
A Practical Guide to PCI DSS Requirements
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
If you take card payments, you’ve probably heard of the Payment Card Industry Data Security Standard (PCI DSS). It’s a set of security rules that every single organisation accepting card payments has to follow. It’s not a law passed by parliament, but think of it as a critical contract you have with the card brands like Visa and Mastercard. Get it wrong, and you could be looking at serious financial penalties and a major blow to your reputation.
Demystifying Your Core PCI DSS Requirements
At its heart, PCI DSS is all about one thing: protecting sensitive cardholder data from falling into the wrong hands. Imagine your business has a high-security vault. Any system that stores, processes, or transmits card information—your payment terminals, e-commerce site, or even your call centre phone systems—sits inside this vault. This protected zone is called the Cardholder Data Environment (CDE), and the whole point of PCI DSS is to make that vault impenetrable.
The standard itself gives you a detailed roadmap for securing your CDE, broken down into 12 core requirements.
The Six Control Objectives
To make things a bit easier to digest, those 12 requirements are neatly grouped into six logical categories, known as control objectives. These are the pillars of a secure payment setup:
- Build and Maintain a Secure Network and Systems: This is your first line of defence, creating a strong barrier between your internal network and the outside world.
- Protect Cardholder Data: This focuses on locking down any stored data using strong encryption and other safeguards.
- Maintain a Vulnerability Management Programme: You can't just set and forget. This means actively hunting for and patching security weaknesses in your systems.
- Implement Strong Access Control Measures: Simply put, only the right people should be able to access sensitive data, and this objective ensures that’s the case.
- Regularly Monitor and Test Networks: This involves keeping a constant eye on your security systems to spot and stop breaches before they happen.
- Maintain an Information Security Policy: This brings it all together by establishing formal security rules that everyone in the organisation has to follow.
The guiding principle is straightforward: if you don’t absolutely need the data, don’t store it. And if you have to store it, protect it like your business depends on it—because it does. Getting this mindset right is the first real step toward compliance.
For any UK business, whether you're a busy contact centre or a small online shop, getting to grips with these pci dss requirements isn't optional. Failing to comply doesn't just put you at risk of fines; it chips away at the customer trust you’ve worked so hard to build.
Each of the 12 requirements provides a crucial layer of defence against increasingly clever cyber threats. A great starting point is to review a detailed PCI DSS compliance checklist which helps break down these essential steps. In this guide, we'll walk through each requirement one by one, giving you the practical insights needed to turn compliance from a headache into a genuine business asset.
A Detailed Breakdown of the 12 Core Requirements
The Payment Card Industry Data Security Standard is built around six core security goals, which are then broken down into 12 specific requirements. It’s helpful to think of the goals as the "why" and the requirements as the "how." Each one tackles a different piece of the data security puzzle, working together to build multiple layers of defence around sensitive cardholder information.
This structure shows that compliance isn’t about chasing after 12 random rules. It’s about achieving six clear security outcomes, from building a fortress-like network to maintaining a rock-solid security policy.
