
What Is a BT Payment Line and How Does It Work?
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
If you’ve ever tried searching for a “BT payment line,” you might have come up empty-handed. That’s because it’s not an official product. Instead, the term has become industry slang for any telephone system used to accept card payments—a nickname that stuck simply because BT has been such a huge player in the UK’s telecoms world for so long.
What People Really Mean by a BT Payment Line

It’s a classic case of a brand name becoming a generic term, like calling any vacuum cleaner a “Hoover” or any sticky tape “Sellotape.” When someone talks about a “BT payment line,” they’re just referring to the everyday act of taking credit or debit card details over the phone, no matter who actually provides the phone service.
This method is still incredibly common, especially in sectors that rely on direct, personal conversations with customers. For many businesses, it’s a quick and convenient way to close a sale or settle an account.
Why Do We Still Take Payments Over the Phone?
Even with the rise of slick online checkouts, phone payments are here to stay. There are some very practical reasons for this:
- Customer Comfort: Some people, particularly when making a large or complicated purchase, just feel more secure giving their details to an actual human being.
- Urgent Transactions: Think about contact centres handling debt collections or policy renewals. They need to be able to take payment right there and then to resolve the issue.
- Accessibility: Not everyone is comfortable with online payment portals, and many people still don't have reliable internet access. The phone is a trusted fallback.
The sheer dominance of BT's network explains how its name got attached to the practice. Back in 2022, BT’s network carried an incredible 12.3 billion minutes of calls, easily dwarfing its rivals. It’s no wonder the name became ingrained in the contact centre lexicon. You can explore more data about BT's market position on Statista.
The real problem isn't the phone line itself, but what happens during the call. As soon as a customer reads their card details out loud, that sensitive data enters your business environment, creating a huge security and compliance headache.
This is the crux of the issue. That data is now exposed to your agents, it gets captured on call recordings, and it might even touch your internal IT systems. This puts you on a direct collision course with data security standards like PCI DSS.
It's precisely why smart businesses are moving away from this old, insecure way of doing things and adopting secure telephone payment solutions that shield customer data from the moment it’s shared.
The Hidden Risks of Taking Payments by Phone

If you're handling card details over the phone without a secure system, you're essentially dealing with a leaky pipe in your data infrastructure. It's a setup where sensitive information can—and often does—escape at multiple points, creating huge security and compliance headaches for your entire operation.
Think about it. The moment a customer reads their card number aloud, it enters a surprisingly high-risk environment. Your agents can hear it. They might see it on their screen as they type it in. They might even jot it down on a piece of paper. Just one simple action, and that critical data has been exposed in three different ways.
But the biggest red flag? That sensitive payment information is almost certainly being captured directly on your call recordings. Storing recordings that contain full card numbers (PANs) and security codes (CVCs) is a clear-cut violation of the Payment Card Industry Data Security Standard (PCI DSS).
The Human Element and Data Exposure
Let’s be honest, people are often the weakest link in any security chain. Even with the best intentions, giving your team direct access to raw card data is just asking for trouble. A recent study found that a staggering 42% of small businesses suffered a cyber breach in the last year, with internal vulnerabilities being a major cause.
This old-fashioned, manual process opens your business up to a few key threats:
- Insider Threats: A disgruntled or dishonest employee could easily copy, sell, or misuse the card details they handle all day long.
- Accidental Exposure: An agent scribbles a card number on a sticky note and forgets about it, leaving it in plain sight on their desk.
- Targeted Attacks: Sophisticated social engineering tactics can trick even well-meaning staff into revealing information they shouldn’t have access to.
And it's not just about data breaches. A significant "hidden risk" is the direct hit to your revenue from simply not being able to answer the phone, which is a common problem in busy call centres. There's a lot of money lost from unanswered calls, and inefficient payment processes only make it worse.
At its core, the problem is simple: the more people and systems that touch sensitive data, the greater the risk of a breach. Traditional telephone payment methods put your staff, your systems, and your customers’ data directly in the line of fire.
