
What Is Cardholder Data Environment a Guide to PCI DSS Scope
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
When you hear the term Cardholder Data Environment, or CDE, what should come to mind is a secure bubble around any part of your business that touches payment card information. It's the combination of people, processes, and technology responsible for storing, processing, or transmitting sensitive card details.
Think of it like a quarantine zone. Everything inside that zone needs to be locked down tight.
The Foundation of PCI DSS Compliance
Getting your head around your CDE isn't just a technical exercise; it's the absolute first step towards PCI DSS compliance. This "bubble" defines the exact boundaries of your security responsibilities. Any system, person, or process inside the CDE must meet the strict controls of the Payment Card Industry Data Security Standard (PCI DSS). Anything safely outside of it has far fewer hoops to jump through.
Defining this boundary correctly is a game of strategy. If you draw the line too wide, you end up with a massive CDE that's incredibly expensive and complex to secure. More systems mean more risk, more work, and more painful audits. On the flip side, a tightly defined and minimised CDE makes security manageable, affordable, and far more effective.
Why Your CDE Matters More Than Ever
The pressure to secure this environment is only growing. In the UK, for example, the shift to digital payments has been enormous. Online transactions made up 50.5% of all card spending in a recent September, a huge jump from just 43.7% in September 2019. You can see the full consumer spending data over on the ONS website.
This explosion in e-commerce and remote payments means card data is flowing through more systems than ever before, which can easily cause the CDE in many businesses to swell out of control.
To get more specific, let’s look at the core components that make up a CDE. The table below breaks down the key elements you need to identify.
Key Components of a Cardholder Data Environment
| Component Type | Description | Examples |
|---|---|---|
| People | Any employee, contractor, or team member with access to cardholder data or the systems within the CDE. | Call centre agents, finance teams handling refunds, IT administrators, developers working on payment pages. |
| Processes | The specific workflows and business operations that involve handling or accessing card information. | Taking payments over the phone, processing mail-order forms, managing recurring billing, handling chargebacks. |
| Technology | All hardware, software, and network equipment that stores, processes, or transmits card data. | Point-of-sale (POS) terminals, servers, network routers, firewalls, payment applications, virtual terminals. |
These three pillars—people, processes, and technology—are interconnected. A single weak link in any one of them can compromise the entire environment.
The smaller your CDE, the smaller your compliance footprint. Your primary goal should always be to reduce its scope, which directly lowers your risk, costs, and the effort required to prove compliance.
Ultimately, grasping what your CDE is—and what it isn't—sets the stage for every security decision you'll make. It’s the starting point for building a robust and defensible PCI DSS compliance programme. For a deeper dive into the standard itself, check out our complete guide on what PCI DSS is.
Defining Your CDE Scope and Boundaries
Once you’ve got your head around what a Cardholder Data Environment (CDE) actually is, the next crucial job is to define its scope. This process, known simply as scoping, is all about drawing a clear, firm boundary around every person, process, and piece of technology that comes anywhere near card data. Think of it as mapping out your own secure quarantine zone.
This isn’t just a box-ticking exercise; it's a strategic decision with massive implications for your business. Every single component inside this boundary is subject to the full force of all relevant PCI DSS controls. On the flip side, any system sitting safely outside this line has far fewer compliance hoops to jump through, which translates directly to lower costs and a lot less hassle.
The image below breaks down the three core pillars that make up any CDE.