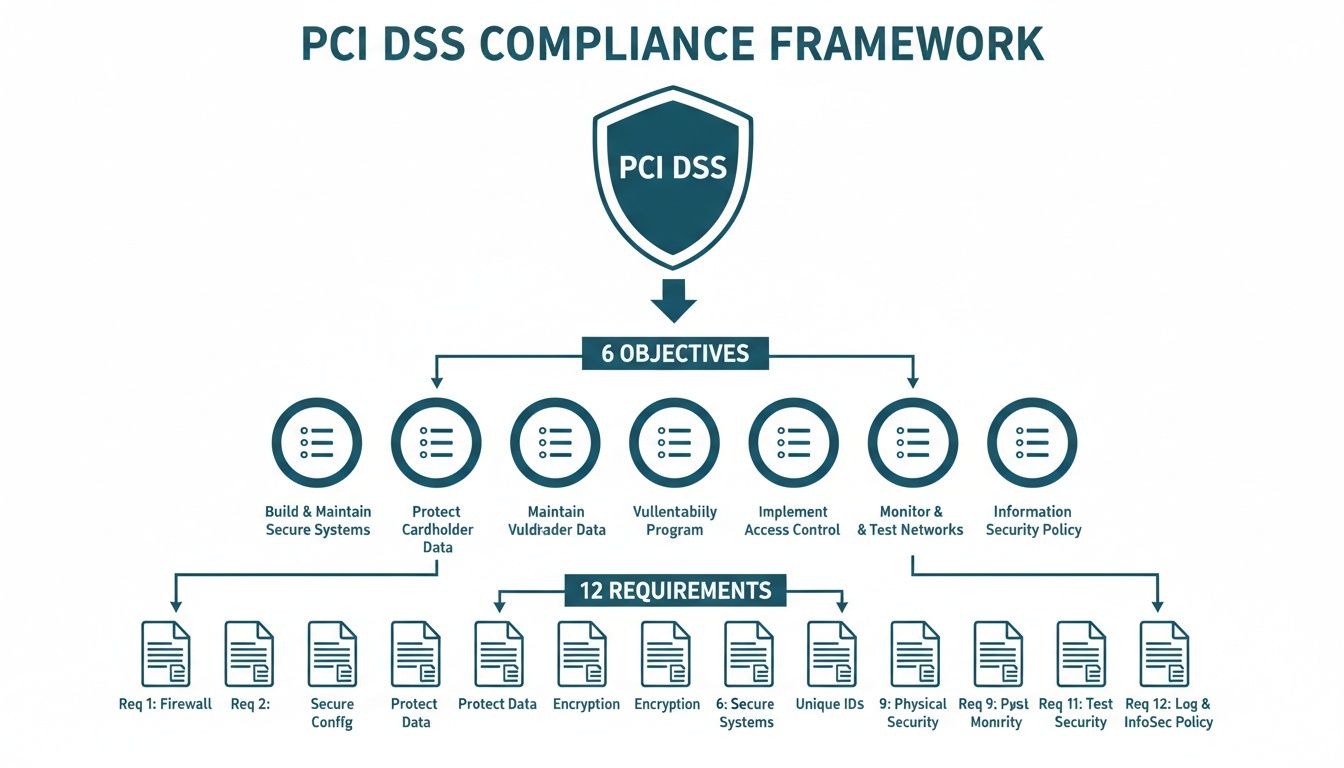
The table below gives you a quick overview of how these pieces fit together.
The 12 PCI DSS Requirements and Their Objectives
This table summarises the six control objectives and the 12 core requirements that fall under each, providing a clear and organised reference.
| Control Objective | Requirement Number | Requirement Description |
|---|---|---|
| Build and Maintain a Secure Network and Systems | 1 | Install and Maintain Network Security Controls |
| 2 | Apply Secure Configurations to All System Components | |
| Protect Cardholder Data | 3 | Protect Stored Account Data |
| 4 | Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks | |
| Maintain a Vulnerability Management Programme | 5 | Protect All Systems and Networks from Malicious Software |
| 6 | Develop and Maintain Secure Systems and Applications | |
| Implement Strong Access Control Measures | 7 | Restrict Access to System Components and Cardholder Data by Business Need to Know |
| 8 | Identify Users and Authenticate Access to System Components | |
| 9 | Restrict Physical Access to Cardholder Data | |
| Regularly Monitor and Test Networks | 10 | Log and Monitor All Access to System Components and Cardholder Data |
| 11 | Test Security of Systems and Networks Regularly | |
| Maintain an Information Security Policy | 12 | Support Information Security with Organisational Policies and Programmes |
Now, let's dig into what each of these really means in practice, especially for a contact centre.
Goal 1: Build and Maintain a Secure Network and Systems
This first goal is all about building a strong perimeter around your Cardholder Data Environment (CDE). Think of it as constructing strong walls and installing secure doors on your digital property to keep intruders out.
Requirement 1: Install and Maintain Network Security Controls
This is your first line of defence. It’s about installing and maintaining firewalls and other network controls to guard your CDE. A firewall acts as a gatekeeper, inspecting every bit of traffic coming into and out of your network and only letting legitimate communications pass.
