What is tokenization in payments and how it secures your data
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
At its heart, payment tokenization is a clever security method that swaps sensitive card data for a unique, non-sensitive placeholder called a 'token'. This simple switch means the actual card number is never exposed during or after a transaction.
Think of it like a casino chip. Inside the casino, it represents real value, but if someone were to steal it and take it outside, it's just a useless piece of plastic. Tokenization does the same thing for your customers' payment data.
Understanding the Power of Payment Tokenization
Let's cut through the technical jargon. Tokenization isn't just another buzzword; it's a fundamental change in how businesses can protect customer payment information.
By replacing the Primary Account Number (PAN) with a randomly generated token, your organisation can process payments, handle refunds, and manage recurring billing without ever needing to store or transmit the vulnerable card details. This is especially vital in places like contact centres, where payments are often taken over the phone. Instead of an agent hearing or writing down a card number, the data is captured securely and instantly converted into a token, completely bypassing your internal systems.
Before we dive deeper, this table breaks down the core concepts you'll need to know.
Tokenization at a Glance Key Concepts
This table breaks down the core components of payment tokenization, providing a simple definition for each term before we explore them in detail.
| Concept | Simple Explanation | Primary Goal |
|---|---|---|
| Tokenization | The process of swapping a real PAN for a unique, non-sensitive token. | To remove actual cardholder data from a business's systems. |
| PAN (Primary Account Number) | The 16-digit number on the front of a payment card. This is the sensitive data. | To uniquely identify the customer's account for payment processing. |
| Token | The randomly generated, non-sensitive placeholder that replaces the PAN. | To act as a secure substitute for the PAN in business operations. |
| Token Vault | A highly secure, centralised server where the mapping between tokens and PANs is stored. | To protect the original card data, keeping it isolated and encrypted. |
With these terms in mind, it becomes clearer how the pieces fit together to create a powerful security framework.
The Growing Need for Secure Payments
The push for robust security like tokenization isn't just theoretical; it's driven by the sheer volume of payments happening every day. The UK payment ecosystem, for instance, has seen explosive growth, creating massive opportunities for secure payment technologies.
In one recent year, the UK processed 48.1 billion payments, a figure that jumped to 48.8 billion the following year. Debit cards made up the lion's share, accounting for 26.1 billion of those transactions. This growth across every channel—phone, web chat, video calls—only magnifies the risk of data breaches and proves why solutions that take sensitive data out of the equation are no longer a 'nice-to-have'.
Tokenization effectively devalues sensitive data. If a breach happens, criminals only get their hands on useless tokens, not actual card numbers they can sell or exploit. It turns a potential catastrophe into a far more manageable incident.
This proactive approach does more than just stop fraud in its tracks. It's the foundation for slashing complex compliance burdens, particularly the scope of the Payment Card Industry Data Security Standard (PCI DSS). When you can prove that real cardholder data never touches your network, you simplify audits, lower costs, and, most importantly, build unbreakable trust with your customers. It's a simple concept with a profound impact.
How Tokenization Works During a Live Transaction
To really understand what tokenization is in payments, it helps to move away from the theory and look at a real-world scenario. Let’s walk through the process step-by-step, using a typical contact centre payment as our guide. This everyday interaction is the perfect way to see how tokenization protects sensitive data right from the moment a customer decides to pay.
Picture this: a customer is on the phone with one of your agents to settle a bill. In a traditional, unsecured setup, this is a high-risk moment. The customer would read their 16-digit card number out loud, and the agent would type it directly into your system. That data is now exposed to potential interception, insecure storage, or even internal fraud.
This is exactly where tokenization changes the game.
The Customer Initiates a Secure Payment
Instead of verbally sharing their card details, the customer is asked to enter their card number (PAN), expiry date, and CVC using their telephone keypad. As they press the digits, a crucial security layer kicks in behind the scenes.
Technologies like DTMF (Dual-Tone Multi-Frequency) suppression work silently in the background. This clever tech ensures that the agent hears only flat, monotonous tones—not the distinct beeps that could give away the numbers being entered. The sensitive audio data is completely masked from the agent and, just as importantly, from any call recording software.
This simple step ensures raw cardholder data never even enters your business's environment. The agent isn't exposed to it, your systems don't touch it, and your call logs stay clean and compliant. It's the first and most vital step in shrinking your PCI DSS scope.
