
A Guide to PCI Compliance Auditing in the UK
Get Compliance Consultation
Ensure your payment processing meets UK regulations with Paytia's compliance experts.
So, what exactly is a PCI compliance audit? Think of it less like a test you can cram for and more like a comprehensive health check for your payment security. It’s a formal, deep-dive review to verify that your business is living and breathing the Payment Card Industry Data Security Standard (PCI DSS).
An auditor will meticulously inspect your systems, policies, and day-to-day procedures to make sure sensitive cardholder data is locked down tight at all times.
Understanding the Purpose of a PCI Compliance Audit

It’s easy to see an audit as just another box to tick, but its real purpose is to safeguard your customers' financial data from theft and fraud. This isn't just about running a technical scan; it's a top-to-bottom validation that proves your organisation can be trusted with highly sensitive information.
The stakes are incredibly high, especially for businesses using the cloud. Applying a strong governance framework is the only way to meet PCI DSS requirements in these complex environments. We dive deeper into this in our guide on Mastering Governance in the Cloud for Secure and Scalable IT. It’s about making security a verifiable reality, not just a promise on a webpage.
Key Players and Core Objectives
The audit is usually run by a Qualified Security Assessor (QSA), an independent expert certified by the PCI Security Standards Council. This third-party pro examines your setup against the 12 core requirements of PCI DSS. The depth of the audit depends on your transaction volume, which slots you into one of four compliance levels.
At its heart, the audit aims to:
- Prevent Data Breaches: The ultimate goal is to find and fix security weak spots before criminals can exploit them.
- Build Customer Trust: Passing an audit shows customers you’re serious about protecting them, which is priceless for brand loyalty.
- Maintain Payment Processing Privileges: Card brands like Visa and Mastercard require compliance. Fail an audit, and you could lose the ability to take card payments altogether.
Why Auditing Is Not Optional
Putting a PCI audit on the back burner is a recipe for disaster. Non-compliance can lead to eye-watering fines, higher transaction fees from your bank, and the kind of reputational damage that’s hard to recover from.
Recent fraud statistics in the UK highlight just how real the threat is. Card-not-present (CNP) fraud—the type that happens over the phone or online—was responsible for over 80% of total card fraud losses, exceeding £0.5 billion in a single 12-month period. This isn't a distant threat; it's happening right here, right now.
A successful PCI compliance audit is more than a certificate for the wall. It's a testament to your organisation's commitment to security. It confirms you have the right people, processes, and technology in place to protect every single transaction.
Ultimately, this formal review is a non-negotiable part of doing business for any UK company that touches card data. It turns security from a theoretical goal into a proven, documented, and constantly monitored reality that protects both your customers and your business.
Navigating the Four Levels of PCI Compliance
Before you can even think about a PCI compliance audit, you need to figure out where your business fits into the bigger picture. It’s a bit like an MOT for a vehicle; a massive lorry needs a far more rigorous inspection than a small family car. In the same way, the intensity of your audit depends entirely on how many card payments you process each year.
The whole system is broken down into four levels. Your level determines everything—from which validation documents you need to fill out, to whether you require a formal, on-site audit by a Qualified Security Assessor (QSA). Getting this first step right is the foundation of a smooth audit process.
Level 1: The Highest Tier
Level 1 is for the big players—we're talking global retailers, major airlines, and large financial institutions that process a staggering number of card transactions. Because they handle such vast quantities of sensitive data, they're considered the highest risk.
As you’d expect, their audit requirements are the toughest. Every Level 1 organisation must undergo an annual Report on Compliance (ROC). This isn't just a box-ticking exercise; it's a formal, on-site audit carried out by an independent QSA who will meticulously check every single applicable PCI DSS control. It’s an exhaustive process that leaves no stone unturned.
Levels 2, 3, and 4
As you move down the tiers, the transaction volumes get smaller, and the auditing requirements become a bit more manageable—though no less important. In the UK, the levels are clearly defined by the number of transactions processed each year.
A business processing over 6 million transactions annually is Level 1 and must have that full ROC. Level 2 merchants, who handle between 1 to 6 million transactions, can often use a Self-Assessment Questionnaire (SAQ) instead. Level 3 covers those processing 20,000 to 1 million transactions, and Level 4 is for businesses with fewer than 20,000 e-commerce transactions or up to 1 million transactions in total.
