
Understanding Your Level of PCI Compliance in the UK
Get Compliance Consultation
Ensure your payment processing meets UK regulations with Paytia's compliance experts.
Your PCI compliance level is simply a category your business falls into based on how many card transactions you process each year. The logic is straightforward: the more payments you handle, the more rigorous the security checks you need to pass.
Understanding Your PCI Compliance Level
Think of it like getting a vehicle MOT. A family car needs a standard annual check-up, but a heavy goods vehicle hauling dangerous materials requires a much more stringent and frequent inspection. It's the same principle with PCI DSS. A small local shop processing a few thousand transactions a year has a simpler path to proving they're secure compared to a national retailer handling millions. This tiered system makes sure the security effort matches the level of risk.
The Payment Card Industry Data Security Standard (PCI DSS) groups merchants into four main levels. These aren't just labels; they dictate exactly what you need to do to prove your systems are safe. Getting this wrong can lead to some seriously painful consequences.
Why Your Compliance Level Matters
Knowing your specific PCI compliance level is the absolute first step in protecting your business and your customers. Misjudging it isn't a minor slip-up; it can leave you wide open to huge financial penalties and shatter the trust you've built with your customers. For UK businesses, the stakes are incredibly high.
Recent card fraud statistics paint a stark picture, with over £0.5 billion lost in just one 12-month period. A shocking 80% of that figure came from card-not-present (CNP) fraud—the kind that happens over the phone, through chat, or other remote channels. You can learn more about how to navigate these challenges and get ready for the PCI DSS 4.0 deadline in March 2025.
A data breach can unleash crippling fines from the card brands, lead to your merchant account being terminated, and cause irreparable damage to your reputation. Your compliance level essentially defines your battlefield and the minimum defences you need to have in place.
Ultimately, your transaction volume decides your entire compliance journey. It's the difference between being able to check your own security with a self-assessment and having to bring in external auditors for a full-blown on-site inspection. Knowing where you stand isn't about ticking a box—it’s about building a solid security strategy that protects your bottom line.
Decoding the Four Merchant PCI Compliance Levels
Figuring out your level of PCI compliance isn't about memorising a bunch of technical rules. It’s about understanding where your business fits into the bigger picture of payment security. Let's ditch the dry definitions and look at what each level means in the real world, whether you're a high-street giant or a local charity.
The whole system boils down to one main factor: how many card transactions you process each year. The more you handle, the higher your level—and the stricter the rules get.
