems Immediately: Agents can answer questions, fix mistakes, and take payment all in one go.
- Cater to Everyone: Not all customers are tech-savvy. The phone is a familiar and accessible alternative for them.
Balancing Convenience with Iron-Clad Security
Here's the big challenge, though. How do you keep that smooth, human-led experience while guaranteeing total security and compliance? An insecure phone payment is like asking a customer to shout their card details across a busy café—it puts sensitive data at serious risk.
The number one job for any business taking phone payments is to keep sensitive cardholder data completely out of its environment. This not only protects the customer but also massively simplifies the organisation's own compliance headaches under the Payment Card Industry Data Security Standard (PCI DSS).
This guide will walk you through how modern technology pulls off this balancing act, making phone payments both secure and brilliantly efficient. We’ll get into the risks, compare the different ways to take payments, and give you a clear plan for implementing a solution that protects your customers and your business. For a wider perspective, feel free to explore other alternative payment methods in our detailed article.
Understanding the Risks of Taking Card Payments by Phone
Taking a card payment over the phone feels simple, but behind that conversation lies a minefield of security risks and regulatory duties. Any business that accepts a payment over the phone must follow a strict set of rules called the Payment Card Industry Data Security Standard (PCI DSS). This isn't just a friendly suggestion; it's a mandatory global standard designed to keep customer data safe.
Ignoring these rules can lead to painful consequences. We're talking about heavy fines, losing the ability to accept card payments altogether, and the kind of brand damage that’s hard to recover from. At the centre of this challenge is a concept known as PCI scope.
Think of your PCI scope as the potential "blast radius" for a data breach in your business. Any person, computer system, or business process that comes into contact with sensitive cardholder data is considered "in scope." The more things you have in scope, the bigger your compliance headache, the higher your costs, and the greater your risk.
Why Outdated Practices Create Major Problems
Old-school methods, like a call centre agent hearing or jotting down a customer's card number, drag your entire contact centre right into the heart of PCI scope. This one act exponentially increases your compliance burden. Suddenly, every agent, every computer, and every call recording system has to meet the tough security controls of PCI DSS.
This traditional approach opens up several gaping vulnerabilities:
- Insecure Call Recordings: If you record calls for training or quality checks, you could be stockpiling thousands of audio files filled with credit card numbers. These recordings are a goldmine for fraudsters.
- Internal Fraud: When agents have direct access to card data, the risk of an employee misusing or stealing that information skyrockets. It only takes one rogue agent to cause a catastrophic breach.
- Unsecured Desktops and Networks: Card details typed into CRM notes or spreadsheets can linger in system memory, log files, or unencrypted network traffic, creating multiple weak spots for an attack.
The core principle of modern payment security is simple: if you don’t need to see, hear, or store sensitive card data, then don't. The most effective way to protect your business is to remove your environment from the flow of this information entirely.
Understanding the Regulatory Maze
The rules don't stop with PCI DSS. To steer clear of legal trouble and maintain customer trust, businesses also need to focus on avoiding Telephone Consumer Protection Act violations when managing phone interactions. While PCI DSS is laser-focused on data security, other regulations govern how you communicate with customers, creating a complex web of duties.
The goal is to build a fortress around customer data without making the payment process a nightmare. For a deeper look into the specific dangers lurking in traditional phone payment methods, you can explore the hidden risks of taking card payments over the phone in our detailed guide.
Ultimately, the risks tied to outdated phone payment practices are too big to ignore. The financial and reputational cost of a data breach can be devastating, especially for small and medium-sized businesses. This is why adopting secure, modern payment technology isn't just a good idea—it's an urgent business priority that turns compliance from a burden into a real strategic advantage.
Choosing the Right Method for Phone Payments
When a customer is ready to pay over the phone, the experience they have can make or break their trust in your business. Not all phone payment methods are created equal, and figuring out the right one really boils down to your specific needs. The three main ways to handle it are agent-assisted payments, fully automated Interactive Voice Response (IVR) systems, and self-service payment links sent during a call.
Each approach strikes a different balance between customer experience, security, and operational efficiency. The trick is to align the technology with what you’re trying to achieve—whether that’s a high-touch, personal service or a lightning-fast, self-serve option for simple transactions.
Agent-Assisted Payments: The Personal Touch
In an agent-assisted model, a customer talks to a live person who guides them through the payment. This method is perfect for complex or high-value sales where a customer might have questions or just need a bit of reassurance. That human element builds confidence and lets your team sort out any issues on the spot.