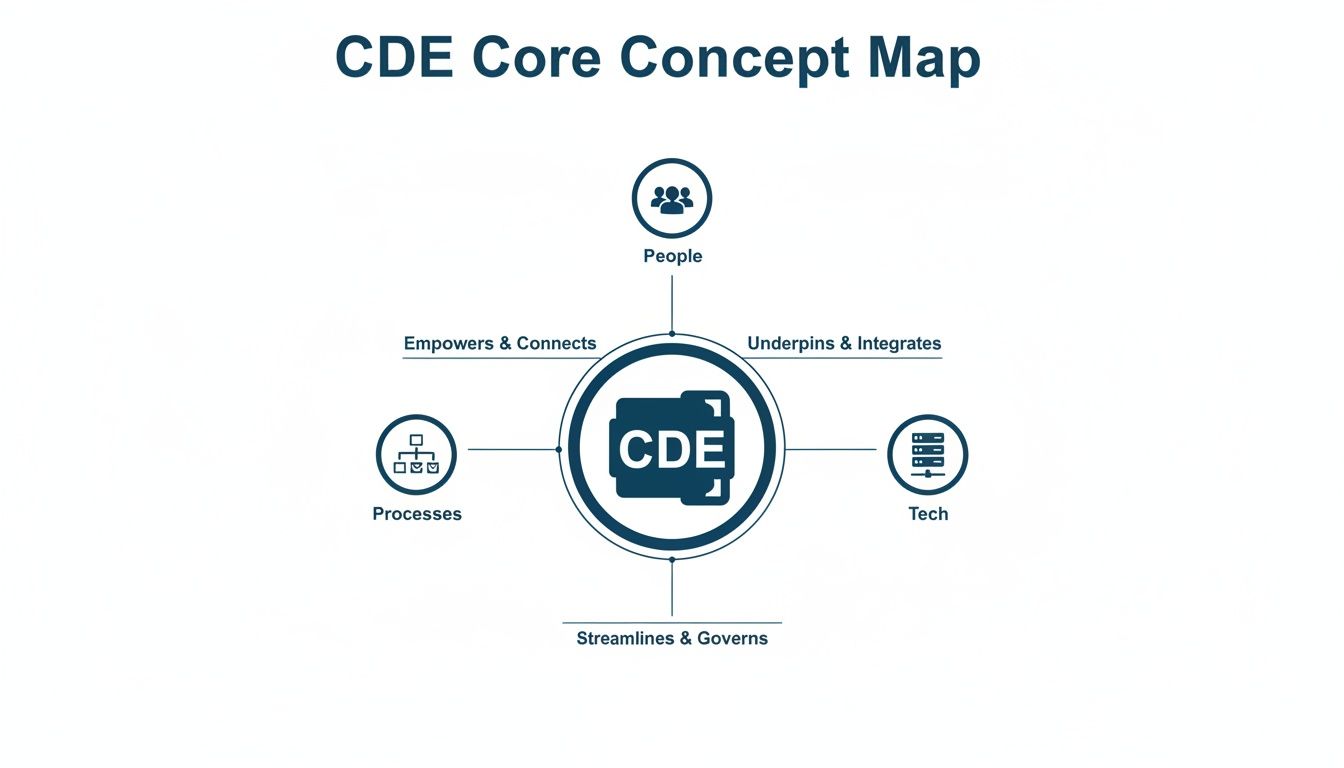
As you can see, the CDE is a combination of your technology, the processes you follow, and the people who run them. A weak link in any one of these areas can put the entire environment at risk.
Identifying In-Scope Systems
Figuring out your CDE's boundaries means you have to look beyond the obvious. Sure, your point-of-sale (POS) terminals and payment processing servers are clearly in-scope, but the real challenge is spotting the systems that are indirectly involved. Scoping rules tend to group systems in a few key ways:
- Systems that store, process, or transmit cardholder data: These are the heart of your CDE, things like payment applications and databases. No surprises there.
- "Connected-to" systems: These are any systems sitting on the same network segment as your CDE components. Without proper network segmentation, your entire office network could get pulled into scope.
- "Security-impacting" systems: These are systems that manage the security of your CDE, even if they never touch card data themselves. This includes things like authentication servers, logging systems, and vulnerability scanners.
For instance, an administrator’s laptop used to log into a payment server becomes part of the CDE, even if no card data is ever stored on it. Why? Because if that laptop gets compromised, it could be the key an attacker uses to unlock the entire environment.
Drawing these boundaries correctly is what transforms PCI DSS from a daunting list of over 300 sub-requirements into a manageable, targeted security framework. Your goal is to make this quarantine zone as small and as isolated as possible.
The Power of Proper Scoping
Getting your scoping right is the bedrock of a successful PCI DSS compliance programme. A well-defined and minimised CDE is simply easier to protect, cheaper to maintain, and far simpler to audit. By clearly identifying every system, application, and network device that could affect the security of cardholder data, you create a defensible perimeter.
This clarity also prevents scope creep, which is what happens when new, unsecured systems are accidentally connected to the CDE, creating dangerous vulnerabilities. It also makes sure your security investments are focused where they matter most—protecting the data that is most valuable to attackers and most critical to your customers’ trust.
Ultimately, scoping is about taking control of your security posture.
