What Is PCI Compliant? A Practical Guide for Merchants
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
If you’ve ever wondered what it means to be PCI compliant, you’re not alone. In simple terms, it means your business follows a specific set of security rules to keep your customers' payment card details safe from fraudsters and thieves. Think of it as the minimum security standard for handling sensitive financial data—it’s absolutely vital for earning and keeping customer trust.
What PCI Compliance Really Means For Your Business

Here's the bottom line: if your business in the UK accepts, processes, stores, or even just transmits credit or debit card information, then PCI compliance isn't optional. It’s a firm requirement.
This isn't a government law, but a contractual rule set by the major card brands—think Visa, Mastercard, and American Express. The rulebook they all enforce is called the Payment Card Industry Data Security Standard (PCI DSS).
Let's put it another way. If you ran a restaurant, you’d have to follow strict food hygiene regulations to keep your customers safe. PCI DSS is the data equivalent for your business; it protects your customers from financial harm and shows you're a responsible, trustworthy company.
The Heart Of PCI DSS: Protecting Cardholder Data
The whole point of PCI DSS is to protect Cardholder Data (CHD). This is the treasure trove that cybercriminals are after, and it’s more than just the card number.
Specifically, it includes:
- Primary Account Number (PAN): That long number on the front of the card.
- Cardholder Name: The cardholder's full name.
- Expiry Date and Service Code: Key details needed to authorise a purchase.
- Sensitive Authentication Data: This is the really critical stuff like the CVV code, PINs, and full magnetic stripe data. Under PCI DSS rules, you must never store this information after a transaction is authorised.
PCI DSS is a global security standard mandated by the card brands, not a government law. Failing to comply can result in serious consequences, from steep fines to losing your ability to accept card payments altogether.
To give you a clearer picture, here's a quick breakdown of the core components.
PCI Compliance At A Glance
| Component | What It Is | Why It Matters For Trust |
|---|---|---|
| PCI DSS | The Payment Card Industry Data Security Standard—a set of 12 core requirements. | It's the universal rulebook for protecting customer payment data worldwide. |
| Cardholder Data (CHD) | The full PAN, cardholder name, and expiry date. | This is the primary data that needs to be secured wherever it is stored or processed. |
| Sensitive Auth Data | CVV, PINs, and full magnetic stripe/chip data. | This data is so sensitive it should never be stored, proving you're not hoarding risky info. |
| Scope | The people, processes, and technologies in your business that touch cardholder data. | Reducing your scope is the key to simplifying compliance and lowering your risk profile. |
Following these standards shows customers you're actively working to protect them, which is a powerful way to build brand loyalty.
Why Compliance Is A Pillar Of Trust
Getting PCI compliant is far more than a box-ticking exercise. It's a powerful message to your customers that you take their financial security seriously. In a world where data breaches make headlines almost daily, showing you have robust security practices in place builds real confidence and protects your hard-earned reputation.
A crucial part of compliance that often gets overlooked is what you do with old IT equipment. You can't just throw it away. Secure disposal ensures that any stored cardholder data can't be retrieved from old hard drives or servers. This is why working with secure data destruction with compliant partners is a non-negotiable part of a complete security strategy.
Ultimately, PCI compliance isn’t a one-off project; it’s an ongoing commitment to protecting your customers, and in doing so, protecting your business.
The 12 Core PCI DSS Requirements Explained

At first glance, the 12 PCI DSS requirements can look like an intimidating technical checklist. But they’re not just arbitrary rules. They’re a logical framework for building robust security, designed to protect sensitive payment data from every conceivable angle.
Instead of getting lost in the details of each one, it’s much easier to grasp them when grouped into six core goals. Think of this as the blueprint for constructing a secure payment environment from the ground up, with each requirement acting as a critical building block.
Goal 1: Build and Maintain a Secure Network
This is all about putting a strong perimeter around your systems. It’s the digital equivalent of building fortress walls and hiring a bouncer to guard the front door.
- Requirement 1: Install and Maintain Network Security Controls. You need firewalls to act as a digital bouncer. They stand at the edge of your network, inspecting all incoming and outgoing traffic and deciding who gets in and who stays out.