But here’s the crucial part: to keep the process secure and compliant with PCI DSS, the agent must never hear or see the card details. Modern solutions get this right by letting the customer punch in their card number using their telephone keypad while the agent stays on the line. Technologies like DTMF suppression mask the tones, so the sensitive data travels directly to the payment processor, completely bypassing your environment.
It’s the best of both worlds: the efficiency of technology with the comfort of human support.
Automated IVR Payments: The Efficiency Engine
An Interactive Voice Response (IVR) system gives you a fully automated, 24/7 payment channel with zero agent involvement. Customers call in, follow a menu using their voice or keypad, and enter their payment details to finalise a purchase. This is a brilliant fit for straightforward, recurring payments like utility bills, council tax, or subscription renewals.
The biggest wins with a secure IVR are cost savings and constant availability. It frees up your agents to tackle more complex customer problems, which helps cut down call queues and operational costs. And because the whole thing is automated and secure, it dramatically shrinks your PCI DSS scope.
The choice between an agent and an IVR often comes down to the nature of the transaction. High-value, nuanced sales thrive with a human touch, while simple bill payments are perfectly suited for a fast, efficient automated system.
Self-Service Payment Links: The Modern Hybrid
A third, increasingly popular option involves the agent sending a secure payment link to the customer’s mobile via SMS during a live call. The customer taps the link on their device and completes the payment on a secure, mobile-friendly webpage, all while still talking to the agent.
This approach offers a fantastic middle ground. The customer stays in full control of their card details in a digital interface they know and trust, while the agent is right there to confirm the payment went through and wrap up any final questions. It delivers the modern, user-friendly experience that many customers now expect.
The flowchart below shows how the way you handle card data directly affects your business's PCI compliance scope.
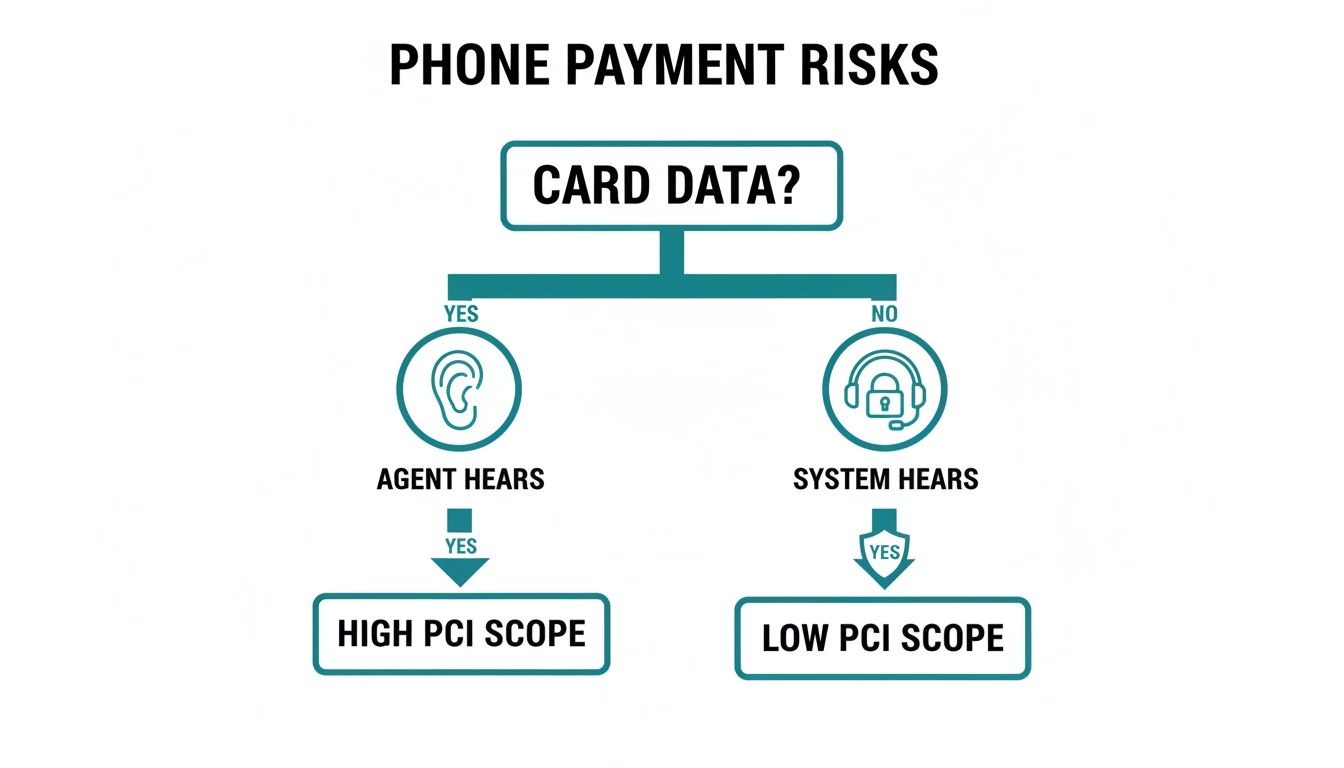
As the diagram makes clear, the moment an agent or an insecure system hears card data, your PCI scope balloons, sending risk and compliance costs through the roof.
