
Requirements for pci compliance: A Plain-English Guide
Get Compliance Consultation
Ensure your payment processing meets UK regulations with Paytia's compliance experts.
The core requirements for PCI compliance are a set of 12 security controls laid out by the Payment Card Industry Data Security Standard (PCI DSS). These aren't just suggestions; they are mandatory rules for any organisation that accepts, processes, stores, or transmits credit or debit card information. Their entire purpose is to create a secure environment for handling sensitive payment data.
Understanding Your Core PCI Compliance Requirements
Before we start talking about firewalls and encryption, it's vital to get your head around what PCI compliance actually means for your business. Think of the PCI DSS as the essential security blueprint for a vault holding your customers' most sensitive financial details. Following these rules is non-negotiable and is enforced by the big card brands like Visa and Mastercard.
These standards are built around six foundational security goals, which are then broken down into the 12 specific requirements we'll get into later. The whole framework is designed to build a robust, multi-layered defence against data theft.
The Importance of PCI Scope
One of the most fundamental concepts to understand is PCI scope. This term simply defines which parts of your business—the people, processes, and technologies—come into contact with cardholder data. Anything that falls within this scope must adhere to all 12 PCI DSS requirements.
This is where many businesses get into trouble. An overly broad scope, where payment data touches everything from agent desktops to call recording software, is often the single biggest barrier to achieving compliance. It creates a vast and expensive security perimeter that’s a nightmare to manage and secure.
For UK businesses, these requirements apply universally. You'll be categorised into one of four merchant levels based on your annual transaction volume, which dictates the type of validation needed—from a full-blown audit to a simpler self-assessment. The underlying security controls, however, stay the same for everyone.
The primary goal should always be to minimise your PCI scope. If sensitive data never enters your environment in the first place, you dramatically reduce the complexity, cost, and risk that comes with compliance.
Why Compliance is a Continuous Effort
Achieving compliance isn't a one-and-done project you can tick off a list. It's an ongoing commitment to security. The standards evolve—updates like PCI DSS v4.0 are shifting the focus towards continuous monitoring rather than just passing an annual check-up.
This change reflects the simple reality that security threats are constant, and your defences have to be, too. For a deeper look at the fundamentals, you can learn more about what Payment Card Industry compliance entails and why it's so critical for modern businesses. Successfully managing the requirements for pci compliance is about building a sustainable security culture, not just passing a yearly test.
Breaking Down the 12 Core PCI DSS Requirements
At first glance, the 12 core PCI DSS requirements can feel a bit like reading a dense legal contract. They seem complex, technical, and overwhelming. But they're not. At their heart, they're just a logical set of security practices designed to protect sensitive payment data.
The easiest way to make sense of them is to stop thinking of them as a dry checklist. Instead, group them under their six foundational goals.
Think of it like building a secure vault. You wouldn't just install a heavy door and call it a day. You'd also need reinforced walls, security guards, surveillance cameras, and strict rules for who gets access. Each of the 12 requirements is one of those essential security layers, all working together.
This diagram shows how the entire PCI DSS framework flows from the top down — from the main standard, through the six control objectives, and down to the 12 specific requirements.