Compliance Nightmares and Reputational Damage
Failing to lock this data down isn't just a security slip-up; it’s a massive compliance failure. The PCI DSS rules are crystal clear: you cannot store sensitive authentication data, like CVC codes, after a transaction is authorised. Capturing this stuff in your call recordings puts you in immediate breach of those rules.
The fallout from a data breach linked to an insecure BT payment line can be brutal. We're talking about hefty fines and penalties, of course, but the real killer is the catastrophic damage to your reputation. The customer trust you've spent years building can be wiped out in an instant. This is the fundamental problem that modern, secure payment solutions were built to solve.
Making Sense of PCI DSS for Telephone Payments
Trying to get your head around the Payment Card Industry Data Security Standard (PCI DSS) can feel overwhelming, like a puzzle with way too many pieces. But for any business that takes payments over the phone—using what some might call a BT payment line—it’s a reality you can't ignore. The good news? It doesn’t have to be a constant headache.
At its core, PCI DSS is simply a set of security standards. It’s there to make sure any company that accepts, processes, stores, or sends card information does so in a secure way. Think of it like the basic hygiene standards for a restaurant; it’s the minimum you need to do to keep your customers' payment data safe.
The moment a customer reads their card number over the phone, the responsibility for protecting that data lands squarely on your shoulders. This covers everything from the second you hear the numbers to how they're stored and who can access them.
The Power of Scope Reduction
If there's one concept you need to grasp to make PCI DSS manageable, it's scope reduction. The 'scope' is everything in your business that touches cardholder data—your people, your computer systems, and your internal processes. The bigger the scope, the more complicated and expensive compliance gets.
Picture that sensitive data as a bright light. Anything that light touches—a computer, a network, an employee—is immediately pulled into your PCI DSS scope. That means every one of them has to meet the full, rigorous set of security controls, which can be a massive operational drain.
Scope reduction is the art of shrinking the footprint of cardholder data within your business. If you can stop the payment details from ever entering your environment, you slash your compliance burden dramatically.
This is exactly where modern, secure payment technologies come into their own. They create a protective shield, intercepting sensitive data before it can ever reach your agents, your call recordings, or your internal network.
Key Technologies for Compliance
Ensuring PCI DSS compliance in a contact centre today isn't about ticking boxes or manual spot-checks. It's about using smart technology to design the risk out of the process from the very beginning. Two key pieces of tech make this happen:
- DTMF Masking: This technology intercepts the touch-tones (DTMF) a customer presses on their keypad to enter card details. The tones are shielded, so your agent hears nothing but a flat, single tone, and more importantly, nothing sensitive is ever picked up by call recording systems.
- Tokenization: This is a clever process that swaps a customer's real card number for a unique, non-sensitive placeholder called a token. You can then use this token for things like recurring payments or refunds without ever needing to see or store the actual card details again.
These aren't just fancy add-ons; they are fundamental building blocks for a truly secure payment process. By putting them in place, you can effectively lift your entire contact centre out of PCI DSS scope. If you want to dive deeper into the specific rules, you can learn more about the core PCI DSS requirements in our detailed guide. It’s a proactive move that turns compliance from a recurring problem into a solved one.
Comparing Legacy and Modern Secure Payment Methods
How you decide to handle payments over a BT payment line is one of those critical decisions that ripples through your entire operation, affecting everything from security and efficiency to the trust your customers have in you. The gap between outdated, manual methods and modern, secure solutions isn't just a small step—it's a massive leap into a safer, smarter way of doing business.
For years, companies have relied on clunky workarounds to try and tick the PCI DSS compliance box. These legacy methods, while well-intentioned, are fundamentally flawed. Why? Because they still allow sensitive card data to creep into the business environment, even if just for a moment. They're reactive, trying to patch security holes rather than preventing them from ever appearing.