This diagram lays it all out. Level 1 is for the biggest players with the highest transaction volumes, and the requirements scale down from there.
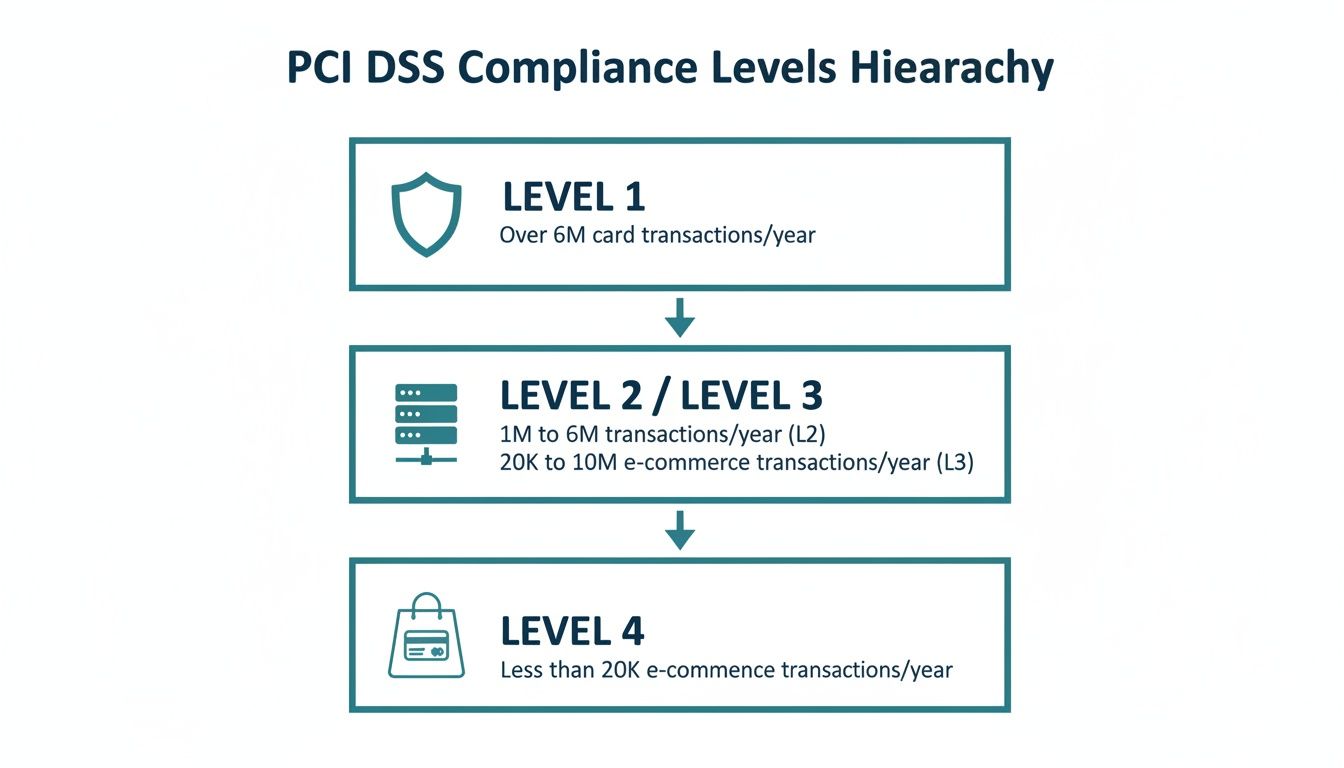
As you can see, the compliance burden is designed to match the risk. It makes sense—businesses holding the most cardholder data need the most intense scrutiny.
Level 1: The Highest Tier of Scrutiny
Think of a major UK supermarket or a national airline. These companies process a staggering number of card payments daily—in-store, online, and over the phone. That puts them squarely in Level 1.
A business lands in Level 1 if it processes over six million card transactions a year. Because they handle such a massive amount of sensitive data, they're considered the highest risk and face the toughest validation process.
The non-negotiable for Level 1 is an annual Report on Compliance (ROC). This is no simple checklist. It's a full-blown, on-site audit carried out by an independent Qualified Security Assessor (QSA). The QSA acts like a forensic inspector for your data security, meticulously checking every system, policy, and control that comes anywhere near cardholder data. For a deeper dive on what that involves, take a look at our guide on PCI compliance auditing.
On top of the ROC, Level 1 merchants must also:
- Run quarterly network vulnerability scans with an Approved Scanning Vendor (ASV).
- Complete an Attestation of Compliance (AOC) form to formally sign off on their compliance status.
Level 2: The Growing Business
Now, picture a successful e-commerce brand that’s been growing fast. They might not be a household name just yet, but they're processing a serious number of orders.
This is Level 2 territory, covering businesses that handle between one million and six million transactions annually. The validation isn't quite as intense as a full on-site audit, but the security standards are still incredibly high.
Instead of an external ROC, Level 2 merchants usually validate their compliance with a Self-Assessment Questionnaire (SAQ). This is a detailed report where the business evaluates its own security against the PCI DSS rules. They also have to complete the quarterly network scans and submit an AOC.
Level 3: The Established Local Enterprise
What about a popular local restaurant chain with a few locations, or a regional charity that holds an annual telethon? These organisations process a steady flow of payments but are well under the million-transaction mark.
Level 3 is for merchants processing between 20,000 and one million e-commerce transactions per year. Just like Level 2, their main validation tools are the annual SAQ and quarterly scans from an ASV.
The real devil is in the detail of the SAQs. A simple online shop that outsources all its payment processing might only need to fill out SAQ A, which is fairly straightforward. But a business taking card details over the phone—where that data enters their environment—is looking at the far more gruelling SAQ D, which can have over 300 questions.