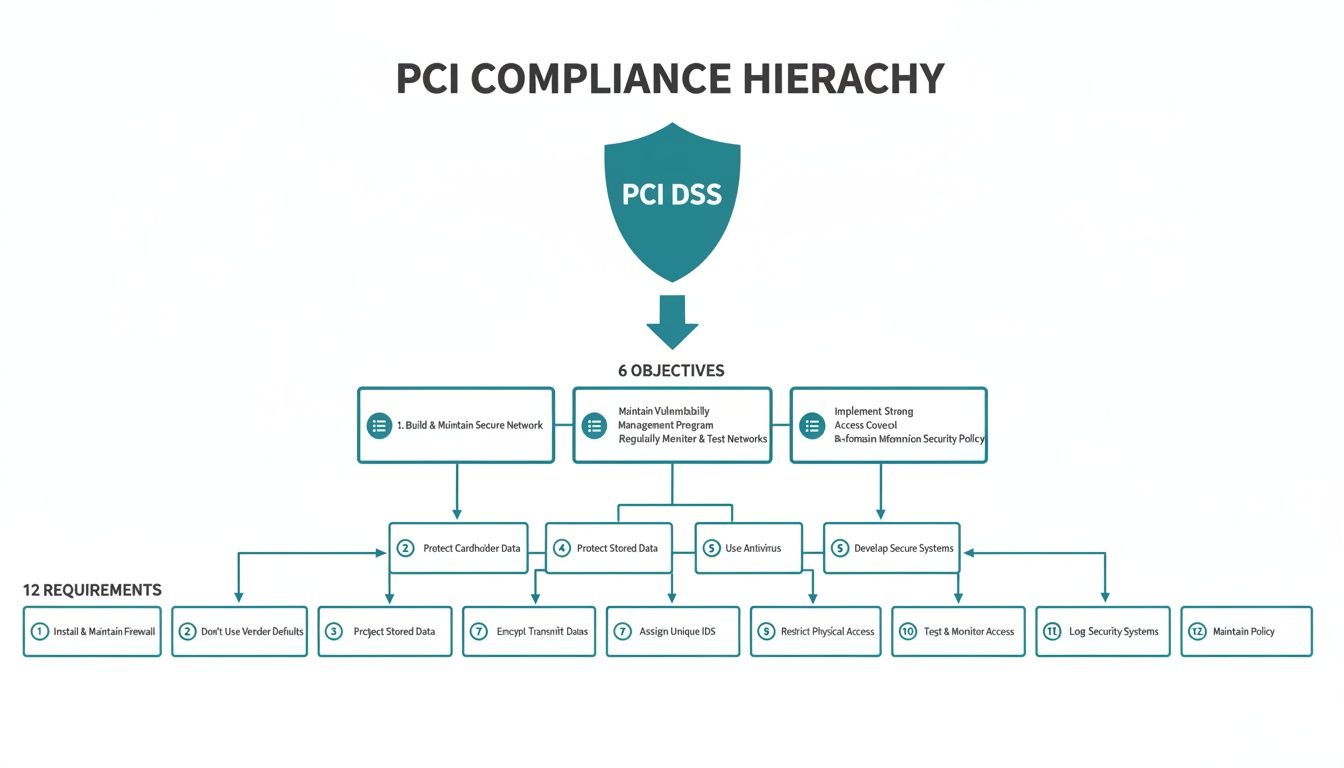
This structure makes it clear that every single requirement serves a higher-level security goal. It’s all about creating a complete, layered defence for your payment systems.
To help you get a quick overview, this table maps the 12 requirements to their corresponding control objectives.
The 12 PCI DSS Requirements at a Glance
| Control Objective | Requirement Number | Requirement Focus |
|---|---|---|
| Build and Maintain a Secure Network and Systems | 1 | Install and Maintain Network Security Controls |
| 2 | Apply Secure Configurations to All System Components | |
| Protect Account Data | 3 | Protect Stored Account Data |
| 4 | Protect Cardholder Data with Strong Cryptography During Transmission | |
| Maintain a Vulnerability Management Programme | 5 | Protect All Systems and Networks from Malicious Software |
| 6 | Develop and Maintain Secure Systems and Applications | |
| Implement Strong Access Control Measures | 7 | Restrict Access to Cardholder Data |
| 8 | Identify Users and Authenticate Access | |
| 9 | Restrict Physical Access | |
| Regularly Monitor and Test Networks | 10 | Log and Monitor All Access |
| 11 | Test Security of Systems and Networks Regularly | |
| Maintain an Information Security Policy | 12 | Support Information Security with Organisational Policies |
Now, let's dive into what each of these goals and requirements actually means in practice, using some real-world analogies.
Goal 1: Build and Maintain a Secure Network and Systems
This first goal is all about building a strong digital perimeter around your data environment. It’s the equivalent of putting up fortress walls and posting guards at the gates to control who comes in and out.
Requirement 1: Install and Maintain Network Security Controls: Think of this as your network’s security guards. It means having properly configured firewalls and routers to inspect traffic and block anything unauthorised from reaching the systems holding card data. Just like a guard checks IDs at the door, a firewall makes sure only legitimate traffic gets through.
Requirement 2: Apply Secure Configurations to All System Components: This one is simple but critical. You must change all default passwords and security settings on your hardware and software. Leaving the vendor-supplied defaults like "admin/password" is like leaving the key to your building under the doormat for anyone to find.
Goal 2: Protect Account Data
Once your perimeter is secure, the next job is to protect the actual data inside. The idea is that if a threat does somehow get past your walls, the data they find is completely useless to them.