How a CDE Shows Up in Your Business
The idea of a cardholder data environment (CDE) can seem a bit abstract, but it gets very real, very fast when you see it in action. In many businesses, especially those with contact centres, the CDE isn't just a locked server room—it's woven directly into your daily customer interactions.

Picture a customer phoning your support team to pay a bill. The moment they read their card number aloud, your CDE expands dramatically. Suddenly, it’s not just about a payment gateway anymore. Now it includes the agent's headset, their computer, the entire telephony system, and even your call recording software.
If that card data gets captured in a recording or typed into an unsecure application, your CDE has just ballooned, pulling your entire communication infrastructure into the scope of PCI DSS. This is an incredibly common—and costly—oversight for many organisations.
Common Places Cardholder Data Hides
A CDE can pop up in all sorts of channels, often in places you’d least expect. Pinpointing these areas is the first step toward securing them and, more importantly, shrinking your compliance footprint.
Here are a few tangible examples:
- Phone Calls and IVR Systems: When customers key in or speak their card details, that data travels through your phone network. If it isn't properly isolated, every connected system—from the PBX to agent workstations—can become part of the CDE.
- Web Chat and Messaging: Transcripts from web chat sessions that contain a Primary Account Number (PAN) create a stored data risk. The chat platform, its servers, and any CRM system that logs these conversations are immediately pulled into scope.
- E-commerce Platforms: This is the most obvious one. Your website’s payment page, the web server it runs on, the application code, and the database are all core components of your CDE.
- Back-Office Systems: Maybe your finance team manually processes mail-order forms or handles refunds. The computers they use, the spreadsheets they might create, and even the shared network drives where files are saved all become part of the CDE.
Each of these examples shows just how easily your CDE can grow. The key takeaway is that cardholder data acts like a dye pack—once it touches a system, that system is stained and brought into PCI DSS scope.
This risk is amplified by the sheer volume of transactions. In the UK, outstanding credit card balances recently hit £72.1 billion. With billions in transactions flowing through business systems, protecting every touchpoint where cardholder data appears is simply non-negotiable. You can discover more insights on UK credit trends from the Bank of England's latest report.
Recognising these hidden CDEs is vital. By pinpointing exactly where card data flows, you can start to implement controls or adopt technologies—like those offered by Paytia—to remove these systems from scope entirely, shrinking your compliance burden for good.
Understanding the Risks and Required Controls
Leaving your cardholder data environment unsecured is like leaving the vault door wide open. It’s not just a box-ticking exercise for compliance; it’s a direct invitation for data thieves, posing a real threat to your business’s bottom line and reputation.
The consequences of a breach are steep, ranging from crippling fines issued by card brands to the irreversible loss of customer trust. A poorly defined or unprotected CDE makes you an easy target for cybercriminals. The whole point of PCI DSS is to give you a defensive framework, mapping specific controls to the threats you'll actually face. These aren’t just arbitrary rules; they are practical, battle-tested measures designed to protect sensitive payment information.
Matching Defences to Threats
Think of PCI DSS as a security strategy, not just a checklist. Every single requirement is a direct response to a known risk. For instance, weak network security can give an attacker a foothold, which is why controls around firewalls and secure configurations are so critical. It’s all about connecting the dots between the threat and the solution.
To give you a better idea of how this works, here’s a quick breakdown of some common risks and the PCI DSS controls designed to shut them down.
Common Risks vs PCI DSS Controls
This table maps common security threats within a CDE to the specific PCI DSS control categories designed to mitigate them. It’s a straightforward way to see the cause-and-effect relationship between a vulnerability and its corresponding safeguard.
| Common Risk | Description of Threat | Mitigating PCI DSS Control Category |
|---|---|---|
| Unauthorised Access | Attackers breaching your network to get their hands on stored or transmitted cardholder data. | Strong Access Control Measures: Ensuring only authorised personnel can interact with the CDE. This includes unique user IDs and multi-factor authentication. |
| Data Interception | Criminals capturing card data as it travels across your internal network or the open internet. | Network Security & Encryption: Encrypting all transmitted cardholder data and maintaining a secure, segmented network to protect data in transit. |
| Malware Infections | Malicious software like keyloggers or memory scrapers designed to skim card details from your systems. | Vulnerability Management: Maintaining a robust programme that includes regularly updated anti-virus software and prompt patching of system vulnerabilities. |
| Insider Threats | An employee, either maliciously or accidentally, exposing sensitive cardholder data. | Access Control & Monitoring: Restricting access on a need-to-know basis and logging all access to cardholder data to create a clear audit trail. |
| Physical Tampering | Gaining physical access to servers, terminals, or other hardware to steal data directly. | Physical Security Controls: Restricting physical access to sensitive areas and devices that store, process, or transmit cardholder data. |
Understanding this direct link makes it much easier to justify and implement the necessary security measures. Each control has a clear purpose tied to protecting your customers and your business.