Level 4: The Small Business Start-Up
Finally, imagine a small local bakery selling cakes online or a solo consultant taking payments for their services. These businesses are the backbone of the economy, but their card payment volume is much lower.
Level 4 is for anyone processing fewer than 20,000 e-commerce transactions or up to one million total transactions a year. This is the most common compliance level. The requirements are the most manageable, focusing on completing the right SAQ and running quarterly scans if they apply to your setup.
Pinpointing your exact level is the essential first step. Once you know where you stand, you can build a security strategy that’s both effective and manageable for your business.
The Hidden Dangers of PCI Scope Creep
Figuring out your level of PCI compliance is just the first step. The real challenge, especially for organisations taking payments remotely, is keeping your PCI DSS scope under control.
Think of it like painting a room. Your PCI scope is the area you need to protect. If you're careful, you just need to tape off the skirting boards and window frames. But if you get sloppy? Paint splashes everywhere—the ceiling, the floor, the furniture. Suddenly, a simple job turns into a massive clean-up operation.
This is exactly what PCI scope creep does. Without tight controls, sensitive cardholder data can splash across your entire network, dramatically expanding the area you must secure, audit, and prove is compliant.

For contact centres and other regulated businesses, this isn't just a theory; it’s a daily risk. Every system, application, and person that interacts with—or could even affect the security of—cardholder data is considered 'in scope'. When that scope expands, so do the costs, complexity, and headaches of maintaining your PCI compliance level.
How Everyday Actions Widen Your PCI Scope
Scope creep often happens silently, through seemingly harmless practices. An agent might jot down a card number on a notepad "just in case the system crashes." That single piece of paper, the desk it's on, and even the bin it’s thrown into are now in scope.
Call recording is another huge culprit. Many contact centres rely on a manual 'pause and resume' system to stop recording when a customer reads out their card details. But what if the agent forgets to pause or resumes too early? The full card number and CVC are now stored in your call recordings, instantly dragging your entire recording platform and its associated storage into the PCI audit zone.
This is where it gets dangerous: a single moment of human error can pull vast, interconnected systems into the scope of a PCI audit. Suddenly, your CRM, VoIP system, agent desktops, and network infrastructure must all meet the stringent standards of PCI DSS.
This transforms a manageable compliance task into an expensive and technical nightmare. Instead of securing a small, defined payment channel, you're now responsible for proving the security of your entire contact centre.
Common Causes of PCI Scope Creep in Contact Centres
Many standard contact centre practices inadvertently expand PCI scope. The table below highlights how seemingly normal operations introduce risk and how secure alternatives, like those offered by Paytia, can contain it.
| Common Practice | Resulting Security Risk | Impact on PCI Scope | Secure Alternative (e.g., Paytia) |
|---|---|---|---|
| Manual 'Pause & Resume' for call recordings. | Human error leads to card data being stored in audio files. | Brings the entire call recording system, storage, and network into scope. | DTMF masking automatically prevents card tones from ever being recorded. |
| Agents verbally take card numbers. | Staff see and hear sensitive card details, increasing insider threat risk. | Agent desktops, headsets, and surrounding physical environment enter scope. | Agent-assisted payments let customers enter details on their keypad; agents never see or hear them. |
| Taking card details in web chat or email. | Unencrypted transmission and storage of plain-text card data. | Chat platforms, email servers, and agent workstations all become in-scope. | Secure payment links sent via chat/email direct customers to a PCI-compliant portal. |
| Storing card numbers in the CRM for future use. | Card data is stored in a system not designed for it, creating a high-value target for attackers. | The entire CRM, its database, and connected applications are pulled into scope. | Tokenization replaces the card number with a secure, non-sensitive token for recurring billing. |
By adopting secure payment technologies, you can effectively draw a clear line around your payment process, ensuring card data never touches your wider environment.
The True Cost of Uncontrolled Scope
When your PCI scope gets out of control, the consequences are immediate and painful. The validation process becomes exponentially more difficult. A business that could have used a simple Self-Assessment Questionnaire (SAQ) may find itself forced into the territory of SAQ D, the most demanding of them all, which covers over 300 security controls.