The Old Guard: Legacy Workarounds
Think of legacy methods like trying to catch raindrops in a bucket during a storm. You might catch most of them, but leaks are pretty much inevitable. Two common approaches fall squarely into this category:
- Pause-and-Resume Recording: This is exactly what it sounds like. An agent has to manually stop the call recording when a customer reads out their card details, then remember to restart it afterwards. The entire process hinges on human action, which makes it incredibly prone to error. All it takes is for one agent to forget to hit 'pause', and you’ve got a serious compliance breach on your hands.
- Clean Rooms: This approach involves physically moving the payment part of the conversation to a separate, sterile environment. Agents have to leave their desks and head to a secure room with no phones, pens, or paper to process the transaction. While it isolates the data, it's a clumsy, expensive nightmare to maintain and creates a horribly disjointed experience for both the agent and the customer.
These methods don't just add friction; they add risk to every single transaction. They push up call handling times, demand constant staff training and oversight, and ultimately, they never solve the core problem: the exposure of card data to your people and systems.
A New Standard: Modern Automated Solutions
Modern secure payment platforms, like Paytia, take a completely different tack. Instead of trying to manage risk, they are built from the ground up to eliminate it entirely.
Modern solutions work on a simple but powerful principle: if sensitive data never enters your environment, you don’t have to worry about securing it. This completely flips the security dynamic from reactive damage control to proactive prevention.
These systems use clever technology to create a secure bubble around the payment process. Techniques like DTMF (the tones from a keypad) masking and channel separation ensure that card numbers never reach your agent's ears or your call recording systems. The data is intercepted, encrypted, and sent directly to the payment processor, completely bypassing your infrastructure.
This not only delivers a much higher level of security but also dramatically simplifies your PCI DSS compliance by shrinking what's known as your 'scope'.
To really see the difference, let’s put these two approaches side-by-side.
Legacy vs Modern Secure Phone Payment Solutions
The table below breaks down the practical differences between clinging to outdated methods and embracing a modern, secure, and compliant solution. The contrast is stark.
| Feature | Legacy Method (e.g., Pause-and-Resume) | Modern Solution (e.g., Paytia) |
|---|---|---|
| Security Level | Low to moderate; relies on manual intervention and is highly prone to human error. | High; uses end-to-end encryption and automation to prevent data exposure. |
| PCI DSS Scope | High; your agents, network, and call recording systems are all in scope. | Minimal; sensitive data never enters your environment, reducing scope by 90-95%. |
| Agent Experience | Clunky and stressful; agents are responsible for complex security procedures. | Seamless; agents remain in conversation while the customer enters details securely. |
| Customer Trust | Can feel awkward or unprofessional, potentially raising customer concerns. | Smooth and reassuring; demonstrates a clear commitment to data security. |
| Operational Impact | Increases average call handling times and requires extensive ongoing training. | Reduces call handling times and eliminates the need for manual compliance tasks. |
As you can see, the choice isn't just about technology—it’s about fundamentally changing your security posture from a liability to an asset.
How Modern Secure Payment Technology Works
To really get your head around how modern solutions protect something like a BT payment line, it’s worth popping the bonnet and looking at the core technologies making it all happen. These aren't just bits of clever software; they represent a complete change in mindset—moving from a model of managing payment risk to one of eliminating it entirely.
This shift is powered by a few key technologies working together. They essentially create a secure bubble around the payment process, making sure that sensitive information never even grazes your internal systems. This approach doesn't just bolt the doors on security; it actually makes your operations much simpler.
Shielding Data with DTMF Masking
One of the smartest tools in the box is DTMF (Dual-Tone Multi-Frequency) masking. Think of it as an invisible shield for the keypad tones a customer presses when entering their card details. As a customer taps in their card number, the DTMF masking tech intercepts these tones before they can reach the call agent or your call recording system.
So, instead of hearing those giveaway beeps, the agent just hears a flat, continuous, monotone sound. It’s a simple but incredibly effective technique that ensures no card information is ever heard by your staff or captured on recordings. That alone is a massive step towards easy PCI DSS compliance.