This tiered approach means smaller businesses have a less daunting path to proving their compliance.
- Level 2: These are typically mid-sized companies that still process a healthy number of payments. While some acquiring banks might still ask for a ROC, most Level 2 merchants can validate their compliance with an SAQ and an Attestation of Compliance (AOC).
- Level 3: Smaller e-commerce shops and independent retailers often fall into this bracket. The standard path here is completing the correct annual SAQ.
- Level 4: This level covers the smallest businesses, like local boutiques or new start-ups. Just like Level 3, they prove their compliance by completing an annual SAQ.
Knowing your level isn't just a formality—it dictates your entire audit strategy. If you get it wrong, you could either end up going through a needlessly complex and costly audit or, worse, fail to meet your actual obligations and put your business at risk.
Here’s a simple table to break it down.
PCI Compliance Levels and Auditing Requirements at a Glance
This table provides a quick summary of the four PCI compliance levels, the transaction volumes that define them, and what’s typically required for annual validation.
| Compliance Level | Annual Transaction Volume | Annual Validation and Auditing Requirements |
|---|---|---|
| Level 1 | Over 6 million transactions | Annual Report on Compliance (ROC) by a Qualified Security Assessor (QSA) |
| Level 2 | 1 million to 6 million transactions | Annual Self-Assessment Questionnaire (SAQ) and Attestation of Compliance (AOC) |
| Level 3 | 20,000 to 1 million transactions | Annual Self-Assessment Questionnaire (SAQ) |
| Level 4 | Fewer than 20,000 e-commerce transactions (or up to 1 million total) | Annual Self-Assessment Questionnaire (SAQ) |
Knowing where you stand allows you to allocate the right resources, set realistic timelines, and approach your PCI audit with confidence.
For a deeper dive into what each level entails, check out our guide on the different PCI levels of compliance.
Preparing for a PCI DSS v4.0 Audit

With PCI DSS v4.0 now in play, the old way of thinking about compliance is over. A PCI compliance audit is no longer a simple box-ticking exercise. Today, auditors dig much deeper to gauge your company’s real-world security maturity and how you actually manage risk.
This shift has really shaken up UK PCI compliance auditing, introducing new controls and deadlines that demand serious preparation. Many of these new requirements become mandatory by 31 March 2025, pushing for continuous risk assessments and much tougher multi-factor authentication (MFA) controls.
To get ready, you need to move away from treating compliance as a periodic event. It's now about maintaining a constant state of security readiness.
Key Controls Under the v4.0 Microscope
Auditors are zeroing in on a few specific areas where security has been beefed up. They want to see proof that your security isn't just a policy gathering dust on a shelf—it needs to be a living, breathing part of your daily operations.
Here’s what they’re looking at closely:
- Stronger Multi-Factor Authentication (MFA): Vague MFA policies just won't cut it anymore. Auditors now expect to see MFA enforced for all access into the cardholder data environment, not just for a handful of users or remote connections.
- Proactive Vulnerability Management: The bar for managing vulnerabilities has been raised. You have to show you're on the front foot, with regular scanning and quick fixes based on clear risk rankings.
- Clear Data Retention and Disposal Policies: Auditors will want to see documented policies that spell out exactly how long you keep sensitive data and—just as importantly—how you securely get rid of it when it’s no longer needed.
When you're pulling everything together for an audit, it's vital to have all your paperwork in order, including proof of secure data destruction. This is where understanding the significance of an HDD destruction certificate becomes critical, as it provides solid evidence that old equipment has been properly dealt with.
Understanding the Customized Approach
One of the headline changes in PCI DSS v4.0 is the customized approach. This gives businesses more flexibility to meet security goals using innovative tech that might not fit neatly into the traditional, prescribed control framework.
But this flexibility comes at a price: a much heavier burden of proof. If you go down this route, you can't just say you meet the requirement. You have to conduct a detailed risk analysis for each custom control and back it up with a mountain of documentation for the auditor.
The customized approach is not an easy way out. It’s designed for mature organisations that live and breathe risk management. You have to prove your unique solution delivers security that's at least as good as the prescribed control.