The financial fallout includes:
- Higher Audit Costs: More systems to assess means more time and money spent on auditors or internal teams.
- Increased Remediation Efforts: You’ll likely need to invest in new security hardware, software, and policy changes across a much wider footprint.
- Operational Disruption: Audits and security upgrades can grind daily operations to a halt, pulling key people away from their core duties.
Ultimately, uncontrolled scope turns achieving and maintaining your PCI compliance level into a constant, uphill battle. It dramatically increases the likelihood of a data breach and the severe penalties that follow. The key isn't just to meet the standards but to actively contain the "paint" from the very start by preventing card data from entering your environment in the first place.
How PCI DSS v4.0 Impacts Your Compliance Efforts
The world of payment security never sits still, and neither does the PCI Data Security Standard. The latest version, PCI DSS v4.0, isn't just a minor tweak; it's a major evolution designed to tackle modern security threats head-on. If your business handles card payments, getting to grips with these changes is essential, as they directly affect the work needed to maintain your PCI compliance level.
Think of it like updating the building code for a house. The foundation is the same—protecting cardholder data—but the new rules demand stronger locks, better alarms, and reinforced windows to deal with today's more sophisticated intruders. PCI DSS v4.0 does the same for your data security, reacting to the rise of remote working, automated attacks, and clever phishing scams.
This new version raises the security bar for everyone, no matter how many transactions you process. While your transaction volume still dictates your specific PCI compliance level, v4.0 increases the baseline effort needed across the board.
Key Security Enhancements in Version 4.0
The updates in v4.0 aren't just for show. Each one is a direct response to a real-world risk that has become more prominent in recent years. Instead of just ticking off old controls, the standard now pushes for a more proactive and continuous approach to security.
Some of the most significant changes include:
- Mandatory Multi-Factor Authentication (MFA): Previously, MFA was often just for remote access. Now, it’s required for all access into the cardholder data environment. This provides a crucial defence against stolen login details.
- Enhanced Phishing Protection: The standard now has specific requirements to defend against phishing, finally acknowledging that human error is often the weakest link in the security chain.
- Stronger Password Requirements: Passwords for accounts used by applications and systems must now be changed at least every 12 months and can no longer be hard-coded into scripts or files.
These updates mean that maintaining even a Level 4 compliance status now demands more technical and procedural effort than ever before.
PCI DSS v4.0 marks a shift away from a "point-in-time" compliance checklist and towards a continuous security mindset. It encourages businesses to weave security into their daily operations, not just treat it as an annual audit.
The Urgency of the March 2025 Deadline
The transition to the new standard isn't happening overnight, but a critical deadline is looming. All new assessments must use v4.0 from January 1, 2025, and all its new requirements become mandatory by March 31, 2025. Key v4.0 changes demand documented data retention policies, stronger vulnerability management, and enhanced website script protections.
This deadline creates a real sense of urgency. Waiting until the last minute could lead to a frantic scramble for resources, failed assessments, and a loss of your compliant status. It’s precisely why proactively reducing your PCI scope has never been more critical. By shrinking the number of systems that handle card data, you also shrink the number of systems that need updating to meet these stricter v4.0 controls.
For businesses that take payments over the phone, these changes introduce unique challenges. You can learn more by reading our guide on PCI DSS v4.0.1 telephone payment compliance requirements.
Ultimately, the arrival of v4.0 reinforces a core truth of compliance: the smaller your PCI scope, the simpler, cheaper, and faster your journey will be.
Radically Reducing Your PCI Compliance Burden
After grappling with the dangers of PCI scope creep, the way forward isn't about building taller walls around your entire network. It's about fundamentally changing how your business interacts with sensitive card data—making sure the data never enters your building in the first place.
Modern secure payment technologies achieve this by creating a secure bubble around the transaction, completely isolating it from your business environment. This approach dramatically shrinks your PCI scope, which directly slashes the effort and cost tied to your level of pci compliance. Let’s explore how these technologies work with a couple of simple analogies.