The Power of Tokenization
Next up is another critical piece of the puzzle: tokenization. The best way to picture this is like a secure cloakroom for your customer’s card data. When a payment goes through, the real card number is instantly swapped for a unique, randomly generated placeholder, known as a "token."
This token acts as a secure reference to the original card details, which are stored safely in a PCI-compliant vault managed by the payment provider. You can then use this non-sensitive token for future transactions, like recurring billing or refunds, without ever needing to handle the real card number again.
This infographic does a great job of comparing the old, risky methods with the modern, secure technologies that protect businesses today.
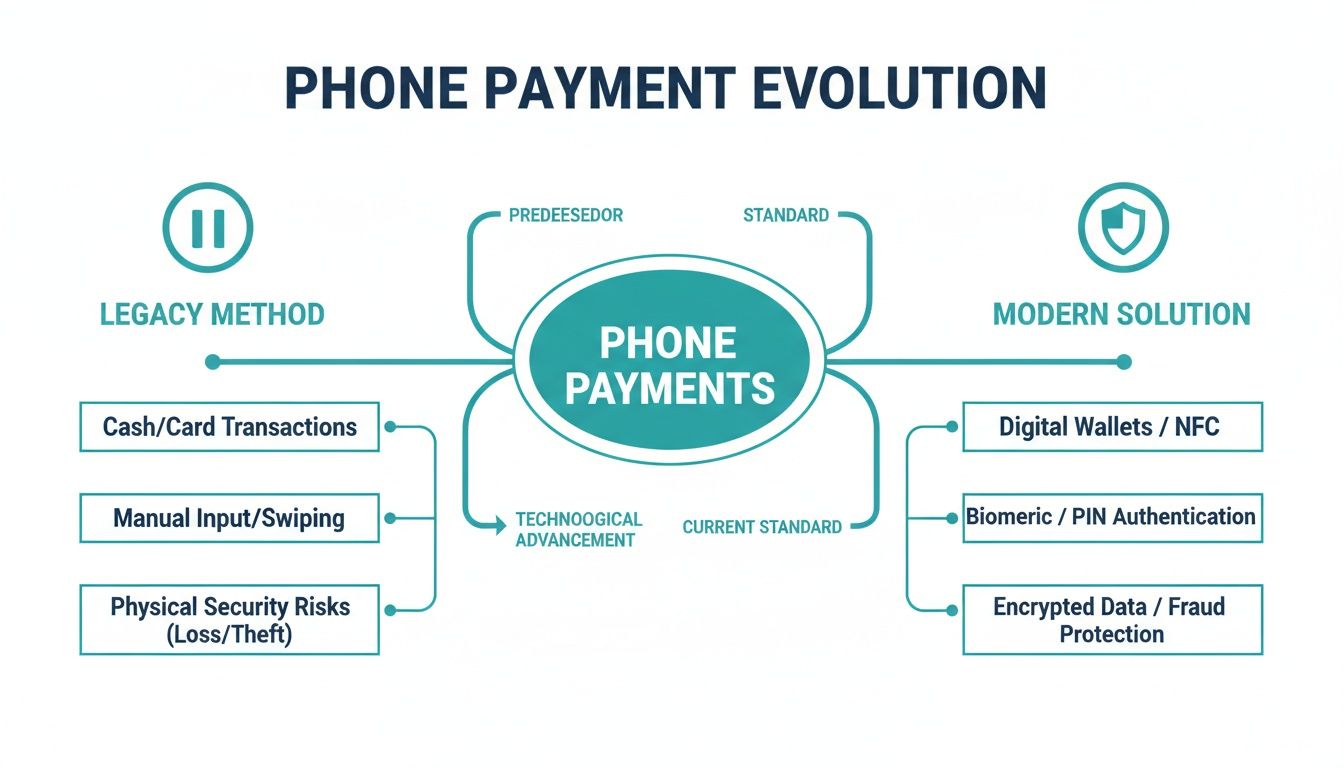
You can see how modern solutions completely remove the business from the flow of sensitive data. It’s a world away from legacy methods, where data exposure is a constant headache.