- Requirement 2: Apply Secure Configurations. Never use vendor-supplied defaults for system passwords and other security parameters. Leaving a password as “admin” or “password123” is like leaving your front door key under the mat—it’s the first place criminals will look.
Goal 2: Protect Account Data
Once payment data is inside your network, it’s your responsibility to guard it. This goal focuses on making that data completely useless to anyone who might steal it.
- Requirement 3: Protect Stored Account Data. If you absolutely have to store cardholder data, you must make it unreadable. This is done using strong techniques like encryption, hashing, and masking, which scramble the data into a useless jumble for unauthorised eyes.
- Requirement 4: Protect Data with Strong Cryptography During Transmission. When card details travel across open, public networks (like the internet), they must be encrypted. This is what the little padlock icon and “HTTPS” in your browser’s address bar signify—a secure, private tunnel protecting the data on its journey.
The latest version, PCI DSS 4.0, places a much greater emphasis on customised security approaches and stronger authentication methods. It’s a direct response to the evolving threat landscape, acknowledging that rigid, one-size-fits-all rules are no longer enough to combat sophisticated modern cyberattacks.
Goal 3: Maintain a Vulnerability Management Programme
Security isn’t a one-and-done task. It’s a continuous process of proactively finding and fixing weaknesses before attackers have a chance to exploit them.
- Requirement 5: Protect All Systems from Malicious Software. This is a fundamental one: use and regularly update anti-virus and anti-malware software on all systems that could be affected.
- Requirement 6: Develop and Maintain Secure Systems and Applications. When a software provider releases a security patch, install it promptly. Just like you update your smartphone’s OS to fix bugs and security holes, you must do the same for all your business systems.
Goal 4: Implement Strong Access Control Measures
This goal is built on the principle of "need-to-know." It's about ensuring that only the right people can access sensitive information, and only when it's absolutely necessary for their job.
- Requirement 7: Restrict Access to Cardholder Data. Access to sensitive payment information should be limited strictly to employees whose roles require it. Not everyone in the company needs the keys to the digital vault.
- Requirement 8: Identify Users and Authenticate Access. Every single person who can access your systems needs their own unique ID and password. This gets rid of shared, generic logins and means you can trace every action back to a specific individual.
- Requirement 9: Restrict Physical Access. This goes beyond the digital world. It means locking server room doors, securing paper documents with card details, and generally preventing unauthorised individuals from physically getting their hands on sensitive data.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you can't see. This goal is about keeping a constant watch over your systems for suspicious activity and actively testing your own defences to find weak spots.
- Requirement 10: Log and Monitor All Access. You must keep detailed logs of all activity across your network and review them regularly. Think of these logs as your security cameras—they help you spot trouble as it happens and are invaluable for investigating any incidents.
- Requirement 11: Test Security of Systems and Networks Regularly. This means running regular vulnerability scans and penetration tests. In short, you’re hiring ethical hackers to try and break into your systems to find any holes before the real criminals do.
Goal 6: Maintain an Information Security Policy
Finally, all these technical measures need to be supported by a formal, documented policy that everyone in your organisation understands and follows. Technology is only half the battle; people are the other half.
- Requirement 12: Support Information Security with Policies and Programmes. A formal security policy sets the ground rules for everyone. It should clearly define procedures for handling cardholder data, outline a plan for responding to security incidents, and mandate regular security awareness training for all staff.
Finding Your PCI Merchant Level and Validation Method
Getting to grips with PCI compliance isn't just about learning the rules; it's about figuring out which ones actually apply to you. Let's face it, the requirements aren't a one-size-fits-all deal. A huge multinational retailer processing millions of transactions faces a whole different level of scrutiny than a local charity taking a few donations over the phone.
To make sense of this, the Payment Card Industry (PCI) groups businesses into four distinct merchant levels. What determines your level? It almost always comes down to one thing: how many card payments you process each year. Pinpointing your level is the absolute first step to understanding what you need to do to stay compliant.
Unpacking the Four PCI Merchant Levels
Think of these levels like weight classes in boxing. The heavyweight contender (Level 1) has a far more intense and regulated training regime than a lightweight (Level 4). The more transactions you handle, the more rigorous your compliance validation process becomes.
While the exact numbers can differ slightly between card brands like Visa and Mastercard, the general breakdown looks like this:
- Level 1: This is for the big players—merchants processing over 6 million card transactions a year. It’s also the category for any business, regardless of size, that has had a major data breach.