How Technology Contains the 'Paint'
Two core technologies are central to containing PCI scope: DTMF suppression and tokenisation. They work in tandem to ensure card numbers, expiry dates, and CVCs are never seen, heard, or stored within your systems.
Imagine your customer is paying over the phone. As they tap their card details into their telephone keypad, DTMF (Dual-Tone Multi-Frequency) suppression acts like a soundproof box. It intercepts those tones before they ever reach your agent or your call recording system, replacing them with a flat, monotonous sound. Your agent can see the numbers appearing on their screen as asterisks, but they never hear the tones, and your call recordings capture nothing of value.
Next, tokenisation comes into play. Think of this as swapping your actual house key for a single-use ticket. Instead of your systems storing the 16-digit card number, the secure payment platform sends it straight to the payment gateway. In return, the gateway sends back a unique, non-sensitive 'token'—a random string of characters that represents that specific card for any future transactions.
By combining these methods, you create a powerful barrier. DTMF suppression prevents data from entering your environment via audio, while tokenisation ensures it’s never stored in your databases. The actual card data completely bypasses your infrastructure.
The Impact on Your Compliance Level
This is where the strategy really pays off. By implementing a solution like Paytia's Secureflow, which keeps card data entirely separate from your environment, you can slash your PCI scope—often by as much as 95%. This has a direct and profound effect on your validation process.
The key takeaway is that the platform handles all the heavy lifting. This allows your business to focus on a much smaller, more manageable set of compliance controls.
A contact centre that was previously staring down the barrel of a Self-Assessment Questionnaire (SAQ) D, with its 329 demanding questions, could suddenly find itself eligible for the far simpler SAQ A. This version applies to merchants who have fully outsourced their cardholder data functions and can be completed in a fraction of the time.
Tangible Business Outcomes
The benefits of shrinking your PCI scope go far beyond just ticking a compliance box. It translates into real, measurable advantages for your business, your staff, and your customers. The goal isn't just to be compliant; it's to be secure in a way that actually fuels growth and confidence.
Here’s what this means in practice:
- Lower Audit and Remediation Costs: With fewer systems in scope, the time and money you spend on auditors, penetration tests, and quarterly scans will plummet. You're no longer paying to secure systems that never even touch card data.
- Reduced Risk of a Data Breach: The simplest way to protect cardholder data is not to have it in the first place. By preventing it from ever entering your environment, you eliminate the primary target for cybercriminals.
- Simplified Operations: Your agents can get back to focusing on serving customers without the stress of handling toxic data. This removes the risk of human error and makes training much simpler.
- Increased Customer Trust: Offering a secure and seamless payment experience shows customers you take their security seriously. This builds the kind of confidence and loyalty that encourages repeat business.
Ultimately, by embracing secure payment technology, you can transform your relationship with PCI DSS. It shifts from being an overwhelming annual burden to a manageable, strategic part of your security posture, allowing you to maintain your required level of pci compliance with far less friction and cost.
Your Action Plan for PCI Compliance
Knowing your level of pci compliance is one thing, but turning that knowledge into a real-world security strategy is something else entirely. This is where the theory stops and the practical work begins.
Achieving and maintaining compliance isn’t a one-off project. Think of it as a continuous cycle of assessing where you are, fixing what’s broken, and proving you’ve done the work.
We’ve put together a practical roadmap to help you take control. Below is a step-by-step guide to structure your compliance journey, turning what can seem like an overwhelming task into a series of clear, manageable steps.
Your Step-by-Step Compliance Journey
The path to proving your compliance follows a logical sequence. Each step builds on the last, starting with a clear-eyed look at your current setup and ending with the formal paperwork.
Calculate Your Transaction Volume: First things first, you need to know exactly which PCI compliance level you fall into. Get the numbers. Tally up every single card transaction from all your channels over the past 12 months. This figure is the key that unlocks your specific validation requirements.
Map Your Cardholder Data Environment (CDE): Get visual. Create a detailed diagram that shows every single point where cardholder data enters, moves through, or is stored in your business. This map needs to include everything—from agent desktops and call recording systems to your CRM and the network hardware that connects it all.