Requirement 3: Protect Stored Account Data: If you absolutely must store cardholder data, this rule defines how. It demands that you make the primary account number (PAN) unreadable using strong methods like encryption or tokenisation. It’s the difference between shredding sensitive documents before you bin them versus just tossing them in whole.
Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission: When payment data is sent across open networks (like the internet), it has to be encrypted. This is like sending a valuable package in a locked, armoured van instead of an open-top convertible. Strong TLS encryption ensures that even if someone intercepts the data, they can’t read it.
A core principle of PCI DSS is data minimisation. The safest data is data you don't have. If you can avoid storing cardholder data altogether, you dramatically reduce both your risk and the headache of meeting these requirements.
Goal 3: Maintain a Vulnerability Management Programme
Security isn't a "set it and forget it" task. It's an ongoing process of finding and fixing weaknesses. This goal is all about proactively hunting for vulnerabilities before criminals can find and exploit them.
Requirement 5: Protect All Systems and Networks from Malicious Software: This is about using up-to-date anti-virus and anti-malware software on all systems that could be targeted. It’s the digital version of a regular health screening to find and remove infections before they can spread.
Requirement 6: Develop and Maintain Secure Systems and Applications: This requirement ensures that security is baked into your software and applications from the very beginning. It also means applying security patches quickly to fix known issues, just like a car manufacturer issuing a recall to fix a faulty part before it causes an accident.
Goal 4: Implement Strong Access Control Measures
This is all about making sure that only the right people can access sensitive data, and only for legitimate business reasons. It’s based on the well-known security principle of "need to know."
Requirement 7: Restrict Access to Cardholder Data: Access to sensitive data must be limited strictly to the people whose jobs depend on it. You wouldn't give every employee in a company the key to the main vault; you’d only give it to a trusted few.
Requirement 8: Identify Users and Authenticate Access: Every single person who accesses your systems needs a unique ID. This rule also calls for strong authentication, such as multi-factor authentication (MFA), to prove they are who they say they are. It’s the difference between a generic keycard anyone could use and a system that requires a keycard and a fingerprint scan.
Requirement 9: Restrict Physical Access: This covers the physical security of any computer, server, or device that holds card data. It means locking server rooms and securing payment terminals to prevent someone from physically tampering with them. This one is as straightforward as it gets—literally locking the doors.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you can't see. This goal focuses on keeping a constant watch over your environment for any suspicious activity and regularly testing your defences to make sure they're actually working.
Requirement 10: Log and Monitor All Access to Network Resources and Cardholder Data: You must keep detailed logs of everything that happens on your network, especially any time cardholder data is accessed. These logs are like security camera footage; they provide a trail to investigate if a breach occurs and can help you spot unauthorised access as it happens.
Requirement 11: Test Security of Systems and Networks Regularly: This involves actively probing your own defences for weaknesses through things like vulnerability scans and penetration tests. It’s like hiring a team of ethical hackers to try and break into your own building just to see if your security holds up under pressure.
Goal 6: Maintain an Information Security Policy
Finally, all these technical controls need to be held together by a strong foundation of policies and procedures that everyone in the organisation understands and follows. This is the human element of security.
- Requirement 12: Support Information Security with Organisational Policies and Programs: This is the master requirement that ties everything else together. It requires you to have a formal security policy that documents your rules, assigns responsibilities, and includes a plan for what to do if a breach occurs. It’s the security manual that ensures everyone, from the top down, knows their role in protecting customer data, creating a security-first culture.
Navigating PCI Compliance in Your Contact Centre

While the 12 core requirements for PCI compliance apply to every business, the contact centre is a different beast altogether. It's a uniquely complex and high-risk environment. Handling payments over the phone, through web chat, or other live channels creates a compliance minefield that many organisations find themselves completely lost in.
The second a customer reads their card number aloud, your PCI scope explodes. Just think about what that one simple action sets in motion.
All of a sudden, every single piece of tech and every process that touches that conversation is dragged into the Cardholder Data Environment (CDE). This means they all have to be locked down according to the demanding PCI DSS framework.
The Expanding Scope of Contact Centre Payments
So what exactly gets pulled into this expanded scope? The list is almost always longer than businesses first assume, creating a massive—and expensive—security perimeter to defend.
