
Take Card Payments Over the Phone: take card payments over the phone guide
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
If you want to take card payments over the phone, you need a way to do it that’s both secure and smooth for the customer. This means using technology that keeps sensitive card details completely out of your hands, which is the cornerstone of any modern, compliant phone payment setup.
Why Secure Phone Payments Still Matter

In a world of digital wallets and one-click checkouts, taking payments over the phone might feel a bit old-fashioned. But for countless businesses—especially in sectors like utilities, insurance, and healthcare—it’s still an essential channel. It offers a direct, human connection that many customers still value, particularly when they’re settling a bill or sorting out a problem.
A clunky or insecure phone payment process does more than just frustrate people; it actively erodes trust in your brand. That moment of hesitation when a customer is asked to read out their card number? That’s a clear signal that something is wrong. Mastering this isn’t just about ticking a compliance box—it's a critical part of the customer experience that can give you a real competitive edge.
The Modern Payment Landscape
The UK market really highlights this point. While contactless is everywhere, phone payments have become a lifeline for contact centres. A recent UK Finance report showed that debit cards were used for 26.1 billion payments, making up half of all transactions. Even with 76% of those being contactless, the transactions that aren't face-to-face—like those over the phone—are still a vital part of the picture. You can dig into the full details in the UK Finance Payment Markets Report.
This reality puts a huge responsibility on your shoulders. You have to handle these payments without putting customer data at risk. That's where the Payment Card Industry Data Security Standard (PCI DSS) comes in.
PCI DSS isn't just a rulebook. It’s a framework for building and maintaining a secure payment environment. Get it right, and you protect both your customers and your business from the fallout of a data breach.
Understanding the Core Risks
If you ignore these standards, you're leaving the door wide open to some serious vulnerabilities. The main risks when you take card payments over the phone include:
- Data exposure: Your agents hearing or seeing full card numbers.
- Insecure storage: Card details getting caught in call recordings or appearing on screen captures.
- Reputational damage: A single security slip-up can destroy years of customer loyalty.
Getting this wrong can lead to hefty fines, losing your ability to process card payments, and causing irreversible harm to your brand. So, putting a secure solution in place isn't just a good idea—it’s essential for any organisation that values its customers and its own future.
Navigating Security and Compliance Obligations

Before you even think about technology, you have to get your head around the rules of the road. When you take card payments over the phone, you’re handling highly sensitive financial data, and that comes with some serious responsibility. This responsibility is governed by a global standard: the Payment Card Industry Data Security Standard (PCI DSS).
Don't think of PCI DSS as just a list of restrictive rules. It’s a framework designed to protect your customers, your reputation, and your bottom line. It lays out the security controls needed to stop card data theft. Get it wrong, and you could be facing hefty fines, the loss of your ability to process cards, and catastrophic damage to customer trust.
Demystifying PCI Scope
A core concept you need to grasp is PCI scope. Put simply, this covers every person, process, and piece of technology in your business that comes into contact with cardholder data. The bigger your scope, the more complex and expensive it becomes to get—and stay—compliant.
Your goal should always be to shrink this scope. If your agents never hear, see, or handle sensitive card details, you can effectively remove them and their workstations from the PCI audit. We call this "de-scoping," and it dramatically simplifies your compliance obligations, saving you a world of time, money, and headaches.
The trouble is, many traditional phone payment methods put you squarely in scope. We see these high-risk practices all the time:
- Call Recordings: Standard call recording systems capture everything, including the customer reading out their 16-digit card number and CVC. That data is now stored on your systems, making you a prime target.
- Screen Monitoring: Software that records an agent's screen for QA can easily capture them typing card details into a virtual terminal.
- Handwritten Notes: It sounds old-fashioned, but it happens. An agent jotting down card details on a sticky note—even with good intentions—creates a massive, unnecessary security hole.
PCI DSS compliance isn't just about passing an annual audit; it's about embedding security into your daily operations. A single insecure process can undermine your entire security posture and expose you to significant risk.
A Tale of Two Housing Associations
Let's look at how this plays out in the real world. Imagine a local housing association that needs to take card payments over the phone for rent arrears.