The Token Vault Creates the Token
The DTMF tones, now secured, are sent directly to a specialised, third-party provider known as a token vault. Think of this vault as a digital Fort Knox—an ultra-secure, PCI DSS Level 1 certified server environment built for one purpose: to safely handle and store sensitive payment data.
Once the vault receives the card details, it performs two key actions almost instantly:
- It generates a token. This is a unique, algorithmically created string of characters that has no mathematical link to the original card number. It’s a secure, non-sensitive stand-in.
- It stores the real card data. The original PAN and the newly created token are securely stored together inside the vault, creating a link between the two that only the vault can ever decipher.
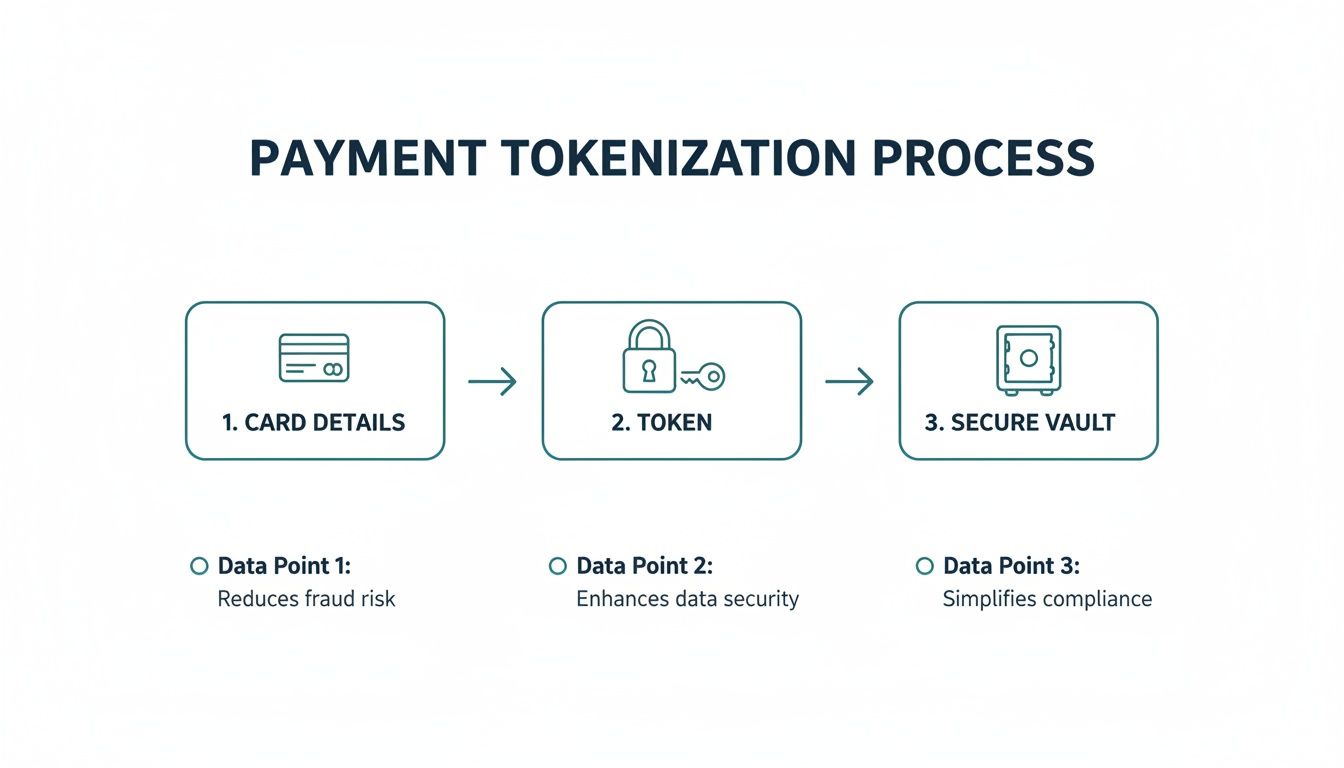
This diagram shows the basic flow, from capturing the card details to generating a token and locking it away safely.