For a contact centre, this means setting up your firewalls to block unauthorised access to the systems handling payments, like agent desktops or your CRM platform. It also involves documenting all your firewall rules and reviewing them at least every six months to make sure they're still doing their job effectively.
Requirement 2: Apply Secure Configurations to All System Components
Default settings are a hacker’s best friend. Many vendors ship hardware and software with generic, well-known passwords and settings just to make installation easier. This requirement forces you to change all vendor-supplied defaults and remove or disable any unnecessary functions before a system goes live in your environment.
This is why you never use passwords like "admin" or "password123." It’s also about creating a master blueprint—a configuration standard—for all your system components, ensuring every server, router, and application is hardened against common attacks right from day one.
Goal 2: Protect Cardholder Data
Once your perimeter is secure, the next job is to protect the data itself, whether it’s sitting on your systems or flying across a network.
Requirement 3: Protect Stored Account Data
The easiest way to protect cardholder data? Don’t store it in the first place. If you don't have a solid business reason to keep it, your policy should be to get rid of it securely.
If you absolutely must store cardholder data, this requirement lays down the law on how to do it. The full Primary Account Number (PAN) must be rendered unreadable wherever it is stored, which usually means using strong cryptography like encryption or tokenization.
Key Takeaway: You should never, under any circumstances, store sensitive authentication data after a transaction is authorised. This includes the full magnetic stripe data, the three-digit CVV code, or PINs. Storing this data is a direct and serious violation of PCI DSS.
For example, on a customer receipt or in a CRM system, the PAN should be masked so only the first six and last four digits are visible (e.g., 411111******1111). This simple step prevents unauthorised staff or attackers from getting their hands on the full card number.
Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks
When cardholder data travels over open networks like the internet, it’s vulnerable to being snooped on and intercepted. Requirement 4 demands that you use strong cryptography and security protocols to protect this data while it’s in transit.
This is why you see "HTTPS" on payment websites—it's a clear signal that the connection is encrypted. In a contact centre, this rule also applies to any data sent between your systems and your payment processor, making sure that information is unreadable to anyone who might be listening in.
Goal 3: Maintain a Vulnerability Management Programme
Security isn't a "set it and forget it" task; it's an ongoing process of finding and fixing weaknesses. This goal is all about keeping your systems resilient against new and emerging threats.
Requirement 5: Protect All Systems and Networks from Malicious Software
Malware—including viruses, worms, and ransomware—is a constant threat. This requirement insists that you deploy anti-virus software on all systems that are commonly targeted by malicious software.
Your anti-virus tools must be kept up-to-date with the latest threat definitions and configured to run periodic scans. This ensures that any new malware that manages to sneak onto a system is spotted and stamped out quickly.
Requirement 6: Develop and Maintain Secure Systems and Applications
Security needs to be baked into your systems and applications from the very beginning, not bolted on as an afterthought. This requirement focuses on the secure development of applications and, crucially, the timely patching of all your systems.
Industry reports consistently show that vulnerabilities in web applications are a leading cause of data breaches. To meet this requirement, you must:
- Install critical security patches from vendors within one month of release.
- Develop software securely, whether it's built in-house or by a third party, following industry best practices.
- Address common coding vulnerabilities in your software development processes to shut down potential attack vectors.
Goal 4: Implement Strong Access Control Measures
This goal is built on a simple but powerful principle: people should only have access to the data and systems they absolutely need to do their jobs. Nothing more.
Requirement 7: Restrict Access to System Components and Cardholder Data by Business Need to Know
This is the principle of "least privilege" in action. Access to the CDE should be strictly limited to personnel whose job demands it. For instance, a contact centre agent might need to initiate a payment, but they should never have access to the database where encrypted card numbers are stored.
Every person and every system should have the bare minimum level of access needed. This dramatically reduces the risk of both accidental data exposure and malicious insider threats.
Requirement 8: Identify Users and Authenticate Access to System Components
To control who gets in, you first have to know who they are. Requirement 8 ensures that every individual with access to the CDE has their own unique ID. This means no shared accounts like "agent" or "admin."