Scenario 1: The Insecure Way
An agent takes a call from a tenant. To process the payment, the agent asks the tenant to read out their full card number, expiry date, and CVC. As the call is being recorded for "training purposes," the agent types this information directly into a payment portal on their computer.
In this scenario, the sensitive data is now in the call recording, has been visible on the agent's screen, and might even be lingering in the computer's memory. The PCI scope is huge. A data breach is just waiting to happen.
Scenario 2: The Secure Way
The same agent takes the same call. But this time, when it's time to pay, the agent explains that for security, the tenant will use their telephone keypad to enter their card details. The agent stays on the line to help, but the system uses DTMF masking technology.
The agent only hears flat tones, not the sensitive numbers, and nothing appears on their screen. The data travels directly to the payment gateway, completely bypassing the housing association's systems.
This simple process change has taken the agent, their computer, and the call recording system completely out of PCI scope. The tenant’s data is secure, and the association has drastically cut its compliance burden. It’s a win for everyone.
To further tighten security, it's crucial to consider robust authentication methods like implementing two-factor authentication. As compliance evolves, staying informed is key; our guide on the upcoming PCI DSS 4.0.1 requirements for telephone payments offers deeper insights.
https://www.paytia.com/resources/blog/pci-dss-4-0-1-telephone-payments-march-2025-compliance-requirements
Choosing the Right Technology for Phone Payments
Once you've got a handle on the security rules, the next job is to find the right tools to make compliance a reality. To securely take card payments over the phone, you need technology specifically designed to keep sensitive data completely out of your environment. This is a world away from outdated and risky habits like pausing call recordings, which are wide open to human error and still leave your agents exposed.
Modern solutions are built from the ground up to "de-scope" your operations from PCI DSS requirements. In simple terms, they make sure card numbers, expiry dates, and CVCs never even touch your systems. This doesn't just protect your customers; it massively simplifies your own compliance burden, freeing up your team to focus on what they do best—serving those customers.
Let's walk through the leading technologies available today, each with its own strengths and best-fit scenarios.
Live Agent Assisted Payments with DTMF Masking
Picture this: your agent is on a call with a customer ready to pay an invoice. Instead of asking them to read out their card details—a huge security no-no—the agent triggers a secure payment process. The customer then simply uses their telephone keypad to punch in their card number.
This is where Dual-Tone Multi-Frequency (DTMF) masking works its magic. As the customer taps the keys, your agent just hears flat, monotonous beeps, not the actual tones that correspond to the numbers. On their screen, they only see asterisks popping up in the payment fields. The sensitive data is captured and sent straight to the payment gateway, completely bypassing your agent, your network, and your call recordings.
This method is perfect for contact centres where that human touch is vital. The agent can stay on the line to guide the customer, answer any last-minute questions, and confirm the payment went through, all without ever being exposed to a single digit of card information. It’s an elegant solution that keeps the conversation flowing while locking down security.
Automated IVR for 24/7 Self-Service
What about payments that come in after hours, or for routine things like topping up an account? An Interactive Voice Response (IVR) system lets customers pay entirely on their own, without ever needing to speak to an agent.
A customer can call a dedicated payment line, verify their identity with something like an account or invoice number, and then follow the voice prompts to enter their card details using their keypad. It’s a secure, efficient self-service channel that works for you 24/7.
For businesses with high volumes of routine payments, like utility companies or subscription services, an automated IVR is a game-changer. It frees up your agents to deal with more complex issues while giving customers a super-convenient way to pay whenever it suits them.
This approach not only trims your operational costs but delivers a consistent and secure experience every single time. You can learn more about how a well-designed payment IVR solution can completely transform your collections process.
Secure Payment Links via SMS and Email
Sometimes, the middle of a phone call just isn't the right time or place to take a payment. Your customer might be on a busy train, in a public place, or they might just prefer to handle the transaction privately on their own device. For these moments, sending a secure payment link is the perfect answer.