When you’re defining and implementing these controls, it’s crucial to stick to industry best practices. For a deep dive into securely sanitising data when you no longer need it, the NIST SP 800-88 guidelines for data sanitization are considered the gold standard.
New technologies are also playing a huge role in strengthening these defences. Recent personal finance statistics show that 78% of transactions in the UK are now authenticated using biometrics like fingerprints or facial recognition. This, combined with AI-driven fraud detection, has helped slash card fraud losses by 18% year-on-year, proving how modern controls bolster the CDE.
Viewing these controls as a protective shield for your customers and your business completely changes your perspective. PCI DSS stops being a burden and becomes a strategic asset for building a secure, trustworthy operation.
Getting your head around the logic behind these rules is the first step. For a complete breakdown, explore our detailed guide on the core PCI DSS requirements.
Actionable Strategies to Reduce Your CDE Scope
Let's be honest, managing a sprawling Cardholder Data Environment (CDE) is a massive headache. It's expensive, complex, and keeps you up at night worrying about risk. The bigger your CDE, the more systems you have to lock down, monitor, and audit just to meet PCI DSS requirements.
The smartest move isn't just protecting the CDE you have—it's actively shrinking it.
By bringing in the right technology and processes, you can slash your CDE scope, often by over 90%. This doesn't just make compliance easier; it drives down costs and seriously beefs up your security. The real goal is to stop sensitive cardholder data from ever touching your systems at all.

Isolate Systems with Network Segmentation
One of the most fundamental ways to limit your CDE scope is network segmentation. Think of it as building digital walls inside your IT infrastructure. You create a separate, isolated network just for handling card data, keeping it completely separate from the rest of your business traffic like email, HR systems, or general web browsing. This is how you stop "scope creep."
Without proper segmentation, a single compromised laptop on your main office network could become a gateway for an attacker to pivot and access your payment systems. Good segmentation ensures that only systems with a legitimate, documented need can talk to the CDE, which drastically cuts down the number of components you have to worry about.
Remove Data with Advanced Technologies
While segmentation puts a fence around your CDE, modern tech can help you bulldoze parts of it completely. These solutions work by intercepting card data before it gets anywhere near your environment, effectively outsourcing the risk and compliance burden to a certified third party.
Here are the most effective methods:
- Tokenisation: This process swaps out the actual card number (the Primary Account Number or PAN) for a unique, non-sensitive stand-in called a token. You can safely store this token in your systems for things like recurring billing or looking up customer accounts, while the real card data stays locked away in your payment processor's secure vault.
- End-to-End Encryption (E2EE): E2EE scrambles card data the instant it’s captured—say, at a payment terminal—and it stays encrypted until it reaches the payment processor's secure environment. This means the data is never in a readable format as it travels through your network.
- DTMF Masking: A game-changer for phone payments. Dual-Tone Multi-Frequency (DTMF) suppression lets customers punch in their card details using their phone keypad. The tones are masked and captured directly by a secure third-party platform. Crucially, this means the sensitive data never reaches the agent's headset, their computer, or your call recording system.
By adopting these technologies, you can de-scope entire channels. A call centre agent's desktop, the phone system, and call recordings can be completely removed from your CDE, massively simplifying your audit process.
Leverage Secure Third-Party Solutions
For most businesses, building these advanced de-scoping tools from scratch is completely impractical. This is where partnering with a specialist, PCI DSS Level 1 certified provider like Paytia becomes a powerful strategic move.
Solutions like Paytia's Secureflow platform are designed for one primary purpose: to take your environment out of scope. By handling the capture of card data across voice, chat, and other digital channels, Paytia ensures the sensitive information is processed entirely within its own secure, compliant environment. Your systems never have to store, process, or transmit the raw card details.
This approach gives you a clear and simple path to compliance. Instead of juggling hundreds of individual PCI DSS controls across your own infrastructure, your main responsibility is simply to ensure your chosen provider maintains their certification. It’s a proven way to shrink your CDE, cut your risk, and free up your team to focus on what they do best—running your business.