In short, your team must be ready to defend your security choices with solid evidence and analysis. For most businesses, sticking with the defined, traditional approach is still the most straightforward path to a successful audit.
Gathering the Right Evidence
Under v4.0, auditors expect to see a pile of evidence to support your compliance claims. A big part of your prep work should involve getting these documents organised and ready long before the auditor walks through the door.
Some of the essential pieces of evidence include:
- System Logs and Audit Trails: Be prepared to hand over logs from firewalls, servers, and applications. These need to show your access controls are working as they should and that you're monitoring all activity.
- Documented Policies and Procedures: You’ll need current documentation for everything, from your incident response plan to your security awareness training for staff.
- Vulnerability Scan Reports: Have your latest reports from your Approved Scanning Vendor (ASV) and any internal scans ready to go, along with proof that you've fixed any issues found.
- Proof of Staff Training: Auditors will ask for records showing that every relevant team member has completed their annual security training.
The new standard makes one thing clear: showing your work is just as important as doing it. Good preparation can be the difference between a smooth audit and a stressful, drawn-out nightmare. If your business takes payments over the phone, our detailed guide on the specific PCI DSS v4.0 requirements for March 2025 compliance can help make sure you're fully prepared.
Common Audit Pitfalls and How to Avoid Them
Even the most prepared organisations can get tripped up during a PCI compliance audit. The process is famously detailed, and a few common—and entirely avoidable—mistakes can quickly derail an assessment. The good news is that knowing where others stumble is the first step to making sure your audit goes smoothly.
Many businesses fall into these traps not through a lack of effort, but because of small, overlooked details in their security setup. The trick is to stop thinking reactively and start proactively hunting down these weak spots long before the auditor even books their travel. Let's break down some of the most frequent hurdles.
The Unsegmented Network Trap
One of the single most expensive mistakes we see is the "unsegmented network." Think of your business as a large house and your cardholder data environment (CDE) as a single, high-security safe room. If you don't have proper walls and locked doors separating that room from the rest of the house, an auditor has to inspect the entire property—every room, every cupboard, every window.
In technical terms, this is a flat network. It means the systems handling sensitive card data are sitting on the same network as everyday workstations, office printers, and even the guest Wi-Fi. This blows up your audit scope, pulling nearly your entire infrastructure into the PCI DSS spotlight.
Solution: Get serious about network segmentation. Use firewalls and strict access controls to build a secure, isolated fortress around your CDE. This move alone can drastically shrink the number of systems your auditor needs to look at, saving you an incredible amount of time, money, and headaches.
The Scope Creep Surprise
Another classic pitfall is scope creep that seemingly comes out of nowhere. This usually happens when a new way to take payments is introduced without looping in the compliance team. Maybe marketing launched a new web chat payment feature, or another department started taking payments through a new mobile app they commissioned.
If these new data flows aren't mapped and secured to PCI DSS standards, they create huge blind spots that auditors are trained to find. All of a sudden, systems you thought were completely out of scope are now front and centre, and they are almost guaranteed to be non-compliant.
To dodge this bullet, you need to keep a complete, up-to-date inventory of every single system, app, and process that touches cardholder data. This isn't optional.
- Map Your Data Flows: Create detailed diagrams showing exactly where card data comes in, where it goes, and how it leaves your environment.
- Make it a Habit: Build a PCI compliance check into the lifecycle for any new technology project or business process. No exceptions.
- Use Discovery Tools: Consider using automated tools that can scan your network to find any rogue systems or apps that might be handling card data without anyone knowing.
Neglecting Third-Party Vendor Management
Lots of companies outsource parts of their payment process to third-party vendors, like payment gateways or cloud providers. A huge mistake is just assuming that because the vendor says they are "PCI compliant," you can wash your hands of any responsibility.
That’s a dangerous assumption. At the end of the day, you are still responsible for protecting your customers' data. If your vendor has a security slip-up that affects your data, the liability lands right back on your doorstep. Your auditor will absolutely ask for proof that you're actively managing these relationships.
You have to show your due diligence:
- Verify Their Compliance: Ask for your vendor's Attestation of Compliance (AOC) every single year. This is the proof that they've passed their own PCI audit.
- Define Responsibilities: Get a written agreement that spells out exactly which PCI DSS requirements the vendor handles and which ones are still on you.