Your agent can generate a unique, time-sensitive link and send it straight to the customer's mobile via SMS or to their email. The customer taps the link, which opens a secure, branded payment page where they can enter their card details. The transaction is processed directly with the payment gateway, and both your agent and the customer get an instant confirmation.
This method is incredibly flexible and puts the customer firmly in control. It's especially effective for:
- Following up on quotes: Send a link to make it effortless for a customer to approve a job and pay the deposit.
- Chasing outstanding balances: A friendly SMS reminder with a payment link is far less intrusive and often more effective than a phone call.
- Complex orders: When a customer needs a moment to review the details before committing, a payment link gives them that space.
The Power of Tokenization
Running behind the scenes of many of these secure methods is a powerful technology called tokenization. Think of it like a casino chip. You hand over your real money at the cashier and get chips in return. Those chips have value inside the casino, but they’re useless to a thief who nabs them on the street.
Tokenization does something very similar with card data. When a payment is made for the first time, the payment gateway swaps the sensitive card number for a unique, non-sensitive identifier called a "token." This token can then be safely stored in your CRM or billing system for future use, like for recurring subscriptions or processing refunds.
You can charge the token again and again without ever needing to see or store the original card details. If you ever had a data breach, the thieves would only find a list of useless tokens, not actual card numbers. It's a foundational technique for shrinking your PCI scope and protecting your business.
Comparison of Modern Phone Payment Technologies
Choosing the right tool—or combination of tools—really comes down to your specific business needs, from your call volume and agent workflow to the kind of experience you want to provide. A small business might lean heavily on payment links, while a large, bustling contact centre could get the most value from a blend of all three technologies.
To help you weigh the options, here’s a quick comparison of the modern methods we've discussed.
| Technology | How It Works | Best For | PCI Scope Impact | Customer Experience |
|---|---|---|---|---|
| DTMF Masking | Customer uses their keypad; agent hears masked tones and sees asterisks. | High-touch, agent-led conversations in busy contact centres. | High Reduction. De-scopes agents and call recordings. | Seamless and secure, with constant agent support. |
| Automated IVR | Customer calls a number and follows prompts to pay via keypad. | 24/7 self-service for routine or high-volume payments. | Maximum Reduction. No human involvement in the payment process. | Convenient and fast for customers who know what they owe. |
| Payment Links | Agent sends a secure link via SMS/email for customer to complete payment. | Mobile customers, quote follow-ups, and non-voice interactions. | High Reduction. Payment occurs outside your direct environment. | Puts the customer in control of when and where they pay. |
Ultimately, by picking the right mix of these technologies, you can build a flexible and deeply secure system to take card payments over the phone. It’s the key to protecting your customers, empowering your agents, and making your compliance journey a whole lot simpler.
Weaving Secure Payments into Your Existing Workflow
Picking the right payment technology is one thing; getting it to play nicely with your existing setup is a whole different ball game. Let's be honest, a powerful payment solution is useless if it forces your team to constantly jump between different screens and applications. The real goal is to embed secure payment tools directly into the systems your agents live in all day.
When you take card payments over the phone, true efficiency comes from a single, unified workflow. This means plugging your payment platform straight into your telephony system, your Customer Relationship Management (CRM) software, and your payment gateway. Get this right, and you create a smooth, uninterrupted journey for both your agents and your customers.
This is what that flow looks like in practice, showing how sensitive data is channelled away from your internal systems.