- The Agent's Workstation: The keyboard they use to type the card details, the screen displaying them, and the entire operating system are all in scope.
- Audio Equipment: The agent's headset and microphone, the very tools capturing the spoken card numbers, become part of the CDE.
- Network Infrastructure: Your whole phone network (VoIP or otherwise), along with the routers and switches carrying that voice data, are now in scope.
- Recording Systems: This is a big one. Call and screen recording platforms, which often capture card details for quality checks, create an enormous compliance risk.
- Physical Environment: Even a humble notepad and pen on an agent’s desk, used to scribble down a number, can bring your physical office into scope.
This "everywhere, all at once" data exposure is the heart of the problem. Securing this vast, interconnected environment isn't just technically difficult; it's incredibly costly. It forces you to apply all 12 requirements to systems that were never built with payment security in mind.
The fundamental issue with traditional contact centre payments is the uncontrolled flow of sensitive data. When card numbers are spoken, typed, and recorded, they contaminate your entire infrastructure, making compliance a monumental task.
Common Vulnerabilities and Compliance Gaps
This widespread data contamination leads to some common and frankly dangerous vulnerabilities. Many contact centres are sitting on toxic data stored in places they never intended, creating ticking time bombs for a potential breach.
One of the most significant risks is data leakage into call recordings. Storing audio files containing full cardholder data is a direct violation of PCI DSS Requirement 3. In the same vein, screen capture software used for training can easily record sensitive information being punched into a CRM or payment app.
And it doesn't stop there. Digital channels add another layer of complexity. If your agents handle payments over web chat, the chat logs themselves can become a goldmine of unsecured card data, widening your scope even further. For businesses in finance, like those using a chatbot for banking, figuring out how PCI DSS applies to these newer channels is critical.
For a deeper dive into managing these specific risks, our guide to call centre payment security solutions provides detailed strategies. Ultimately, failing to control this data flow turns your contact centre into a high-risk zone where meeting the requirements for PCI compliance feels like a constant, uphill battle.
How to Drastically Reduce Your PCI Compliance Scope

After seeing just how many moving parts exist in a contact centre, it’s obvious that trying to bolt security onto every single touchpoint is a losing game. The smartest strategy for meeting the requirements for PCI compliance isn't to build a bigger, more complicated fortress around your data. It's to stop the sensitive cardholder data from ever getting inside in the first place.
This approach is called scope reduction, and it is without a doubt the most powerful tool in your compliance arsenal. Rather than wrestling with all 12 requirements across dozens of systems, you strategically take those systems out of the equation altogether. The mission is to shrink your Cardholder Data Environment (CDE) down to its absolute minimum, making compliance simpler, cheaper, and genuinely more secure.
The Pneumatic Tube Analogy
Think of it like this: imagine a customer wants to pay you in cash, but you're standing behind a thick pane of security glass. Instead of you taking the money, there's a sealed pneumatic tube next to your window. The customer puts the payment in the tube, and it shoots directly to the bank's vault, completely bypassing you.
You can watch the transaction happen and get a confirmation that the money arrived safely, but the cash itself never touches your hands. Because you never handled it, you don't need the same extreme security measures as the bank. This is exactly how modern payment security works. It creates a secure, isolated channel that keeps payment data far away from your business environment.
Key Technologies for Scope Reduction
Several proven technologies make this "pneumatic tube" approach a reality, particularly for contact centres taking payments over the phone. These methods are built to capture card details without them ever being heard, seen, or stored by your agents or on your systems.
DTMF Masking: When a customer is ready to pay, your agent can switch the call into a secure payment mode. The customer enters their card numbers using their telephone keypad, and Dual-Tone Multi-Frequency (DTMF) masking technology intercepts those tones before they ever reach the agent or your call recording system. The tones are sent straight to the payment processor, while your agent just hears flat, masked beeps.
Channel Separation: This technique splits the phone call into two streams. The voice conversation stays with your agent, but the sensitive data entered by the customer travels down a completely separate, encrypted path to the payment gateway. The agent can still guide the customer through the process, but the card numbers are completely invisible to them and your network.
These technologies effectively snip the wire connecting your contact centre infrastructure to raw cardholder data. The agent's computer, the phone network, and your call recording platform are no longer in scope because they never touch sensitive information.