Identify Scope Reduction Opportunities: With your data map in hand, it’s time to get ruthless. Pinpoint every system you can possibly remove from the CDE. For each one, ask the critical question: "Does this system really need to touch card data?" Implementing technologies like DTMF suppression and tokenisation can shrink this map dramatically, saving you a world of effort.
Conduct a Gap Analysis: Now, compare your current security controls against the specific PCI DSS requirements for your level. This process will shine a light on any gaps that need filling before you can even think about validating your compliance. A comprehensive PCI DSS compliance checklist is an invaluable tool at this stage.
Remediate and Implement Controls: Time to fix the problems you found. This stage might involve patching software, changing up internal processes, or deploying new security solutions to lock down data and limit who can access it.
Choose Your Validation Method: Based on your compliance level, you’ll need to select the right validation tool. For Levels 2, 3, and 4, this will be the correct Self-Assessment Questionnaire (SAQ). If you’re a Level 1 merchant, you’ll need to bring in the big guns and engage a Qualified Security Assessor (QSA) for a full on-site audit.
Complete Your Validation and Submit: The final hurdle. Fill out your SAQ or work with your QSA to complete your Report on Compliance (ROC). Once it’s all signed off, you’ll submit the required documents, including your Attestation of Compliance (AOC), to your acquiring bank.
Compliance is a continuous process, not an annual event. It requires ongoing vigilance, regular monitoring, and a commitment to maintaining your security posture throughout the year.
Making Compliance a Sustainable Process
The old-school approach often treats PCI compliance like a yearly MOT—a mad scramble to fix everything just before the deadline hits. That’s not just stressful; it's a terrible security strategy.
Modern solutions, on the other hand, give you the audit trails, logs, and reporting tools you need to make compliance an ongoing, streamlined activity.
By embedding secure payment technology directly into your day-to-day operations, you shift from reactive fire-fighting to proactive management. This ensures that when your next assessment rolls around, you already have all the evidence and controls neatly in place. It transforms compliance from an annual headache into a manageable, continuous part of your business rhythm.
Common Questions About PCI Compliance Levels
Let's tackle some of the most frequent questions businesses have when figuring out their PCI compliance level and what it all means for day-to-day operations.
Does Using a Third-Party Payment Provider Automatically Make Us Compliant?
Not quite, but it makes the journey a whole lot easier. Handing off the heavy lifting to a secure third-party provider dramatically shrinks your PCI scope. You’re still on the hook for securing the remaining parts of your environment and completing the right validation, but it's usually a much simpler Self-Assessment Questionnaire (SAQ).
A secure provider essentially carves out the most complex and high-risk elements from your systems. This makes achieving compliance significantly less difficult and costly.
What’s the Difference Between a Report on Compliance and a Self-Assessment Questionnaire?
Think of it like the difference between a final exam invigilated by an external examiner and a take-home test. A Report on Compliance (ROC) is a formal, on-site audit conducted by an independent Qualified Security Assessor (QSA). This is a rigorous, mandatory examination reserved for Level 1 merchants—those processing the highest volume of transactions.
On the other hand, a Self-Assessment Questionnaire (SAQ) is a tool that allows Level 2, 3, and 4 merchants to check their own homework. There are several flavours of SAQ, ranging from a handful of questions for simple setups to over 300 for more complex environments.
How Does Having Remote Contact Centre Agents Affect Our PCI Compliance?
Remote working throws a huge spanner in the works for compliance, massively increasing your risk and scope. Suddenly, unsecured home networks and personal devices can drag an agent's entire home environment into PCI scope, creating a security and compliance nightmare.
This is exactly why solutions that stop card data from ever reaching the agent's location are so crucial. They contain your PCI scope within the secure platform itself, keeping it completely separate from the uncontrolled and risky home environment. This containment is absolutely essential for maintaining a manageable and defensible PCI compliance posture.
By isolating sensitive payment data from your business environment, Paytia can reduce your PCI DSS scope by up to 95%, simplifying your compliance efforts and lowering costs. Learn how our secure payment solutions can protect your business and customers at https://www.paytia.com.
Ready to Simplify Compliance?
Get expert guidance on UK payment regulations and PCI DSS compliance. Contact us today.