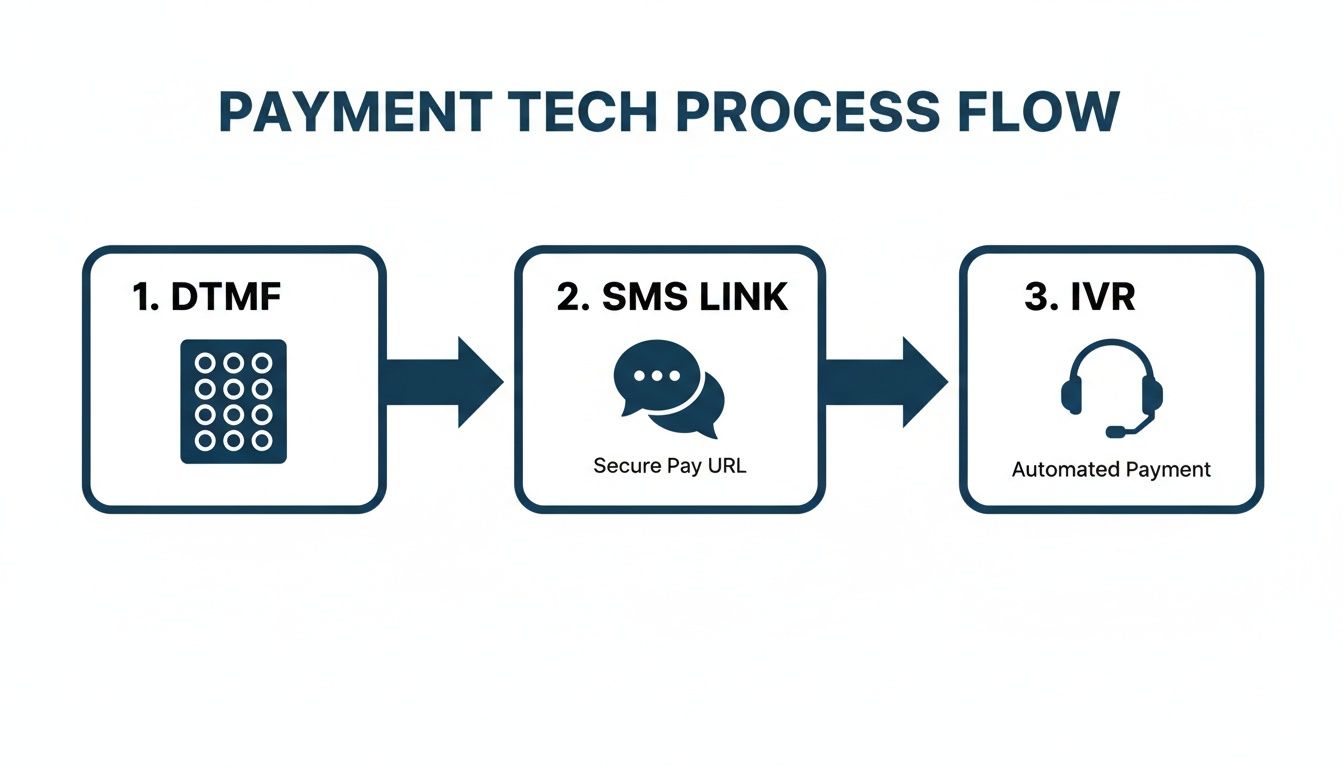
Whether it’s through DTMF key entry, a secure SMS link, or an automated IVR, the design principle is the same: route the payment details directly and securely to the processor, bypassing your own environment entirely.
Connecting Your Telephony and CRM
Your phone system is the heart of your customer conversations. Modern Voice over IP (VoIP) and contact centre platforms are built with connectivity in mind. By integrating your payment solution, an agent can kick off a secure payment process—like DTMF masking—right from their call control panel, without ever needing to switch screens.
Connecting to your CRM is just as critical. When a payment goes through successfully, the integration should automatically handle the admin.
- It can update the customer's record in the CRM to show the payment was made.
- It should log the transaction details (without ever touching the card data itself).
- It can even trigger the next step in your process, like marking an invoice as paid.
This kind of automation cuts out tedious manual data entry, slashes the risk of human error, and gives your team a complete, real-time picture of every customer interaction. For businesses that rely on phone orders, this is a non-negotiable, especially if you’re considering options like hiring a virtual assistant to handle phone orders and need the process to be foolproof.
The Role of APIs in Custom Integrations
But what if your setup is a bit more... unique? This is where Application Programming Interfaces (APIs) come in. Think of an API as a universal translator that allows different software systems to communicate. A payment platform with a solid, well-documented API gives you the freedom to build custom connections that fit your specific needs perfectly.
For example, you could use an API to build a feature that automatically texts a payment link to a customer the moment a quote is generated in your bespoke quoting software. The possibilities are nearly endless, empowering your developers to create a truly seamless system. If you want to get into the technical weeds, understanding how a payment gateway API integration works is a fantastic place to start.