- Level 2: For businesses handling between 1 million and 6 million transactions annually.
- Level 3: For merchants processing between 20,000 and 1 million e-commerce transactions per year.
- Level 4: This covers merchants with fewer than 20,000 e-commerce transactions, or up to 1 million transactions through other channels like phone payments.
The vast majority of small and medium-sized businesses in the UK, including most contact centres, will land in Level 3 or 4. Knowing your level is critical because it tells you exactly how you have to prove you’re compliant. To dig deeper into how these categories affect your business, check out our guide on the different PCI levels of compliance.
Choosing Your Validation Method: ROC vs SAQ
Once you’ve identified your merchant level, you can figure out which validation method you need to use. There are two main paths, and they demand very different levels of effort and external oversight.
A Report on Compliance (ROC) is the most thorough and demanding validation method, reserved exclusively for Level 1 merchants. Picture it as a full-scale, formal audit conducted on-site by an independent Qualified Security Assessor (QSA). The QSA will comb through every aspect of your cardholder data environment, from network diagrams to physical security, and produce an exhaustive report to verify you meet all 12 PCI DSS requirements.
For everyone else—Levels 2, 3, and 4—the process is much different. These merchants typically complete a Self-Assessment Questionnaire (SAQ). Think of an SAQ as being more like filing a detailed tax return for your business. You are responsible for going through the checklist, assessing your own security, and officially attesting that you are compliant. There isn't just one SAQ, though; there are several versions tailored to different business models (e.g., e-commerce only vs. phone payments), so choosing the right one is absolutely essential.
The validation method is a direct reflection of risk. Higher transaction volumes mean a data breach would have a much bigger impact. That’s why Level 1 merchants face a rigorous independent audit, while smaller businesses are trusted to self-assess.
This tiered system makes perfect sense when you look at the scale of card fraud in the UK, which tops £0.5 billion every year. A staggering 70-80% of that comes from card-not-present transactions—the kind that are standard in contact centres and remote sales. This risk-based approach ensures that the businesses posing the greatest threat are held to the highest standard of security checks. You can explore more about UK fraud statistics and compliance levels on Securious.co.uk.
The True Cost Of Non-Compliance And Common Pitfalls
It's one thing to know the rules of PCI compliance, but it’s another thing entirely to grasp what happens when things go wrong. Failing to meet these standards isn't just a box-ticking exercise; it’s a serious business risk with consequences that ripple through your entire organisation.
The penalties for non-compliance are far more severe than a simple slap on the wrist. Card brands can levy hefty monthly fines that stack up frighteningly fast. But the financial pain doesn’t stop there. Your acquiring bank might hike up your transaction fees or, in the worst-case scenario, simply terminate your merchant account. Imagine not being able to accept card payments. For most businesses, that's game over.
The Financial And Reputational Fallout
A data breach is the nightmare scenario, and the fallout is nothing short of devastating. You’ve got the immediate costs—forensic investigations, legal battles, and regulatory fines. But the long-term damage is what truly hurts.
When you lose customer data, you lose trust. It evaporates overnight, and rebuilding that reputation can take years, if it’s even possible. Customers will walk, and the bad press can poison your brand image for a long time. So, let’s be clear: PCI compliance isn't just about dodging fines; it's about protecting the very relationship you have with your customers. For a deeper dive, you can explore the full consequences of PCI non-compliance.
Common Mistakes UK Businesses Make
Too many businesses stumble into the same old traps, putting themselves at massive risk. One of the biggest mistakes is thinking that because your payment provider is PCI compliant, you automatically are too. That's a dangerously false assumption. While using a third-party processor certainly helps, you are still on the hook for securing your own environment.
Another common pitfall is simply mishandling sensitive card data. We see it all the time:
- Jotting down card details: Writing PANs or CVVs on sticky notes or saving them in unsecured spreadsheets is a clear violation.
- Recording card numbers in calls: If your call recordings capture spoken card details, your entire phone system is dragged into scope.
- Emailing payment information: Sending card details over unencrypted email is like sending them on a postcard for anyone to read.