On top of that, access must be authenticated. This involves using strong passwords, implementing multi-factor authentication (MFA) for all access into the CDE, and making sure user sessions automatically lock after a period of inactivity.
Requirement 9: Restrict Physical Access to Cardholder Data
Digital security is only half the battle. This requirement is about locking down the physical locations where cardholder data is handled or stored. This includes not just servers and databases, but even paper records.
Common sense controls here include:
- Using cameras to monitor sensitive areas like server rooms.
- Implementing entry controls like key cards to restrict access.
- Maintaining visitor logs to track who comes and goes.
- Securely destroying media (both digital and paper) when it’s no longer needed.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you can't see. This goal is all about continuously watching your environment for suspicious activity and regularly testing your security controls to make sure they actually work.
Requirement 10: Log and Monitor All Access to System Components and Cardholder Data
Logging is absolutely vital for detecting, investigating, and responding to a security incident. This requirement means you must have audit trails that link all access to system components back to an individual user.
These logs must be reviewed regularly to spot anything unusual that could signal a breach. Most organisations use automated tools to analyse log data and generate alerts for suspicious events, like a flurry of failed login attempts.
Requirement 11: Test Security of Systems and Networks Regularly
You have to constantly poke and prod your own defences to find weaknesses before an attacker does. This includes conducting quarterly internal and external network vulnerability scans by an Approved Scanning Vendor (ASV).
It also involves performing penetration testing, which is basically a simulated attack on your environment to find exploitable security holes. These tests help you find and fix gaps proactively.
Goal 6: Maintain an Information Security Policy
Finally, a strong security posture depends on having clear, documented policies that everyone in the organisation understands and follows.
Requirement 12: Support Information Security with Organisational Policies and Programmes
This final requirement ties everything together. You must establish, publish, maintain, and share a comprehensive information security policy that governs how you protect cardholder data.
This policy should be reviewed at least once a year and updated whenever things change. It must clearly define security responsibilities for all personnel and include a formal security awareness programme to ensure your staff understand their role in protecting customer data. A practical incident response plan is also a critical piece, outlining the exact steps to take if the worst happens and a data breach occurs.
How to Scope and Validate Your Compliance
Getting the 12 requirements in place is a huge milestone, but it’s only half the story. The other half is proving you’ve done it right through a formal validation process. But before you even think about validation, you have to get your scoping right.
Scoping is all about identifying every single person, process, and piece of technology that touches—or could even affect the security of—cardholder data. Think of it as drawing a tight, clear boundary around everything sensitive. This "map" of your Cardholder Data Environment (CDE) defines what’s in scope. Everything inside that line, from servers and laptops to network gear and apps, is subject to the full force of the pci dss requirements.
Don’t mistake this for a simple box-ticking exercise. Nailing your scoping is the single most powerful thing you can do to lighten your compliance load. If you can intelligently isolate your payment systems from the rest of your network, you can shrink your CDE down dramatically. A smaller CDE means fewer systems to audit, which is the cornerstone of any smart compliance strategy.
Choosing Your Validation Method
Once you've drawn that boundary, it's time to prove your controls are working. The method you’ll use boils down to your transaction volume, a threshold set by the major card brands. This leads you down one of two main paths.
- Report on Compliance (RoC): This is the full-blown, on-site audit. A Qualified Security Assessor (QSA) comes in and does a deep dive into your controls, policies, and procedures, culminating in a detailed formal report.
- Self-Assessment Questionnaire (SAQ): This is a self-validation tool where you report on your own PCI DSS assessment. It’s essentially your declaration that you have the right controls in place.
For most businesses, particularly small to medium-sized ones, the SAQ is the standard route. But here’s the catch: not all SAQs are created equal. There are several different versions, each designed for a specific way of handling payments.
Understanding the Different SAQ Types
The type of SAQ you need to fill out depends entirely on how you handle card data. Picking the right one is absolutely critical because the complexity varies wildly between them.
Here’s a quick look at a few common examples:
- SAQ A: The simplest of them all. This is for merchants who have completely outsourced all cardholder data functions to a compliant third party. If you run an e-commerce store with a fully hosted payment page and never see the card data yourself, this is for you.