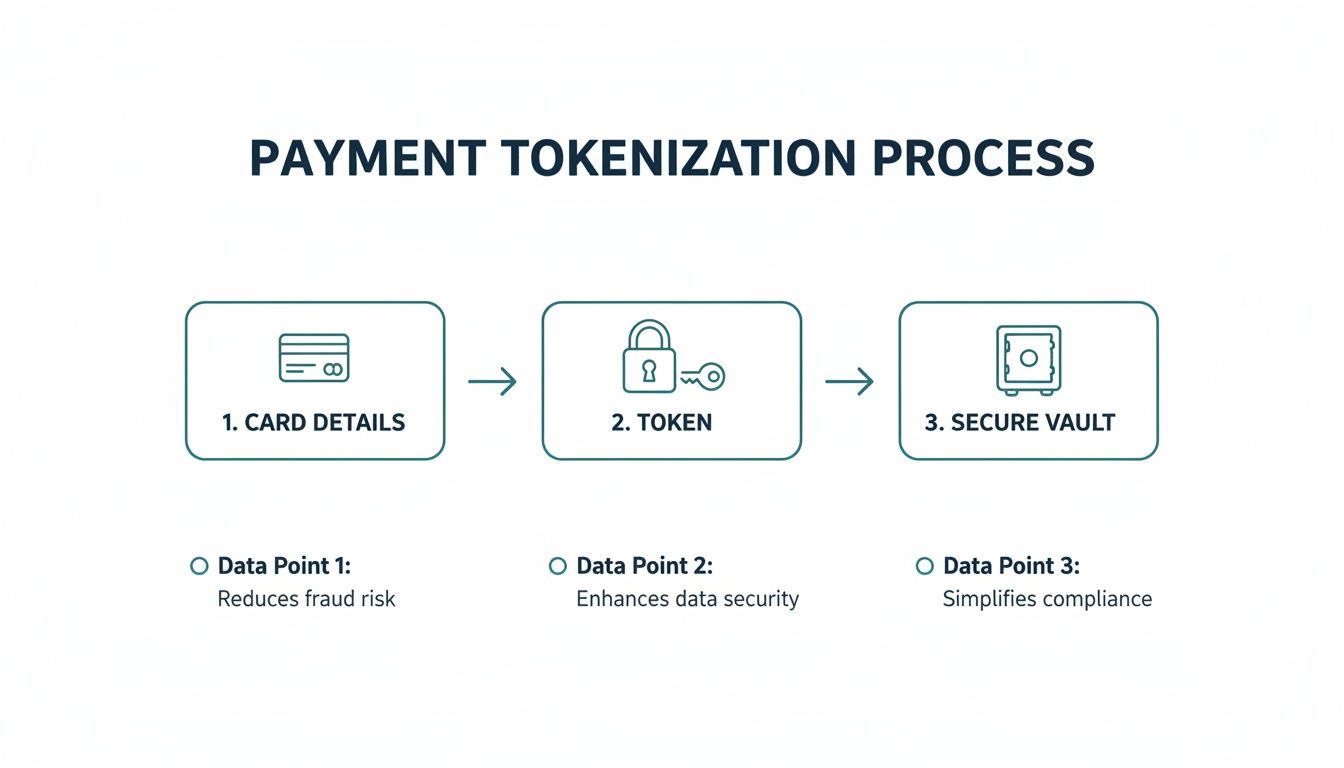
As you can see, the process effectively quarantines sensitive data, making sure it never touches the merchant's less secure systems.
The Token Is Used to Complete the Transaction
With the real card details safely locked away, the token vault sends the new token back to your agent’s payment application or CRM system. Your agent now sees this placeholder on their screen—not the customer’s actual card number.
The agent can now use this token to process the payment through your existing payment gateway. The gateway receives the token, forwards it to the payment processor, which then uses the token vault to retrieve the actual card data and authorise the transaction with the bank.
Throughout this entire journey, from the customer’s keypad entry to the bank authorisation, your business systems only ever deal with the token. If a data breach were to happen, hackers would find nothing more than a collection of useless placeholders, making the stolen information worthless on the black market.
This seamless, invisible process is the essence of effective payment tokenization, turning a high-risk interaction into a secure, compliant, and trustworthy customer experience.
Tokenization vs Encryption: Understanding the Crucial Difference
It’s a common mistake to use ‘tokenization’ and ‘encryption’ interchangeably. While both are heavy-hitting security tools, they protect your payment data in fundamentally different ways. Getting this distinction right is the first step toward building a truly secure payment environment for your business.
Encryption is a mathematical process that scrambles data, turning readable card details into an unreadable code. Think of it like locking a sensitive document inside a high-tech safe. The original document is still there, just protected by a complex lock only you have the key for.