These simple slip-ups can have enormous consequences. The contact centre is a real hotspot for this kind of risk. The moment an agent hears or sees a customer's card number, that single interaction can pull your whole IT infrastructure—from call recorders and agent PCs to network switches—into the crosshairs of a PCI DSS audit.
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. In the UK, every merchant must comply, as non-compliance risks fines up to £17.5 million or 4% of annual turnover under UK GDPR.
This isn't just a theoretical danger. UK card fraud soared past £0.5 billion in a recent 12-month period. And card-not-present fraud—the kind that happens over the phone or online—accounted for over 80% of that staggering sum. You can learn more about the UK compliance landscape and common mistakes on silver-lining.com.
How To Radically Reduce Your PCI Scope And Costs
Wrestling with PCI DSS can feel like a costly, never-ending headache, especially if you run a contact centre. But what if there was a way to sidestep the most painful parts of compliance altogether? The single most effective strategy for making your life easier and saving a lot of money is PCI scope reduction.
The idea is beautifully simple: make sure sensitive cardholder data never touches your systems, your network, or your people. By building a wall between your business environment and those raw payment details, you take yourself out of the most high-risk (and high-cost) parts of the PCI equation.
This isn't just about making audits less painful. It's about fundamentally changing how you handle payments, turning a sprawling, complex compliance nightmare into a manageable, straightforward process.
The Power Of Channel Separation
The magic behind scope reduction lies in a principle called channel separation. Picture a customer on the phone, ready to pay. Traditionally, your agent would hear their card number, type it into a computer, and the call recorder would capture it all. Just like that, your agent, their PC, the phone system, the call recorder, and your entire network are all ‘in scope’ for PCI DSS.
Modern solutions throw that old script out the window. They create a secure, isolated channel for the payment information to travel through, completely bypassing all of your internal infrastructure.
By stopping cardholder data from ever entering your environment, you can shrink your PCI DSS scope by as much as 90-95%. This dramatically cuts the number of security controls you need to worry about, monitor, and have audited.
Think of it this way: your systems never see, hear, or store the toxic data. As a result, your compliance burden plummets, and so do the costs and risks that come with it.
Proven Technologies For Scope Reduction
This isn't theoretical; it’s made possible by two key technologies that work in tandem to protect card data during a payment. They are incredibly effective, particularly in a busy contact centre.
DTMF Masking and Suppression: You know those tones your phone makes when you press the keypad? That's DTMF (Dual-Tone Multi-Frequency). Instead of the customer reading their card number out loud to an agent, they simply type it into their phone's keypad. The tones are masked so the agent can't decipher them, and the data is routed straight to the payment gateway, bypassing your systems completely. Your agent stays on the line to help the customer, but they never touch the sensitive data.
Tokenization: Once the payment gateway processes the transaction, it sends back a "token"—a secure, randomly generated string of characters that acts as a stand-in for the customer's actual card details. This token is completely useless to a fraudster but is safe for you to store in your CRM for things like processing refunds or setting up recurring payments. You get all the operational data you need without the risk of holding onto the raw card numbers.
Together, these technologies create a smooth payment experience where everything happens securely in the background, without exposing your business to unnecessary risk.
A Real-World Example: Before And After
Let's look at a housing association that takes rent payments over the phone.
Before Scope Reduction:
An agent asks a tenant for their card details. The numbers are spoken out loud, captured on call recordings, and keyed into a payment application on the agent's desktop. The entire contact centre infrastructure—desktops, servers, call recorders, and the network—is now in scope. This means a massive audit, frequent vulnerability scans, penetration tests, and hundreds of complicated controls. The cost is huge, and the threat of a breach is ever-present.
After Implementing a Solution like Paytia’s Secureflow:
The agent starts the payment process, but now the tenant enters their card details using their phone keypad. DTMF masking technology captures the numbers and sends them directly to the payment gateway. On-screen, the agent sees masked digits (like **** **** **** 1234), confirming the input without ever seeing the full card number. The payment is approved, and a secure token is sent back to the housing association's system for their records.
The change is profound.