How to Prove Your CDE Is Compliant
Defining and securing your cardholder data environment is a huge piece of the puzzle, but the job isn't finished until you can prove it to auditors and the payment brands. This is the validation stage—where you show that all your security controls aren't just ideas on paper but are actually working, day in and day out.
For the big players (what PCI DSS calls Level 1 merchants), this usually means a formal, on-site audit by a Qualified Security Assessor (QSA), which results in a Report on Compliance (ROC). Smaller businesses often get to complete a Self-Assessment Questionnaire (SAQ), which is essentially a guided checklist to verify they're meeting the standards. The right SAQ for you depends entirely on how you take payments.
Gathering Your Evidence
Whether you’re facing a full audit or an SAQ, the core task is the same: you have to collect and maintain clear evidence that your controls are doing their job. In fact, when you're showing your CDE is secure, you're really tapping into the broader principles of proving compliance program effectiveness.
What does that evidence look like in the real world? It’s usually a mix of things like:
- Clear Documentation: Detailed network maps that explicitly show your CDE boundaries and how card data moves through your systems.
- Vulnerability Scan Reports: Proof of regular passing scans from an Approved Scanning Vendor (ASV).
- Configuration Records: Evidence that your systems are configured securely and that all necessary security patches have been applied.
- Access Logs: Audit trails that tell the story of who accessed sensitive data, what they did, and when they did it.
Proving compliance isn't a one-and-done task; it’s a constant cycle. You have to keep monitoring, testing, and documenting to make sure your CDE stays locked down against new threats as they emerge.
Streamlining Audits with a Certified Partner
This is where working with a PCI DSS Level 1 certified provider like Paytia can completely change the game. By using a solution that prevents sensitive card data from ever touching your own systems, you’re effectively outsourcing the heaviest compliance lifting.
Your partner provides the audit-ready evidence for the payment capture process, which dramatically simplifies your own reporting duties. A partnership like this can transform what would have been a painful, resource-draining audit into a far more straightforward validation exercise. It makes the entire compliance journey faster and a whole lot less complicated. Our guide on the role of a QSA for PCI digs into this relationship in more detail.
Common Questions About the CDE
Once you start digging into the details of your Cardholder Data Environment, a few practical questions almost always come up. Let's tackle some of the most common points of confusion to help you manage your PCI DSS scope with more confidence.
Is Encrypted Card Data Still in Scope?
Yes, but it's a very different kind of "in scope." Think of it this way: even if you lock cash in a safe, the safe itself is still a security concern. The same logic applies here. Systems that store or transmit encrypted Primary Account Numbers (PANs) are still part of your CDE.
The good news is that PCI DSS recognises that encrypted data is far less risky. This means that while those systems aren’t completely off the hook, the number of security controls you need to apply to them is drastically reduced. The absolute key is to make sure your encryption keys are managed securely and stored completely separate from the encrypted data they protect.
Who Is Responsible if We Use a Third-Party Processor?
Ultimately, you are. Partnering with a third-party payment processor or gateway is a smart way to offload a huge chunk of the risk, but it doesn't wash your hands of responsibility. Under PCI DSS, compliance is a shared game between you and your service providers.
Your job is to perform proper due diligence. You must verify that your chosen provider is PCI DSS compliant and get a formal Attestation of Compliance (AOC) from them every year. This document is your proof that they are holding up their end of the security bargain.
What Is the Difference Between Storing and Transmitting Data?
"Transmitting" refers to card data in motion—when it’s travelling across your network or heading out to a payment processor. This data must always be encrypted during its journey, typically using strong protocols like TLS for online payments.
"Storing" is about data at rest—when it’s sitting in a database, a log file, or even a call recording. PCI DSS has very strict rules here, flat-out forbidding you to store sensitive authentication data (like the three-digit CVV) after a transaction is authorised. Any cardholder data you absolutely must store has to be rendered unreadable using methods like encryption, truncation, or tokenisation. Both scenarios—in motion or at rest—place the systems involved firmly inside your CDE.
Take the complexity out of securing your CDE. Paytia provides PCI DSS Level 1 certified solutions that prevent sensitive card data from ever entering your environment, dramatically reducing your scope and compliance burden. Learn how Paytia can secure your phone and digital payments.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