If a fraudster gets their hands on the safe, they can’t read what’s inside without the correct key. The problem is, the valuable information still exists within your systems, albeit in a scrambled format. If that key is ever stolen or cracked, all that sensitive data can be unlocked and exposed.

How Tokenization Removes the Risk
Tokenization takes a completely different road. Instead of just scrambling the original data, it replaces it entirely with a non-sensitive placeholder—the token. The real, sensitive card data is removed from your systems altogether and stored securely in an external, certified token vault.
Let's use a better analogy. Instead of putting your document in a safe in your office, you deposit it at a high-security library and receive a unique library card in return. This card contains no sensitive information; it just acts as a reference to find the original document in the library's impenetrable vault.
If a thief steals your library card, it's useless to them. They can't access your document because they don't have authorised access to the library itself. In the same way, a stolen payment token has no real value and can't be mathematically reversed to reveal the original card number.
This simple but powerful difference is why tokenization is a game-changer for reducing both risk and the burden of compliance.
Comparing Tokenization and Encryption for Payment Security
To make the differences even clearer, let's put these two methods side-by-side. The table below breaks down how each one operates in a real-world payment scenario.
| Feature | Tokenization | Encryption |
|---|---|---|
| Data Format | The token has no mathematical link to the original card number. | The encrypted data is a scrambled version of the original card number. |
| Data Location | Sensitive card data is completely removed from your systems. | Sensitive card data stays in your systems, just in a protected state. |
| Security Impact | A data breach exposes only worthless tokens, not valuable card details. | A data breach that includes the encryption key could expose all card details. |
| PCI DSS Scope | Dramatically reduces scope by taking cardholder data out of your environment. | May not reduce scope as much, since encrypted data is still present. |
While encryption is vital for protecting data as it moves across networks (data in transit), tokenization is unbeatable at protecting data stored within your business environment (data at rest).
Ultimately, the best security strategies don’t pick one over the other—they use both. Encryption protects the token as it travels between your systems and the payment gateway, while tokenization ensures the most valuable prize—the customer’s actual card number—was never there to be stolen in the first place. This layered approach gives you robust protection against today's threats.
Why Adopting Tokenization Is a Business Game-Changer
It’s easy to get lost in the technical details, but the real story is why tokenization matters so much. This isn't just another security upgrade; it's a strategic move that delivers powerful, compounding benefits across your entire organisation, from simplifying regulations to building rock-solid customer loyalty.
The most immediate and significant win is a drastic reduction in your Payment Card Industry Data Security Standard (PCI DSS) scope. At its core, tokenization removes sensitive cardholder data from your systems entirely. When raw card numbers never enter or rest on your network, you can sidestep a huge chunk of the compliance burden.
This translates directly into lower costs and fewer resources tied up in maintaining PCI DSS compliance. Your team gets to focus on what they do best—growing the business—instead of navigating a maze of security controls for data you no longer have to protect. You can learn more about how this works by exploring our guide on what PCI compliance is and how Paytia takes care of it.

A Fortress Against Fraud and Breaches
With card data gone from your environment, your vulnerability to costly data breaches plummets. In a tokenized system, even if criminals manage to get inside your network, all they’ll find is a collection of useless, non-sensitive tokens. These placeholders have zero value outside of your specific payment ecosystem and can't be reverse-engineered to expose the original card number.
This simple shift turns a potential catastrophe into a much more manageable incident. The reputational damage and eye-watering financial penalties of a card data breach are severe, but tokenization acts as a powerful shield, devaluing the very asset criminals are hunting for.
Building Unbreakable Customer Trust
In an age of constant headlines about data theft, your customers are more savvy than ever about the risks of sharing their payment details. Showing them you’re serious about protecting their information is a powerful way to earn and keep their trust.
When you can confidently tell a customer their card details are never stored on your systems, it sends a clear message: their security is a priority. That trust is the bedrock of long-term loyalty and can easily become a key competitive advantage, encouraging repeat business and positive word-of-mouth.
"Adopting tokenization signals to your customers that their security is not an afterthought. It's a core part of your business ethos, transforming a transactional relationship into one built on confidence and peace of mind."
This isn’t just a nice-to-have; it's becoming the standard. The UK tokenization market generated USD 284.1 million in revenue in just one year and is projected to hit USD 929.0 million by 2030, growing at 18.4% annually. This boom shows just how many UK firms are turning to tokenization to tighten security and ease their compliance burden. You can find more details in the full research on the UK tokenization market.