By implementing solutions that prevent card data from entering your environment, you can reduce your PCI DSS scope by as much as 95%. This turns a sprawling, enterprise-wide compliance headache into a much smaller, manageable process focused only on the payment solution itself.
The Business Impact of a Smaller Scope
Shrinking your PCI scope is more than just a technical victory; it delivers powerful business advantages that ripple across your entire organisation.
A radically smaller scope means fewer systems that need strict PCI controls, audits, and constant maintenance. This directly cuts costs for:
- Annual Audits: Instead of a Qualified Security Assessor (QSA) needing to inspect your entire network, their review narrows to just the payment platform.
- Remediation: You'll spend far less time and money fixing compliance gaps on desktops, servers, and software that are now out of scope.
- Security Tools: The need for expensive tools like file integrity monitoring or intrusion detection systems is dramatically reduced for out-of-scope systems.
Beyond the savings, scope reduction massively lowers your risk of a data breach. Since the most toxic data is no longer stored or processed on your network, you become a much less appealing target for cybercriminals. If a breach did happen on your main network, there would be no cardholder data there to steal. This hardens your security posture and protects your brand's reputation.
Ultimately, by focusing on scope reduction, you shift your compliance strategy from a defensive, reactive chore to a proactive and efficient advantage. It makes meeting the requirements for PCI compliance both achievable and sustainable, freeing you up to focus on your actual business.
Here is the rewritten section, crafted to sound completely human-written and natural.
Integrating PCI Compliance into Your Broader Security Strategy
Thinking about PCI compliance as just another box-ticking exercise is a missed opportunity. Smart businesses now see it for what it really is: a fundamental part of building a trustworthy, modern organisation. Instead of treating PCI DSS as an isolated chore, they use it as a strategic pillar that strengthens their entire security posture and keeps them in step with wider regulations.
It’s about more than just protecting card numbers. The robust controls you put in place for PCI compliance—things like tight access control, network monitoring, and data encryption—create a powerful ripple effect. They help safeguard all of your sensitive information and foster a security-first culture that customers genuinely appreciate. This isn't just about dodging fines; it’s about proving you’re serious about protecting their privacy.
PCI DSS as a Cornerstone for Other Frameworks
The principles baked into PCI DSS are simply good security hygiene. Because of this, the work you put into getting compliant often gives you a massive head start on meeting other standards and regulations.
- GDPR Alignment: Many PCI controls, like restricting data access and protecting stored information, directly support the core data protection principles of the General Data Protection Regulation (GDPR).
- ISO 27001 Synergy: The PCI framework’s heavy emphasis on risk assessments, policies, and continuous monitoring closely mirrors what’s needed for an Information Security Management System (ISMS) under ISO 27001.
This overlap means your compliance efforts become far more efficient. By mapping PCI controls to other frameworks, you can stop duplicating work and build a single, unified security strategy that tackles multiple requirements at once.
The Shift to Continuous Compliance with PCI DSS v4.0
The security world never stands still, and neither do the standards that govern it. The latest version, PCI DSS v4.0, marks a critical evolution by moving away from a simple annual audit towards a model of continuous compliance. This change acknowledges a simple truth: security threats don’t work to a yearly schedule—they’re a constant reality.
The core message of PCI DSS v4.0 is that security is not a one-time project but an ongoing, active process. It pushes businesses to weave security into their daily operations rather than just scrambling to prepare for an annual check-up.
This strategic shift lines up perfectly with broader compliance trends in the UK. With 85% of UK and Ireland organisations expecting their compliance strategy to change due to new laws, there's a clear move towards integrating security frameworks. It's no surprise that 85% are also planning an ISO 27001 audit in 2025 to align their controls more systematically.
All businesses must be aligned with PCI DSS v4.0 by March 2025, which introduces stricter rules for multi-factor authentication and threat detection. You can learn more about how PCI DSS is critical in the evolving retail landscape. By embracing this bigger picture, you can transform the requirements for PCI compliance from a burden into a strategic advantage that protects your brand and builds lasting customer trust.
Your Actionable PCI Compliance Checklist
Knowing the rules is one thing, but putting them into practice is where the real work begins. Let's shift from theory to action with a practical checklist, breaking the journey into four clear phases.
Think of this as your project plan for PCI compliance. It's a structured approach that takes the guesswork out of the process, turning a daunting standard into a series of logical, manageable steps. Each phase builds on the one before it, so you can be confident nothing important gets missed.