- Monitor Their Performance: Don't just "set it and forget it." Keep an eye on your vendor’s security posture to make sure they're holding up their end of the bargain.
By getting ahead of these common tripwires—segmenting your network, locking down your scope, and diligently managing your vendors—you can turn your PCI compliance auditing process from a dreaded ordeal into a straightforward exercise that validates the great security you already have in place.
How Technology Can Reduce Your Audit Scope
Facing a PCI compliance audit can feel a bit like preparing to defend a medieval castle. You've got to secure every single wall, gate, and tower. But what if you could magically shrink that castle down to just one, easy-to-defend room? That’s exactly what scope reduction technology does for your audit.
The idea is simple but incredibly powerful. By using specialised tools, you can stop sensitive cardholder data—like the full card number (PAN) and CVC—from ever touching your business environment in the first place. This strategy is a complete game-changer for the PCI compliance auditing process.
When sensitive data never enters your systems, those systems are no longer considered part of the Cardholder Data Environment (CDE). And if they're not in the CDE, they fall outside the scope of your audit. Simple as that.
Descoping Your Environment with Smart Technology
Two key technologies make this possible: DTMF suppression and tokenization.
Think of DTMF suppression as a clever gatekeeper for your phone payments. When a customer taps their card details into their phone keypad, the technology intercepts these tones before they ever reach your agent or your call recording systems.
Instead of hearing the tell-tale beeps, your agent just sees masked characters (like asterisks) on their screen, confirming the input without ever seeing or hearing the actual card numbers. The sensitive data is channelled directly and securely to the payment gateway, completely bypassing your infrastructure.
Tokenization works in tandem with this. Once the payment gateway authorises the transaction, it sends back a "token"—a secure, randomly generated placeholder that represents the customer's card. You can safely store this token in your CRM or other systems for things like recurring billing, without ever holding the actual card details.
By combining these technologies, you effectively create a secure bubble around the payment process. Your agents, their desktops, your call recordings, and your internal networks never have to store, process, or transmit raw cardholder data.
This approach directly tackles some of the most common and costly audit risks.
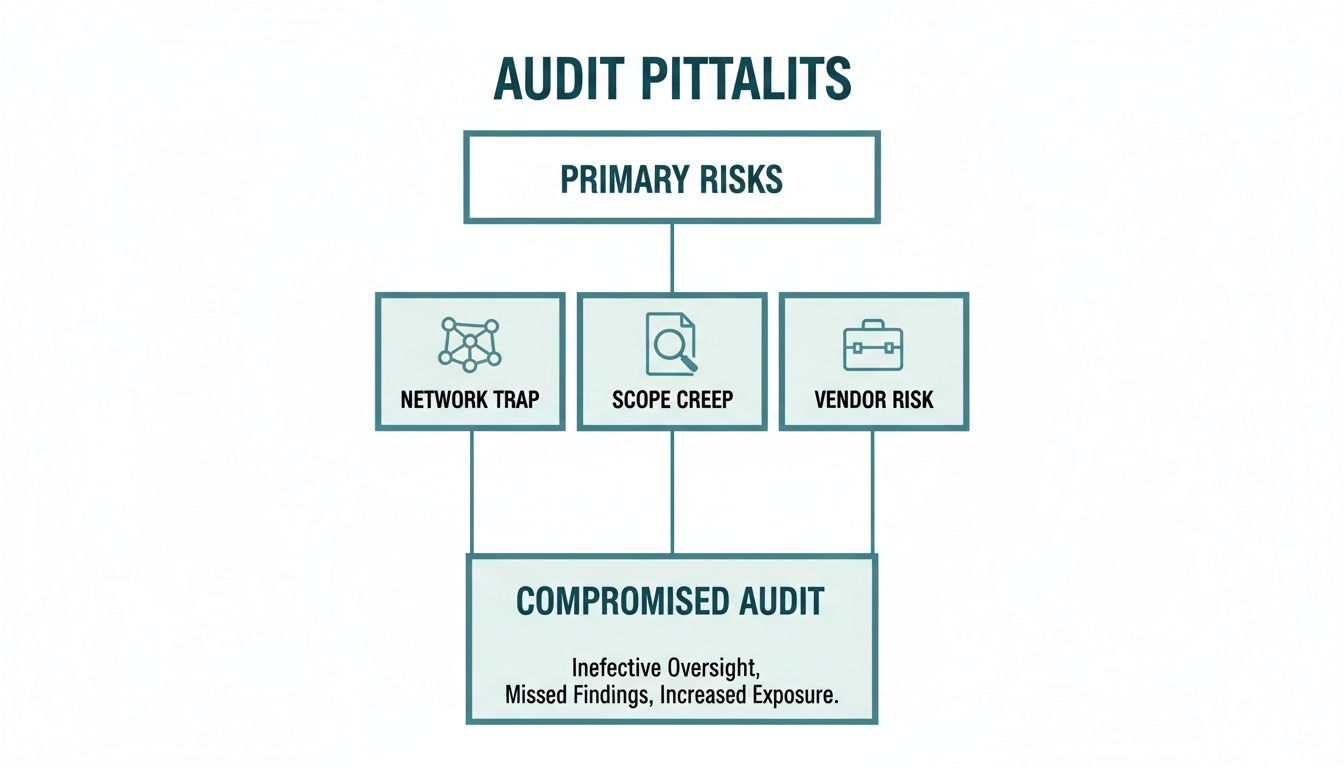
As you can see, risks like an unsegmented network or unexpected scope creep can make an audit spiral out of control. Smart technology helps you get ahead of these problems by keeping card data out from the very start.
The Real-World Impact on Your Audit
The benefits of shrinking your audit scope are massive. For many organisations, especially those with busy contact centres, this approach can reduce PCI DSS responsibilities by up to 95%. This isn't just a minor tweak; it fundamentally changes the entire compliance landscape for your business.