- SAQ B-IP: For merchants who only use standalone, IP-connected payment terminals.
- SAQ C: Aimed at merchants with payment application systems connected to the internet, but who don’t store any electronic cardholder data.
- SAQ D: This is the beast. It’s the most comprehensive and complex SAQ, covering all 12 PCI DSS requirements. If you don't fit into any of the other SAQ types—especially if you store card data electronically—you land here.
A key goal for any contact centre is to structure its payment processes to qualify for the simplest SAQ possible. Moving from the demanding SAQ D to a much simpler version can reduce the number of applicable controls by over 90%.
In the UK, the PCI DSS requirements are tiered based on transaction volume. Level 1 merchants, processing over six million transactions a year, must face a full RoC. However, many UK businesses fall into levels where an SAQ is the norm. A study of UK contact centres found that 27% face significant direct compliance costs, while a staggering 7% stopped taking card payments altogether because of the complexity.
This doesn't have to be the case. Modern technologies like DTMF suppression and tokenisation can shrink the audit scope so effectively that businesses can shift from the dreaded SAQ D to a much simpler version, slashing their compliance costs in the process.
Ultimately, getting your CDE scoped accurately and choosing the right validation method are your foundational steps. They set the tone for your entire compliance journey, making it far more manageable and cost-effective. To get a wider view on how this fits into the bigger picture, it's worth exploring some general compliance principles.
Reducing PCI Scope in Your Contact Centre
Facing up to all 12 PCI DSS requirements can feel like an impossible mountain to climb, especially when your contact centre is juggling payments across different channels. But here's the secret: the key to manageable compliance isn't just about bolting on more controls. It's about strategically shrinking your Cardholder Data Environment (CDE) from the outset.
Think of your CDE as a high-security vault. The smaller that vault is, the easier and cheaper it is to guard. By making sure sensitive card data never even touches your internal systems, you effectively shrink the vault down to a manageable size, dramatically cutting your compliance workload.

Core Technologies for De-Scoping
Several powerful technologies are built specifically to keep card data out of your environment. This approach is a bit like using a secure courier to handle a valuable package—the payment data—without you or your agents ever needing to touch it.
- DTMF Suppression (Masking): When a customer types their card number on their phone keypad, this tech intercepts the Dual-Tone Multi-Frequency (DTMF) tones and masks them. Your agents and call recordings only pick up flat, unrecognisable beeps, meaning your entire telephony system is kept out of scope.
- Tokenization: This clever process swaps the raw Primary Account Number (PAN) for a unique, non-sensitive stand-in called a "token." This token can be stored and used for things like recurring billing without ever exposing the real card details.
- End-to-End Encryption (E2EE): For digital channels like web chat or video, E2EE scrambles the card data the instant the customer enters it. It's only decrypted once it reaches the secure payment processor. To your systems, it's just encrypted gibberish.
By implementing these technologies, you can effectively de-scope huge chunks of your infrastructure. Systems like agent desktops, CRM platforms, and call recorders no longer store, process, or transmit cardholder data, removing them from the punishing demands of a PCI audit.
Channel Separation and Secure Payment Platforms
The most bulletproof strategy combines these technologies inside a secure, isolated payment platform. This is the whole idea behind channel separation, where the payment itself is diverted to a secure, compliant pathway that’s completely separate from your day-to-day communication channels.
For instance, during a phone call, the agent can trigger a secure payment mode. The customer then enters their details directly into this secure channel, completely bypassing the agent and the call recording system. The agent can see the payment progressing but never sees or hears the actual card information.
To get a better feel for the subtle differences and advantages, it’s worth exploring a detailed comparison between channel separation and DTMF suppression to figure out what best suits your operations.
The Practical Impact of Scope Reduction
Getting your PCI scope under control delivers real business benefits that go way beyond ticking a compliance box. The biggest win is the ability to move from the most complicated Self-Assessment Questionnaire, SAQ D, to the much, much simpler SAQ A.
Just look at the difference that makes:
- SAQ D forces you to prove compliance against over 300 individual PCI DSS controls. It's a colossal project that eats up time, money, and technical expertise.