Comparing Your Options Side-By-Side
To help you find the best fit, we need to compare these three methods across some key business criteria. Each has its own strengths, depending on what you prioritise.
This table breaks down the core differences to make the decision clearer.
Comparison of Phone Payment Methods
| Method | Best For | Customer Experience | Security Level (with right tech) | Operational Impact |
|---|---|---|---|---|
| Agent-Assisted | Complex sales, technical support, high-value transactions | Personalised and reassuring; builds trust | Very High | Requires agent time but resolves issues in one call |
| Automated IVR | Simple bill payments, account top-ups, routine renewals | Fast and efficient; available 24/7 | Very High | Reduces agent workload and lowers operational costs |
| Self-Service Links | Mobile-savvy customers, quick checkouts during a call | Modern and user-friendly; customer is in control | Very High | Blends agent support with self-service efficiency |
Ultimately, the smartest strategy might be to use a mix of these methods. By offering different ways to complete a payment over the phone, you can meet a wider range of customer preferences while making sure every single transaction is secure, efficient, and compliant.
The Technology That Secures Phone Payments

To make taking a payment over the phone genuinely secure, we can't just cross our fingers and hope for the best. Good intentions and company policies aren't enough. We need solid technology that builds a digital fortress around sensitive card data.
The core technologies work behind the scenes to completely remove your agents—and your company's systems—from the flow of payment information. For many organisations, especially in healthcare, a deep understanding of specialised medical office phone systems is the first step in securely managing both patient calls and financial transactions.
The whole goal is to create a secure bubble where card details are captured without ever being seen, heard, or stored within your business. Let's break down the three pillars that make this happen.
DTMF Suppression: A Digital Soundproof Booth
Imagine your call centre agent is on the line with a customer who’s ready to pay. They need to provide their 16-digit card number, expiry date, and CVC. In an old-school, unsecured setup, the agent would hear every beep as the customer punches the numbers into their keypad. Those tones are called Dual-Tone Multi-Frequency (DTMF) signals, and a savvy fraudster could potentially record and decipher them.
This is where DTMF suppression (or masking) steps in. It’s like building a digital soundproof booth around the transaction, just for a few seconds.
Here's how it unfolds:
- The agent guides the customer to the payment stage and initiates the secure process.
- The customer starts typing their card details using their phone’s keypad.
- The secure payment technology instantly intercepts these DTMF tones before they reach the agent.
- It replaces them with a single, flat, monotone sound, so the agent hears nothing revealing.
- The real card data travels directly to the payment processor through a secure channel, completely bypassing the agent and your call recording systems.
The agent stays on the line the whole time, ready to help, but they are completely deaf and blind to the actual payment details. It’s a simple but powerful way to stop card data from ever touching your business environment. You can learn more by exploring our guide to understanding DTMF masking technology.
Tokenization: Swapping Real Money for Casino Chips
Once the card data is captured, the next layer of security kicks in: tokenization. Think of this clever process as exchanging your cash for chips at a casino.
Inside the casino, those chips have real value. You can use them to play any game you want. But if someone stole them and tried to use them at the corner shop, they’d just be worthless bits of plastic. Tokenization does exactly the same thing for card data.
A payment gateway takes the real card number—the Primary Account Number (PAN)—and swaps it for a unique, randomly generated string of characters called a token. This token can then be stored safely in your systems for things like recurring billing or looking up a customer’s account. If a fraudster ever breached your systems and stole the tokens, they’d be useless.
Tokenization is the ultimate de-risking tool. It allows your business to function—managing subscriptions, processing refunds, and analysing customer behaviour—without the immense liability of storing actual credit card numbers.