Instead of facing a complex and expensive on-site audit that results in a Report on Compliance (ROC), you may now be eligible to use a much simpler Self-Assessment Questionnaire (SAQ). That shift alone saves an enormous amount of time, money, and stress. Our in-depth guide explains in more detail about how Paytia helps with PCI compliance by implementing these very technologies.
The table below paints a clear before-and-after picture.
Audit Scope Comparison With and Without Scope Reduction Technology
This comparison highlights just how dramatically a descoping solution can cut down the number of systems and processes an auditor needs to examine.
| Audited Area | Without Scope Reduction | With Scope Reduction |
|---|---|---|
| Agent Desktops | In Scope: Requires hardening, monitoring, and regular checks. | Out of Scope: No card data ever touches the desktop. |
| Call Recordings | In Scope: Recordings must be paused or redacted, a complex and risky process. | Out of Scope: DTMF suppression ensures no card data is ever recorded. |
| CRM/Internal Apps | In Scope: If they store card data, they need full PCI controls. | Out of Scope: Only stores useless tokens, not sensitive data. |
| Internal Network | Partially/Fully in Scope: Requires segmentation and constant monitoring. | Largely Out of Scope: Drastically simplified network security requirements. |
By bringing in these technologies, you’re not just preparing for an audit; you're fundamentally redesigning your payment processes to be secure by default. This proactive stance makes the PCI compliance auditing process far less of a headache, turning it into a straightforward validation of a system that is already secure.
Your Audit Readiness Checklist for Phone and Digital Payments
A smooth PCI compliance audit doesn't happen by accident. It's the direct result of careful, methodical preparation, not a last-minute scramble. For any business taking payments over the phone or through digital channels, getting ready means validating every single control and process, piece by piece.
Think of this checklist as your roadmap to facing an audit with confidence. By tackling each point, you can turn what feels like a stressful exam into a straightforward confirmation of your hard work. The aim here is to eliminate surprises—for both you and the auditor.
Phase 1: Scoping and Discovery
Before you can secure anything, you need to know exactly what you’re protecting. This first phase is all about finding every single place cardholder data touches your business. If you miss even one system or data flow, it could lead to an automatic audit failure.
- Map All Data Flows: Get a whiteboard out and draw detailed diagrams. You need to trace the complete journey of cardholder data from the second it enters your business—whether by phone, web chat, or payment link—to the moment it’s gone.
- Identify All In-Scope Systems: Make a full inventory of every piece of hardware, software, and network gear that stores, processes, or transmits cardholder data. This list officially defines your Cardholder Data Environment (CDE).