Traditional vs Scope-Reduced Payment Processing
The table below really highlights the difference a scope-reduction solution like Paytia can make for a contact centre's daily operations and compliance overhead.
| Area Of Operation | Traditional Method (High PCI Scope) | Scope-Reduced Method (e.g., Paytia) | Compliance Impact |
|---|---|---|---|
| Agent's Role | Hears and types in full card details. | Guides customer; never sees or hears card data. | Removes agent desktops from PCI scope. |
| Call Recording | Captures sensitive spoken card numbers. | Pauses or masks audio during payment entry. | Removes call recording systems from scope. |
| Network | Transmits unencrypted card data internally. | Data is encrypted and sent directly to gateway. | Drastically reduces network scope. |
| Validation | Requires a complex, multi-question SAQ-D. | Qualifies for the simplest SAQ-A. | Simplifies annual validation from hundreds of questions to just a handful. |
By making this shift, the housing association moves from a state of high risk and complexity to one of security and simplicity. Their compliance workload is slashed, their costs are lower, and both their staff and tenants are far better protected. This is the modern, intelligent way to handle PCI compliance.
Your Actionable PCI Compliance Checklist
Getting PCI compliant—and staying that way—can feel like a mountain to climb. But if you break it down into a clear, step-by-step roadmap, that daunting challenge becomes a much more manageable project. Think of this checklist less as a list of rules and more as a practical plan to guide you from start to finish.
The trick isn't to get bogged down by all 12 requirements at once. Instead, the smart approach is to focus on understanding and controlling your specific payment environment. This makes the whole process far more efficient.