- SAQ A, which is for businesses that fully outsource their card data handling, has fewer than 30 controls to worry about.
Making that switch can slash your direct compliance effort by up to 95%. That means lower audit costs, less pressure on your IT teams, and a faster, cleaner path to proving you're compliant. Even more importantly, it crushes your risk profile. If you never handle the data, you can't lose it in a breach.
The Real Cost of Getting PCI Compliance Wrong in the UK
It’s one thing to get your head around the technical details of the PCI DSS requirements, but it’s another thing entirely to understand the brutal financial and reputational damage that comes from a breach. Many businesses mistakenly believe that because PCI DSS isn't a formal UK law, the penalties are just a slap on the wrist. That’s a dangerously wrong assumption.
While it’s true that PCI DSS isn’t written into UK statute, any serious breach involving cardholder data can land you in hot water with the Information Commissioner’s Office (ICO) under UK GDPR and the Data Protection Act 2018. Suddenly, you're facing financial consequences far bigger than you ever imagined.
The Penalties Pile Up Quickly
The cost of non-compliance isn't a single fine; it's a painful layering of penalties, each adding to the financial burden. A breach triggers a chain reaction, with fines coming at you from all sides.
- Hefty Card Scheme Fines: Payment giants like Visa and Mastercard will hit your acquiring bank with substantial fines, which are always passed straight on to you. These can run from thousands to hundreds of thousands of pounds every month until you fix the problem.
- Massive Regulatory Sanctions: This is where it gets really serious. The ICO has the power to fine you up to £17.5 million or 4% of your global annual turnover – whichever figure is higher.
- Forced Forensic Audits: After a breach, you'll almost certainly be forced to pay for a costly and invasive investigation by a PCI Forensic Investigator (PFI), who will pick apart your systems to find out exactly what went wrong.
The Lingering Damage of a Breach
Beyond the immediate fines, the secondary costs can be just as crippling. You’ll be on the hook for reissuing every compromised card, covering fraudulent transactions, and scrambling with PR agencies to try and save your brand’s reputation.
But losing your customers' trust? That’s the real killer. A single data breach can wipe out years of brand loyalty in an instant, sending customers running to competitors they feel they can trust. This long-term commercial damage often hurts far more than the initial financial penalties.
Think of robust PCI compliance not as an expense, but as an insurance policy against a catastrophic business failure. The investment in prevention is always a tiny fraction of the cost of a cure.
The overlap between card scheme rules and UK regulation makes this a high-stakes game. In the UK, card-not-present fraud—which covers all your phone and online sales—makes up over 70% of all card fraud. For a UK business with a £50 million turnover, a major breach could easily trigger a £2 million GDPR fine before the card brands even start sending their own invoices. You can explore a deeper dive into how UK businesses can avoid these common mistakes and their costly outcomes.
This is precisely why getting sensitive data out of your environment is the smartest move you can make. Technologies that prevent card details from ever touching your core systems can shrink your audit scope by 90–95%. This drastically cuts the risk that a single weak point could blow up into a headline-making breach with regulator-sized fines.
Common Pitfalls and Preparing Audit-Ready Evidence
Getting through the pci dss requirements is one thing, but proving your compliance to an auditor is a completely different ball game. It’s where many organisations fall down. The surprising part? It’s often not because their security controls are weak, but because their evidence is a mess—disorganised, incomplete, or just plain confusing.
The path to a smooth audit is littered with common, avoidable mistakes.

The classic pitfalls usually boil down to the fundamentals. We see it all the time: improper network segmentation. A failure to properly fence off the Cardholder Data Environment (CDE) blows your audit scope wide open, making a manageable task a nightmare. Another common tripwire is weak logging and monitoring, which leaves your security team flying blind and unable to produce the audit trails an assessor needs to see.
Building Your Evidence Locker
Think of your compliance evidence like a perfectly organised binder you’d hand to a financial auditor. It must be clear, current, and complete. Auditors don't just take your word for it; they need documented proof that your controls are working day in, day out. This isn’t about a last-minute scramble before they arrive—it's about continuous, diligent record-keeping.