Phase 1: Scoping Your Environment
First things first: you need to map out your battlefield. You can't protect what you don't know you have, which makes this discovery phase absolutely essential.
- Map Data Flows: Start by tracing the path of cardholder data. Identify every single system, application, and process it touches. This includes the obvious, like your payment gateway, but also your CRM, agent desktops, and especially your call recording platforms.
- Define Your CDE: With your data map in hand, you can officially draw the boundaries of your Cardholder Data Environment (CDE). Anything and everything inside this perimeter is in scope for PCI DSS.
- Find Scope Reduction Opportunities: This is a game-changer. Look for any point where card data enters your environment when it doesn't need to. This is precisely where solutions like Paytia's Secureflow come in, preventing that sensitive information from ever touching your systems and dramatically shrinking your CDE from day one.
Phase 2: Assessing Your Gaps
Now that you know exactly what you need to protect, it’s time to see how your current security measures stack up against the 12 core PCI requirements.
This isn't just an exercise in finding faults; it's about creating a clear, prioritised action plan. A solid gap analysis is the foundation for everything that comes next.
Go through each applicable requirement with a fine-tooth comb. Document where your controls are solid and, more importantly, where they're weak or missing entirely. This list becomes your roadmap for remediation.
Phase 3: Remediating and Reporting
This is where you roll up your sleeves and fix the issues you found in your assessment. It could involve anything from reconfiguring firewalls and encrypting data to tightening up your access controls.
This is also the stage where you would deploy any scope-reduction technologies you identified. And if you're taking old, non-compliant systems offline, using a detailed server decommissioning checklist is a smart move to ensure you don't accidentally leave sensitive data behind.
Once the fixes are in place, you need to formalise your compliance. For most businesses, this means completing a Self-Assessment Questionnaire (SAQ). Larger organisations might need a formal Report on Compliance (ROC) from a Qualified Security Assessor (QSA).
For a deep dive into this entire process, our complete PCI DSS compliance checklist provides detailed, step-by-step guidance.
Your PCI Requirement Questions, Answered
When you're trying to get to grips with payment security, a lot of practical questions pop up. Let's tackle some of the most common ones we hear from businesses just like yours.
I Use a Third-Party Processor, So I’m Compliant, Right?
It’s a great start, but not quite the full story. Using a payment processor like Stripe or PayPal is a smart move that massively reduces your compliance burden. However, it doesn't get you off the hook completely.
You’re still responsible for making sure your own business processes and systems that touch the payment journey are secure. In most cases, this means you'll still need to complete a Self-Assessment Questionnaire (SAQ) to prove it.
Does PCI DSS Apply to Debit Card Payments?
Yes, absolutely. PCI DSS covers any payment card that features the logo of one of the five big founding members of the PCI Security Standards Council. This net includes credit, debit, and even prepaid cards from brands like Visa, Mastercard, and American Express. The type of card makes no difference to your compliance duties.
What’s the Worst That Can Happen if We’re Not Compliant?
Ignoring PCI compliance is a risky gamble. While it isn't a government law, it's a contractual requirement enforced by the major card brands, and they take it very seriously.
If you fall out of compliance, you could be facing:
- Monthly fines anywhere from £4,000 to £80,000.
- Higher transaction fees slapped on by your acquiring bank.
- And if a data breach happens on your watch? You could be liable for the costs of a forensic investigation, card reissuing fees, and the kind of reputational damage that’s hard to bounce back from.
Think of it this way: compliance is really just good risk management. The investment in getting it right is tiny compared to the financial and brand devastation a data breach can cause.
But We Don’t Store Any Card Data. Surely That Means We’re Compliant?
That's a common misconception. While not storing card data is a huge step in the right direction, PCI DSS still applies. The standards are designed to protect the entire payment lifecycle, which includes the moments when data is being processed and transmitted.
The good news is that not storing data dramatically shrinks your PCI scope and makes compliance much, much simpler. But it doesn’t give you a free pass.
Ready to shrink your PCI scope by up to 95% and simplify compliance for good? Paytia's Secureflow platform ensures sensitive payment data never touches your systems, keeping your contact centre secure and your customers protected. Discover a smarter way to handle payments.
Ready to Simplify Compliance?
Get expert guidance on UK payment regulations and PCI DSS compliance. Contact us today.