A successful integration means your payment data flows where it needs to for reporting and reconciliation, but the sensitive card details never enter your environment. It's about getting the information you need without the risk you want to avoid.
Your Integration Planning Checklist
A smooth integration doesn't happen by accident; it requires a bit of planning. Before you kick things off, get the right people in a room and walk through these key checkpoints. It’ll ensure everyone is on the same page and set you up for a successful launch.
- Identify Stakeholders: Who needs a seat at the table? This usually includes your IT team, contact centre managers, compliance officers, and someone from finance.
- Map Your Current Workflows: Get a clear picture of how your agents handle payments right now. Where are the frustrating bottlenecks? What are the biggest security risks? This map will show you exactly where the new tech will make the biggest impact.
- Define Technical Requirements: Make a list of all the systems that need to talk to each other. Get specific: your telephony platform (e.g., Avaya, Mitel), your CRM (e.g., Salesforce, HubSpot), and your payment gateway (e.g., Stripe, Worldpay).
- Plan the Testing Phase: How will you make sure it all works before going live? Create a detailed testing plan that covers everything from successful payments and failed transactions to refunds and edge cases.
- Prepare for Go-Live: Develop a clear communication plan to let your team know what’s changing. Schedule training sessions so every agent feels confident guiding customers through the new, secure workflow from day one.
Building a Security-First Team Culture
Technology is a powerful shield, but it’s your team that holds it. Even the most sophisticated payment solution can be undone by poor habits on the ground. Building a genuine security-first culture is about turning compliance from a dusty rulebook into a shared mission where everyone understands their part in protecting customer data.
This isn’t just about teaching the technical steps of how to take card payments over the phone. It’s about instilling the why behind the security protocols. When your agents grasp the real-world consequences of a data breach or a clever social engineering attack, they transform from being the weakest link into your strongest line of defence.
The goal is to get your team to a place where they are vigilant and confident, acting as active guardians of customer trust, not just passive users of a system.
Training Your Team to Be Human Firewalls
Effective security training isn't a one-and-done induction session; it's an ongoing conversation. Your agents are on the front line, and they need to be ready for those moments when security is tested, whether by a determined fraudster or a well-meaning but misguided customer.
Your training needs to feel real. Forget dry theory and focus on practical scenarios. Run drills on how to handle a customer who insists on reading their card details out loud. Every agent needs a polite, firm script to gently guide the customer back to the secure keypad entry process.
Instil this one non-negotiable rule above all others: Never ask a customer to read their card details aloud, and never accept them if they offer. This single principle is the bedrock of a secure phone payment environment.
A solid training programme should build this defensive mindset by covering a few key areas:
- Spotting Social Engineering: Teach agents to recognise the tell-tale signs, like callers who try to create a false sense of urgency or find excuses to bypass the standard process.
- Guiding the Secure Process: Make sure every agent can confidently explain how DTMF masking or a payment link works, reassuring customers that these steps are there for their protection.
- Handling Exceptions Gracefully: What happens if a customer is fumbling with their keypad? Agents need a clear protocol for helping them without ever asking for the sensitive numbers themselves.
Documenting Clear Operational Procedures
Confidence comes from clarity. When your team has a clear, documented process for every part of the payment journey, there’s no room for improvisation or guesswork. This documentation isn't just for new starters; it's the single source of truth that ensures consistency and compliance for everyone.
Think of it as your operational playbook, and make sure it’s easily accessible to the whole team. It needs to cover more than just the initial payment transaction.
Create unambiguous, step-by-step guides for these critical financial operations:
- Processing Refunds: Define the exact workflow for issuing a refund using a transaction ID or token, making it clear that new card data should never be requested.
- Managing Disputes and Chargebacks: Outline what non-sensitive information an agent needs to gather to help the finance team resolve a customer dispute.
- Setting Up Recurring Payments: Detail how to use tokenization to securely establish a subscription, reinforcing that you never store the actual card details.