Separating Voice and Payment Data
Finally, there’s a clever technique called channel separation. This method intelligently splits a single phone call into two separate streams: one for the voice conversation and another just for the payment data. The agent and customer can carry on talking without interruption, while the card details travel down a completely separate, secure, and encrypted path straight to the payment gateway.
This separation is vital. It means the payment information completely bypasses your company's phone systems and network. The data never crosses your servers, never gets stored in your systems, and is never captured in your call recordings. To see how this applies to automated systems, have a look at our guide on the IVR payment flow.
The beauty of these technologies is that they're designed to overlay neatly onto the phone systems you already have. There’s no need to rip out your current setup, making the switch to a secure, compliant payment process both straightforward and cost-effective.
Choosing the Right Secure Payment Solution
Picking a partner to handle your telephone payments is about so much more than just ticking a compliance box. The best solutions don't just secure your transactions; they turn your entire payment process from a headache into a real business asset. It's about solving bigger operational problems, from chasing late payments to making your team more efficient.
Think of it like choosing between a simple padlock for your front door and a fully integrated smart security system. Sure, the padlock does a basic job. But the proper system protects everything, gives you useful insights, and just makes life easier. That's what a modern payment solution should do for your contact centre.
Core Criteria for Your Shortlist
When you're weighing up your options, a few non-negotiable features should be at the very top of your list. These are the fundamentals that separate a genuinely secure, effective platform from a flimsy workaround.
- PCI DSS Level 1 Certification: This is the gold standard from the Payment Card Industry. It means the provider’s entire setup has been through exhaustive, independent audits to meet the toughest security rules. Anything less is a gamble you don't want to take.
- Seamless CRM and Gateway Integration: The last thing you need is more complexity. Your chosen solution has to play nicely with the systems you already rely on every day. Look for ready-made integrations with major payment gateways and CRMs to avoid painful, custom development projects.
- True Omnichannel Support: Customers expect to pay how they want, when they want. A top-tier provider will offer a single, unified platform that secures payments whether they come from a voice call, an IVR system, a web chat, or even payment links sent by SMS or email.
Beyond Security: Improving the Experience
A secure BT payment line solution shouldn't mean a clunky experience for your customers or agents. In fact, the right technology makes it better for everyone. The process should feel smooth and professional, giving customers the confidence that their data is in safe hands.
For your agents, it's a huge weight off their shoulders. They're no longer handling toxic card data, which means less stress and less personal risk. They can focus on the customer conversation without having to remember fiddly steps like pausing call recordings. The result? Shorter call times, happier agents, and better service.
The goal is to find a partner that turns a compliance necessity into a competitive advantage. The right solution should not only protect data but also actively improve cash flow, reduce operational overheads, and enhance customer trust.
Finding a Partner, Not Just a Product
Ultimately, you’re not just buying software; you’re looking for a strategic partner who gets the unique pressures of your contact centre. They should bring more to the table than just technology—they should offer genuine expertise on how to streamline your payment workflows and get the best return on your investment.
Look for a provider whose features are designed to solve real-world business problems:
- Automated Payment Reminders: Imagine having tools that automatically chase down late payments. This can massively improve your collection rates while freeing up your team from tedious manual follow-ups.
- Robust Reporting and Analytics: Getting easy access to detailed transaction data helps you spot trends, track performance, and make smarter business decisions.
- Support for Modern Payment Methods: When a provider offers things like Identity Verified Pay by Bank using open banking, it shows they’re thinking ahead and future-proofing your payment options.
By focusing on these key areas, you can choose a secure payment solution that not only handles today’s compliance demands but also helps you build a more efficient, resilient, and trusted business for the future.
Ready to transform your telephone payments from a risk into an asset? Paytia provides a PCI DSS Level 1 certified platform that secures payments across voice, chat, and IVR without sensitive data ever touching your environment. Discover how our seamless solution can reduce your compliance scope and enhance your customer experience. Learn more about Paytia's secure payment solutions.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