End-to-End Encryption: The Sealed Digital Envelope
The final piece of our security puzzle is end-to-end encryption (E2EE). If DTMF suppression is the soundproof booth and tokenization provides the casino chips, then E2EE is the armoured vehicle that transports everything safely.
From the moment a customer types their first digit until the data reaches the payment processor, E2EE wraps it in a protective digital envelope. This encryption scrambles the information, making it completely unreadable to anyone who might try to intercept it along its journey.
Only the authorised payment processor holds the special "key" to unlock this envelope and read the data inside. Even if a cybercriminal managed to intercept the data packet in transit, all they’d see is a meaningless jumble of characters.
Together, these three technologies—DTMF suppression, tokenization, and end-to-end encryption—form a layered defence that makes modern payment over the phone systems incredibly secure. They work in concert to achieve one critical goal: to ensure sensitive cardholder data never touches your organisation's environment.
How to Implement a Secure Phone Payment System
Alright, let's move from theory to practice. Putting a secure system in place for taking a payment over the phone isn't just about buying a piece of software. It’s about finding the right partner and platform that slots neatly into how you already work, while completely overhauling your security posture for the better.
When you get it right, compliance stops being a costly headache and becomes a real business advantage. The aim is to find a system that not only clears today's security hurdles but is also ready for where your business is heading tomorrow. This means digging deeper than just the feature list to check a vendor's certifications, how well their tech plays with others, and the real-world return on investment (ROI) they can actually deliver.
A great implementation should feel less like a massive IT project and more like a smart, seamless upgrade to your operations.
Your Vendor Selection Checklist
Picking the right vendor is easily the most important decision you'll make. This isn't just another supplier; they’re providing a core piece of your security and customer experience. As you weigh up your options, use this checklist to keep you on track.
- PCI DSS Level 1 Certification: This is an absolute must. Any vendor you consider has to be certified as a Level 1 Service Provider. It’s the highest stamp of approval, proving their systems have been through the wringer with rigorous audits to protect cardholder data.
- Seamless Integration Capabilities: The solution has to work with the tools you already rely on. Get confirmation that it connects smoothly with your existing phone system (PBX/VoIP), your contact centre platform (CCaaS), your CRM, and whatever payment gateways you use.
- Comprehensive Security Features: Make sure the platform offers security in layers. You're looking for core technologies like DTMF suppression, end-to-end encryption, and tokenization. These are the building blocks of a system designed to take your business completely out of the path of sensitive data.
- Proven Track Record and Support: Find a vendor who knows your industry and has a history of successful projects to prove it. Don't be shy about asking for case studies or references, and get a feel for how responsive and helpful their support team really is.
A vendor who ticks all these boxes is set to provide a solution that not only works out of the gate but can grow right alongside your business.
Connecting the Technical Dots
A secure payment solution can't be an island. Its real power is unleashed when it integrates cleanly with your existing tech, automating tedious tasks and giving your agents a single, unified screen to work from. The key is making sure it enhances your workflows, rather than throwing a spanner in the works.
This kind of integration unlocks some serious efficiencies. For instance, when a customer calls, the system can automatically pop their record up in your CRM. Once a payment over the phone is successfully processed, the result is logged straight back into the CRM—no manual data entry needed from the agent. This kind of connectivity is crucial for keeping your data accurate and your operations moving quickly.
The true measure of a great implementation is invisibility. The technology should work so smoothly in the background that your agents can focus entirely on the customer, not on the process of taking a payment.
Translating Compliance into Tangible ROI
The single biggest win from a modern phone payment system is the massive reduction in your PCI DSS scope. By making sure sensitive card data never even touches your environment, you can slash your compliance burden by over 90%. This isn't just a number; it translates directly into a measurable return on investment.
Think about all the costs tied to a large PCI scope: pricey annual audits, penetration testing, vulnerability scans, and the countless hours your team sinks into compliance admin. By shrinking that scope, you either eliminate these costs or cut them down dramatically.
This is especially critical in the UK, where phone calls are still a massive part of business, with over 88 million active mobile subscriptions. As payments increasingly happen on mobile, securing those voice transactions is non-negotiable. Solutions like Paytia’s DTMF suppression and automated payment links don’t just eliminate fraud risks—they actually boost payment completion rates, turning a compliance task into a competitive edge. You can find more data on UK mobile usage and trends to see just how important this channel remains.