Fostering Shared Responsibility
Ultimately, a security-first culture only works when everyone feels accountable. Security isn't just the IT department's job or something for a compliance officer to worry about. It belongs to every single person who interacts with your customers.
Create an environment where it's safe to ask questions. If an agent feels a request is unusual or a situation seems off, they should feel comfortable flagging it with a manager without any fear of being criticised. Regular team huddles are perfect for sharing any near-misses or discussing new scam tactics that might be doing the rounds.
By making security a daily conversation and a core team value, you build a much more resilient operation. Your people, armed with the right knowledge and supported by secure technology, become your greatest asset in maintaining a safe and trustworthy environment to take card payments over the phone.
Common Questions About Phone Payments
Even with the best tech, new questions always pop up when you decide to take card payments over the phone. Getting straight answers builds confidence—not just for your team, but for your customers, too. Let's tackle some of the most common queries we hear from businesses moving to a more secure way of working.
We'll cover everything from the legality of it all to the practical side of handling different customer scenarios, always coming back to the core principles of security and compliance.
Is It Legal to Take Card Payments Over the Phone?
Yes, it’s completely legal to take card payments over the phone. But there’s a crucial catch: you must do it in a way that’s compliant with the Payment Card Industry Data Security Standard (PCI DSS). This is non-negotiable.
Simply asking a customer to read their card details aloud over a recorded phone line is not compliant or secure. To operate legally and protect your customers, you have to use secure technology like DTMF masking, payment links, or automated IVR systems. These methods are designed to ensure sensitive cardholder data never even touches your company’s environment, which is the whole point of modern, compliant payment processing.
What if a Customer Refuses to Use the Keypad?
This is a very common concern, but it’s almost always down to a customer not being familiar with the process. If someone hesitates to use their keypad to enter their card details, it’s a perfect opportunity for your agent to reassure them and build trust.
It's all in the explanation. Your agents should be trained to calmly and clearly explain why you’re using this method.
"For your own security, we never ask for card details to be spoken aloud. Using your keypad sends the numbers directly to the bank's secure network without us ever seeing or storing them. It's the safest way to pay over the phone."
A confident, well-practised explanation like this nearly always smooths things over. It reframes the process as a benefit—a security measure you’ve put in place specifically to protect them.
Can We Still Offer Refunds Easily?
Absolutely. A big misconception is that taking your call centre out of PCI scope makes things like refunds more complicated. In fact, modern payment systems make it much simpler and more secure by using tokenization.
When the original payment is made, the payment gateway securely stores the real card details and gives your system a non-sensitive "token" instead. Think of it as a unique, meaningless reference number.
To process a refund, your agent just:
- Finds the original transaction in your payment portal or CRM.
- Clicks to issue a refund against that transaction's token.
- The system tells the payment gateway to send the money back to the original card.
Your agent never needs to ask for card details again, and the refund is processed without any sensitive data ever flowing back through your systems. It’s cleaner, faster, and far more secure.
What’s the Difference Between a Payment Gateway and a Virtual Terminal?
These two terms often get mentioned together, but they do very different jobs when you take card payments over the phone.
A Payment Gateway is the engine of the operation. It's the secure service that connects to the card networks (like Visa and Mastercard), gets the transaction authorised, and moves the money from the customer’s bank to yours. Think of it as the secure digital plumbing for the funds.
A Virtual Terminal is a web-based page where a person can manually type in card details to send them to the payment gateway. Historically, this is what agents used, but it’s a compliance nightmare. It puts your business squarely in PCI scope because your agent sees, hears, and handles the raw card data.
Modern secure phone payment solutions make the agent-facing virtual terminal obsolete. They provide a customer-facing interface (like DTMF masking or a payment link) that captures the card details and sends them directly to the payment gateway. This is the fundamental shift—it keeps your team and your systems completely out of the loop.
Ready to transform how you take card payments over the phone? Paytia provides a suite of PCI DSS Level 1 certified solutions designed to de-scope your environment, reduce compliance costs, and build customer trust. Discover how our agent-assisted, IVR, and payment link technologies can secure your revenue streams.
Learn more and book a demo at https://www.paytia.com.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