Unlocking Operational Flexibility
Finally, the benefits of tokenization run deep into your day-to-day operations, creating smoother customer experiences without adding risk. Because tokens are safe to store, they enable a host of modern payment features:
- Effortless Recurring Billing: Charge repeat customers for subscriptions or services using their stored token, so they never have to re-enter their card details.
- Seamless One-Click Checkouts: Give returning customers a faster, frictionless checkout by recalling their tokenised payment method.
- Hassle-Free Refunds: Process refunds straight back to the customer’s card using the token, without ever needing to see the original PAN.
These capabilities let you offer the convenience customers now expect, all while maintaining the highest level of security. By separating operational ease from data risk, tokenization provides a secure foundation for growth and innovation.
Implementing a Tokenization Solution in Your Business
Deciding to bring payment tokenization into your business is a massive step forward for security and compliance. But where do you actually start? For most organisations, the journey begins with a fundamental choice: build your own system from scratch, or partner with a specialist provider.
Getting this decision right is crucial, and it boils down to your resources and priorities.
Building an in-house solution might sound like the ultimate in control, but it's a huge undertaking. You're looking at a serious investment in hardware, software, and a dedicated team of security experts. Plus, you’ll face the long, costly process of achieving and maintaining PCI DSS Level 1 certification. For all but the largest enterprises, this path is often too complex and expensive to be practical.
This is why partnering with a managed service provider like Paytia is usually the smarter route. These companies have already done the heavy lifting—building the certified, secure token vault and the infrastructure around it. This approach dramatically cuts down your implementation time, slashes upfront costs, and shifts the immense burden of PCI DSS compliance onto their expert shoulders.
Integrating Tokenization into Your Existing Systems
A big question we often hear is, "How will this fit with the systems we already have?" It’s a valid concern. Nobody wants to rip and replace the tools their teams rely on every day.
The good news is that a well-designed tokenization platform is built to be a seamless, secure layer that works with your existing setup, not against it.
Modern tokenization services are designed to plug right into the tools you already use, including:
- VoIP and Telephony Systems: The solution should integrate directly with your contact centre’s phone platform, using technology like DTMF suppression to securely capture payment details during calls.
- CRM and ERP Platforms: Tokens can be passed into and stored within your customer relationship management or enterprise resource planning software. This links secure payment capabilities directly to your customer records.
- Payment Gateways: Tokenization works alongside your existing payment gateway, allowing you to process transactions using secure tokens instead of raw card numbers. Our deep-dive on payment gateway API integration explains exactly how this works.
The bottom line? You gain all the security benefits of tokenization without having to force your team to abandon the technology they know and trust.
Managing Day-to-Day Operations with Tokens
So, what does life look like after tokenization is up and running? How does your team handle everyday tasks like refunds or retrying a failed payment? The answer is: more simply and more securely.
Because tokens are safe to store and reuse for follow-up actions, your team can manage payments without ever needing to see or handle sensitive card details again. A refund, for example, is triggered using the token from the original transaction, which tells the payment gateway to credit the customer's card.
If a transaction fails, the agent can simply retry the payment using the same secure token. A clear audit trail connects every tokenised transaction to a specific customer, agent, and result, giving you full visibility for reconciliation or customer service queries. All this happens while the real cardholder data remains safely locked away.
This secure, token-based approach is becoming the standard. We’re seeing regulators show increasing confidence in these kinds of advanced technologies. The launch of the UK's first fully regulated blockchain-based payment system, for instance, shows a growing comfort with new financial infrastructures that prioritise security. By choosing the right partner, you can implement a solution that not only protects your data but fits perfectly into your operational reality.
Tokenization Isn't Just a Feature—It's the Future
As we've explored, thinking about tokenization in payments goes far beyond a simple security checkbox. It’s a core strategy for any business looking to navigate an era of exploding transaction volumes and increasingly sophisticated fraud. Tokenization is no longer just a "nice-to-have" best practice; it's an essential part of the modern commerce engine.
The main takeaway should be clear: tokenization is not an optional extra. If your organisation processes payments—especially over high-risk channels like the phone—it’s the single most effective way to shield customer data, slash compliance headaches, and build a secure foundation for growth. The question is no longer if you should adopt it, but how to get it right.