- Review Third-Party Connections: List every single vendor or service provider that handles card data for you. It's on you to get proof of their PCI DSS compliance and understand exactly how their services affect your audit scope.
Phase 2: Remediation and Hardening
Once you have a clear map of your environment, it's time to plug the gaps. This is the most hands-on part of the process, where you roll up your sleeves and actively strengthen your defences to meet the specific demands of the PCI DSS.
An auditor doesn't just check if a security control exists; they verify that the control is working effectively and consistently. This is where many organisations get caught out—having a policy isn't enough if it isn't being followed.
Now is the time to get things fixed.
- Verify Network Segmentation: Double-check that your firewalls are properly configured to isolate your CDE from the rest of your network. This is one of the most powerful things you can do to reduce the scope and complexity of your audit.
- Conduct Vulnerability Scans: Run both internal and external vulnerability scans using an Approved Scanning Vendor (ASV). You have to fix any high-risk findings and have the clean scan reports ready to hand over.
- Strengthen Access Controls: Go through every user account with a fine-tooth comb. Make sure every employee has only the absolute minimum level of access needed to do their job. Get rid of any old or unnecessary accounts immediately.
Phase 3: Documentation and Evidence Gathering
The final phase is all about proving you've done the work. In the world of auditing, if it isn’t documented, it didn’t happen. You need to gather all your policies, procedures, and system logs to serve as concrete proof that your security measures are in place and working.
- Compile Policy Documents: Pull together all your key security policies, like your main information security policy, your incident response plan, and data retention rules. Check that they are all up-to-date and have been signed off by management.
- Collect System Logs: Gather at least three months of logs from critical systems—think firewalls, servers, and antivirus software. These logs are your proof that you’re actively watching over your environment for any suspicious activity.
- Confirm Staff Training Records: Have records ready that show all relevant staff have completed their annual security awareness training. This is a simple requirement, but it’s one that auditors never forget to check.
Your PCI Compliance Auditing Questions Answered
If you’re wading into the world of PCI compliance audits, you’ve probably got a few questions. It's a complex topic, but the fundamentals are straightforward once you break them down. Here are some clear, direct answers to the questions we hear most often from UK businesses.
How Much Does a PCI Audit Cost?
This is the big one, and the honest answer is: it depends. The cost of a PCI audit can swing wildly depending on your business’s size and how you handle payments.
For a small business that only needs to fill out a Self-Assessment Questionnaire (SAQ), the direct costs might be quite low. But for a larger Level 1 merchant, a formal on-site Report on Compliance (ROC) from a Qualified Security Assessor (QSA) is required. That can easily run from £15,000 to over £50,000 every single year.
And remember, that figure doesn't even touch the internal costs of remediation—the time, effort, and money spent fixing any security gaps the audit uncovers. This is exactly why getting sensitive data out of your environment is so important. It shrinks the audit scope and directly cuts down these expenses.
How Long Does an Audit Take?
Just like cost, the timeline for an audit comes down to two things: your preparation and the scope of your environment. An organised business with a small, well-documented cardholder data environment (CDE) could sail through an audit in just a few weeks.
On the other hand, a large, unprepared company with a sprawling, complex network could be staring down the barrel of a process that takes three to six months, or sometimes even longer. Being proactive isn't just a buzzword here; it’s the secret to a fast, efficient audit.
An important thing to remember is that a PCI audit isn't a one-and-done project. It’s an annual requirement. This makes continuous compliance and a state of constant readiness absolutely essential for long-term security and success.
Do I Still Need an Audit if I Use a Compliant Payment Processor?
Yes, you absolutely do. Using a PCI-compliant payment gateway like Stripe or PayPal is a fantastic first step and it definitely lightens your compliance load, but it doesn't get you off the hook completely.
You are still responsible for securing your own business processes and any systems that touch the payment flow. The way you integrate with that processor determines which SAQ you need to complete, but you're never totally exempt from your PCI DSS duties. At the end of the day, your compliance is always your responsibility.
Take control of your PCI compliance auditing process. Paytia's Secureflow platform removes sensitive payment data from your environment, reducing audit scope by up to 95% and making compliance simpler and more affordable. Learn how we can help at https://www.paytia.com.
Ready to Simplify Compliance?
Get expert guidance on UK payment regulations and PCI DSS compliance. Contact us today.