1. Map Everywhere Card Data Flows
You can't protect what you don't know you have. The first step is to become a detective and trace the entire journey of payment information through your business. Draw up a detailed diagram that follows the data from the moment a customer shares their details to where it’s processed and eventually stored.
This exercise is often an eye-opener. You might discover that sensitive card numbers are lurking in unexpected places, like call recordings or temporary log files you never knew existed. A solid data flow map is the bedrock of your entire compliance strategy.
2. Define Your Cardholder Data Environment
With your data map in hand, you can now officially define your Cardholder Data Environment (CDE). Your CDE is made up of all the people, processes, and technologies that store, process, or transmit cardholder data. This includes everything from your agents' desktops and phone systems to your network routers and payment servers.
Defining your CDE accurately is absolutely crucial. Why? Because these are the components that fall under the full, rigorous scope of the PCI DSS requirements. Anything outside this defined boundary has a much lighter compliance burden.
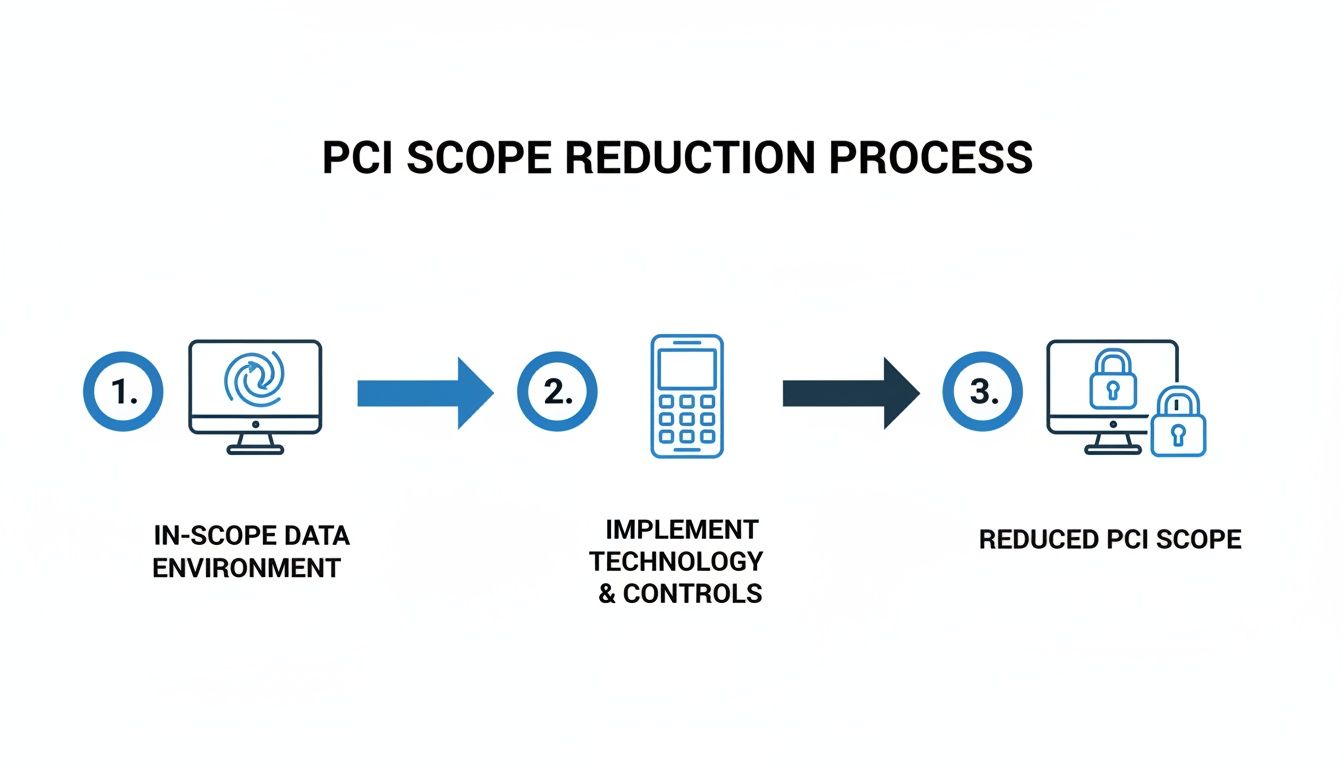
3. Assess and Shrink Your PCI Scope
Now it’s time to get ruthless. Take a hard look at your CDE and ask one simple question at every turn: do we really need this system to touch card data? The goal here is to make your CDE as small as humanly possible. The fewer systems involved, the smaller your PCI scope.
This is where clever technology can completely change the game.
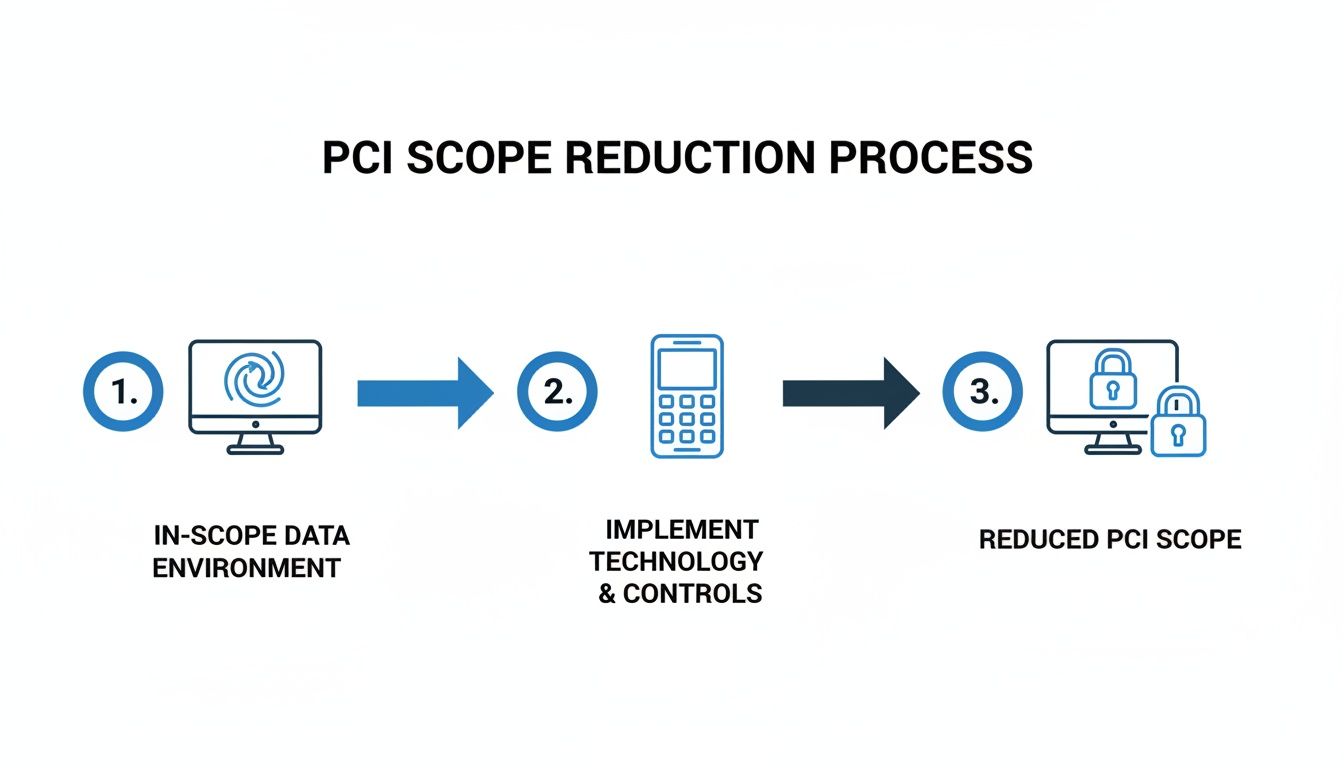
By putting solutions in place that keep payment data separate from your environment, you dramatically reduce what needs to be secured and audited.