Best Practices for Your Tokenization Strategy
When you decide to bring in a tokenization solution, success really boils down to a few key decisions. The aim is to get rock-solid security without turning your day-to-day operations upside down.
To make sure you nail it, focus on these three things:
- Choose a PCI DSS Level 1 Certified Provider: This one is non-negotiable. When you partner with a provider that holds the highest level of security certification, you effectively shift the compliance burden off your shoulders. It guarantees their entire infrastructure is rigorously audited and built for security from the ground up.
- Demand True Omnichannel Support: Your customers don't just live on one channel. They interact with you over the phone, on video calls, through web chat, and more. Your tokenization solution has to work flawlessly across every single one of them to close security gaps and deliver a consistent, trustworthy experience.
- Prioritise Seamless Integration: The solution must play nicely with your existing telephony, CRM, and payment gateway. A platform designed for easy integration means you get top-tier security without having to rip and replace the tools your team already knows and uses every day.
Building the Foundation for What's Next
Looking ahead, tokenization is much more than a defensive shield; it’s what makes innovation possible. It provides the secure underpinning for the next wave of payment experiences, from frictionless digital wallets to the emerging world of embedded and invisible payments. As commerce gets more deeply woven into our devices and daily lives, the ability to transact safely without ever exposing raw card data will be everything.
In a world where a data breach can shatter customer trust in a heartbeat, tokenization provides a critical layer of defence. It makes sensitive data worthless to thieves, turning a potential catastrophe into a manageable incident and proving to your customers that you take their security seriously.
Ultimately, the future of payments is one where security is invisible but absolute. By taking sensitive data out of the equation entirely, tokenization lets businesses get back to focusing on what matters: delivering value and building lasting customer relationships. It's the key to protecting your customers, simplifying your compliance, and creating a resilient, trustworthy payment ecosystem that's ready for whatever comes next.
Common Questions About Payment Tokenization
As you start to explore what payment tokenization is, a few questions always come up. It’s a big shift from how payments used to be handled, so getting your head around the details is the first step to making a smart decision. Here are some straightforward answers to the queries we hear most often from businesses like yours.
A common misconception is that implementing tokenization means overhauling your entire infrastructure. It's actually much simpler. When you work with the right partner, the service slots in as a secure layer that works with the tools your teams already use every day—your phone system, CRM, and payment gateway.
Can We Still Issue Refunds with Tokenization?
Yes, absolutely. In fact, this is one of the biggest wins for your operations team. Because a token acts as a permanent, secure stand-in for a customer's payment details, your team can easily process refunds without ever having to ask for the full card number again.
It's a simple, secure flow:
- Your agent finds the original transaction in your payment system.
- They kick off the refund using the stored token linked to that purchase.
- The request goes to your payment gateway, which uses the token to tell the customer’s bank to credit their account.
The actual card details never leave the secure token vault. This means your team can handle customer service efficiently without bringing security risks back into your environment.
With tokenization, you get to keep the operational ease of quick refunds and recurring billing, but you permanently offload the liability of storing actual card numbers. It neatly separates what your business needs to do from the data it shouldn't have to touch.
How Does Tokenization Impact the Customer Experience?
When it’s done right, tokenization makes the customer experience better—it's both faster and feels much more secure. Take a payment over the phone, for example. The customer just taps their card details into their telephone keypad. It’s usually quicker and far more private than reading numbers out loud to an agent.
This secure approach also builds a huge amount of trust. Customers are more aware of data security risks than ever before. Knowing their card details aren't being heard, written down, or stored by your company gives them real peace of mind. It transforms a moment that can be filled with anxiety into a smooth, professional interaction.
Is Tokenization Expensive to Implement?
When you weigh it against the catastrophic cost of a data breach or the constant drain of maintaining a large PCI DSS scope, tokenization is an incredibly smart investment. The fines, brand damage, and operational chaos that follow a breach can cripple a business.
Working with a provider like Paytia means you don't need a massive upfront investment in hardware, software, and specialised security teams. You're effectively plugging into an existing PCI DSS Level 1 certified infrastructure on a subscription basis. This turns what could be a huge capital expense into a predictable, manageable operating cost. The real ROI comes from slashing compliance costs, tightening up security, and earning greater customer trust.
Ready to see how tokenization can lock down your payments and simplify your compliance? Paytia provides a seamless, agent-assisted solution that works with your existing systems, keeping sensitive data out of your environment for good. Learn more at paytia.com.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