And the ROI doesn't stop at cost savings. By removing the risk of data breaches and internal fraud, you’re protecting your brand's reputation and earning customer trust. On top of that, a quicker, smoother payment journey makes your agents more efficient and can even lift your successful collection rates, directly boosting your bottom line.
Common Questions About Phone Payments
Even with the best technology, changing how you take a payment over the phone is a big step that naturally comes with a lot of questions. Getting clear, straightforward answers is the only way to move forward with confidence. Here, we'll tackle some of the most common queries we hear from businesses looking to implement and manage secure phone payment systems.
Our goal is to give you practical answers that clarify the nuances of compliance, technology, and customer experience, making sure you’re equipped to make the right call for your business.
Is It Safe and Legal to Take Card Details Over the Phone?
Yes, it’s perfectly legal to take card payments by phone, but it’s only safe if you do it correctly. The crucial difference is in how you handle the card details.
The old way—having an agent listen to, repeat, or type in a customer's card number—is incredibly insecure. This method drags your entire contact centre into the scope of PCI DSS compliance, including your agents, call recordings, and IT systems. That makes audits a nightmare and massively inflates the cost.
Thankfully, modern, secure solutions are built to sidestep this risk entirely.
By using technologies like DTMF masking, your agent and your business environment are completely removed from the flow of sensitive data. The agent never hears, sees, or records the card numbers, which dramatically cuts your risk and proves you're handling customer data responsibly and legally. This is the cornerstone of modern, compliant phone payment processing.
This approach doesn't just secure the transaction; it shrinks your PCI DSS obligations, saving you time, money, and a whole lot of stress.
How Does DTMF Suppression Actually Work?
DTMF (Dual-Tone Multi-Frequency) suppression works by catching the tones a customer makes when they press the keys on their phone. Think of it as a secure filter that switches on the moment payment details are being entered. The whole process is seamless for both the customer and the agent on the line.
Here’s a simple breakdown of how it happens:
- Initiation: The agent stays on the line with the customer to guide them and then kicks off the secure payment process.
- Interception: As the customer types their card number, the technology intercepts the DTMF tones before they ever reach your agent or your call recording system.
- Masking: The system instantly replaces those sensitive tones with a single, flat, monotone sound. All the agent hears is a neutral confirmation beep for each key pressed.
- Secure Transmission: Meanwhile, the actual card data travels directly to the payment gateway through a separate, end-to-end encrypted channel.
It's an elegant process that ensures sensitive information never even touches your business environment. This is hands-down the most effective way to protect customer data and simplify your compliance duties.
What Is the Difference Between IVR and Agent-Assisted Payments?
The main difference between a secure IVR and an agent-assisted payment really comes down to the amount of human interaction. Each one serves a different purpose and is better suited to different customer needs.
An agent-assisted payment combines technology with a personal touch. A live agent is there on the call to guide the customer, answer questions, and offer reassurance. When it's time to pay, the customer uses their keypad, and DTMF suppression technology makes sure the agent is shielded from the sensitive data. This approach is perfect for complex sales, technical support issues, or high-value transactions where building trust is key.
A secure IVR (Interactive Voice Response), on the other hand, is a fully automated system. The customer calls in and follows voice or keypad prompts to pay their bill without ever speaking to a person. It's ideal for straightforward, routine payments like settling a utility bill or topping up an account. The big win here is 24/7 availability, which also frees up your agents to focus on more complex customer problems.
Can I Integrate a Secure Phone Payment Solution with My Existing Systems?
Yes, and you absolutely should. Seamless integration is one of the most critical features of any modern payment solution. Leading platforms are designed from the ground up to connect with the infrastructure you already have, including your PBX/VoIP telephony systems, major contact centre platforms (CCaaS), and CRM software.
This integration is vital for creating a smooth, efficient workflow. For example, it enables features like "screen-popping" a customer's record when they call, giving the agent instant context for the conversation. It also means payment outcomes can be automatically logged straight into the CRM, which gets rid of manual data entry and cuts down on human error.
Better yet, a solution with a robust API (Application Programming Interface) gives you the flexibility to build custom integrations, allowing you to tailor the system to your unique business processes. When it's done right, taking a payment over the phone becomes a natural part of the conversation, not a clunky, disjointed interruption.
Ready to transform your phone payment security and customer experience? Paytia provides a PCI DSS Level 1 certified platform that removes your business from the flow of sensitive data, drastically reducing your compliance scope and costs. Discover how our secure payment solutions can integrate seamlessly with your existing systems today.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