4. Implement Scope Reduction Solutions
This is where you make your big move. By bringing in technologies like DTMF masking and tokenization, you can prevent sensitive cardholder data from ever entering your CDE in the first place. This strategy doesn't just shrink your scope; for many businesses, it almost eliminates it entirely.
The practical outcome? Your validation process often simplifies down to filling out the easiest possible Self-Assessment Questionnaire (SAQ).
5. Complete Your Annual Validation
Finally, with all your controls in place and your scope whittled down, it's time to complete your annual validation. For most organisations that have successfully reduced their scope, this just means completing a straightforward SAQ. This is your formal declaration that you are meeting your compliance obligations.
For a deeper dive, our comprehensive PCI DSS compliance checklist can walk you through every detail.
Frequently Asked Questions About PCI Compliance
Even with the best guides, some questions about PCI compliance always seem to surface. Let's tackle a few of the most common ones I hear from businesses to clear up any lingering confusion.
Is PCI Compliance a One-Time Project or an Ongoing Effort?
This is a big one, and getting it wrong can be a costly mistake. PCI compliance is not a "set it and forget it" task. It's a continuous, year-round commitment to security.
Think of it like getting your car MOT’d. You don't pass the test once and assume the vehicle is safe for life. You have to keep up with regular maintenance—checking the tyres, topping up the oil—to keep it running securely. The same principle applies here. PCI compliance demands constant attention, regular security scans, and annual validation to stay ahead of new and evolving cyber threats.
In fact, reports show that less than half of organisations manage to maintain their compliance status year after year, which really underscores how crucial this ongoing effort is.
Does My Payment Processor’s Compliance Cover My Business?
This is probably the most dangerous myth out there. Using a PCI-compliant payment processor is a vital first step, but their compliance does not automatically make your business compliant.
Your processor manages the heavy lifting of payment authorisation and settlement, but you are still responsible for the security of your own environment where you capture those payments. If your systems, your agents, or your processes come into contact with cardholder data in any way—even if it's just being read out over the phone—you have your own set of compliance obligations to meet.
Your payment processor’s compliance is just one piece of the puzzle. Your business is always accountable for securing its part of the payment journey.
How Much Does It Really Cost to Become Compliant?
There’s no single price tag for PCI compliance; it really depends. The final cost is shaped by your merchant level, how complex your payment environment is, and what security measures you already have in place.
For a small business with a straightforward setup, the costs might just be for the annual validation and quarterly vulnerability scans. But for a large organisation with a sprawling cardholder data environment (CDE), the investment can be significant. This could include:
- Annual Audits: A QSA-led Report on Compliance (ROC) can easily run into the tens of thousands of pounds.
- Security Tools: This covers essentials like firewalls, encryption software, and anti-malware solutions.
- Remediation: The budget needed to fix any security gaps found during your assessments.
- Scope Reduction Solutions: While these have an upfront cost, tools that reduce your PCI scope often deliver a fantastic return on investment by slashing long-term audit and maintenance expenses.
At the end of the day, the potential cost of non-compliance—from fines and reputational damage to lost customer trust—is always far, far higher than the investment in getting it right from the start.
At Paytia, we specialise in making this whole process much simpler. Our Secureflow platform is designed to remove your systems from the scope of PCI DSS entirely, transforming what could be a complex and expensive audit into a straightforward validation. Discover how you can cut your compliance costs and risks by visiting Paytia.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