Your evidence locker should contain a few non-negotiables:
- Up-to-Date Network Diagrams: A clear visual map of your network, showing the CDE boundary and every connection in and out.
- Data Flow Diagrams: Illustrations that trace the entire journey of cardholder data as it moves through your systems.
- Security Policies and Procedures: The formal rulebook for everything from who gets access to what you do when something goes wrong.
- Scan and Test Results: Proof of your quarterly vulnerability scans and annual penetration tests.
So many businesses treat compliance like a project with a start and finish line. That’s a huge mistake. It has to be a constant programme of monitoring, testing, and documenting. Your evidence needs to reflect that ongoing effort, not a last-ditch attempt to get organised.
From Theory to Audit-Ready Reality
Having policies on a shelf gathering dust is useless. You have to prove they’re being followed. Adopting strong document management best practices is the only way to keep your evidence organised, accessible, and ready for scrutiny. This means maintaining logs, staff training records, and change control documents meticulously.
Of course, you'll also need a skilled team to present this information. Our guide on finding the right PCI compliance auditor can help you prepare for that critical conversation.
Recent cyber-attacks in the UK have shown just how devastating it can be when these controls fail. The Co-Op confirmed that a breach exposed the data of over 6.5 million customers—a stark reminder of how poor segmentation can escalate a small incident into a colossal data loss.
For UK firms, the stakes are high. Acquirers can impose monthly fines from £5,000 to £100,000 for non-compliance, and that's before you even factor in fraud liability. For contact centres, securing payment flows isn't just a security issue; it's a critical financial decision. By treating evidence collection as a core part of your daily operations, you shift from being reactive to being permanently audit-ready.
Common Questions About PCI DSS Requirements
As you dig into the world of PCI DSS, a few questions almost always pop up. Let's tackle some of the most common ones that businesses grapple with on their journey to compliance.
If I Use a Third-Party Payment Processor, Am I Automatically Compliant?
This is a big one, and the short answer is no. Using a PCI-compliant third-party processor is a fantastic move that can massively shrink your compliance scope, but it doesn’t just wipe the slate clean. You're still on the hook for your own internal processes, like making sure your team is trained and that you aren't accidentally storing card data somewhere else.
The real win here is that modern payment solutions can stop cardholder data from ever touching your systems in the first place. This is what lets you qualify for a much simpler Self-Assessment Questionnaire (SAQ), taking a huge pile of complicated technical requirements right off your plate.
What’s the Real Difference Between PCI DSS v3.2.1 and v4.0?
Think of PCI DSS v4.0 as the modern evolution of the standard, built to handle today's threats and payment technologies. The biggest change is a shift towards more flexibility. Instead of just ticking boxes, v4.0 allows you to use customised controls to meet security goals. It also beefs up requirements for authentication and expands its reach to cover newer payment channels.
While v3.2.1 was officially retired in early 2024, the new requirements in v4.0 are considered best practice until they become mandatory in early 2025. If you haven't already, now is the time to start working towards v4.0, especially in areas like multi-factor authentication and tighter security awareness training.
Key Insight: The move to v4.0 is less about rigid rules and more about achieving clear security objectives. It gives you the freedom to find security solutions that actually fit your business, as long as you can prove they get the job done.
Are Our Call Recordings in Scope for PCI DSS?
Yes, without a doubt. If your contact centre records calls where customers read out their card details, those recordings are now containers for sensitive cardholder data. That means they are 100% in scope for PCI DSS. The recording system itself, where the files are stored, and who can access them all have to meet the standard's toughest security rules.
For most contact centres, this is a massive headache. The most effective way out of this compliance trap is to use technology like DTMF suppression (which masks the keypad tones) or channel separation. By ensuring the sensitive data is never captured in the first place, you pull your call recordings completely out of scope and make your compliance life dramatically simpler.
At Paytia, we specialise in taking the pain out of PCI DSS for contact centres. Our secure payment platform uses clever technology to make sure sensitive card data never even enters your environment. This can reduce your audit scope by as much as 95%, turning a complex compliance project into a manageable one. Learn how Paytia can secure your payments today.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
