
A Complete Guide to Secure Card Payment Over Phone
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
When a customer calls to pay for something, a card payment over phone happens when they read their credit or debit card details aloud to one of your agents. While this used to be business as usual, it's now a method riddled with serious security and compliance risks, putting both your customers' data and your company's reputation on the line.
Why Old Ways of Taking Phone Payments No Longer Work

Think about it this way: would you read your card details out loud in a busy coffee shop to pay for something online? Of course not. It feels incredibly risky because it is. For years, however, businesses have asked customers to do the digital equivalent over the phone, creating a huge gap between modern security standards and outdated, risky practices.
Today's customers expect their payment experiences to be both quick and completely secure. We've seen a massive shift in consumer behaviour to prove it. In the UK, for example, contactless payments now account for nearly a third (32%) of all transactions. This isn't just a trend; it's a clear signal that people demand security and simplicity. You can explore more on UK payment trends in this report.
The Core Problem with Verbal Payments
The moment a customer reads their card number, expiry date, and CVC code to an agent, that highly sensitive information enters your business environment. This single act of verbal exchange opens the door to immediate and significant vulnerabilities.
- Agent Exposure: Your agent hears and might even jot down the full card details. This creates a direct opportunity for everything from accidental exposure to deliberate fraud.
- System Contamination: The data can easily end up in call recordings, saved on an agent's desktop in a note-taking app, or scribbled on a piece of paper. Suddenly, that sensitive data is everywhere.
- A Compliance Nightmare: This simple process drags your entire contact centre—every phone, network, and agent workstation—into the scope of the Payment Card Industry Data Security Standard (PCI DSS).
The fundamental flaw of traditional phone payments is simple but critical: sensitive financial data is unnecessarily exposed to people and systems that should never have access to it. This exposure is the root cause of compliance failures and security breaches.
Falling Short of Modern Standards
Old-school methods for taking a card payment over phone just don't cut it anymore. They are completely out of step with today's data protection reality. Regulators and card companies have strict rules to protect consumers, and the penalties for getting it wrong can be crippling. Trying to work around the problem with manual fixes like pausing call recordings or enforcing "clean desk" policies is simply not reliable enough—they don't address the core risk.
This guide will break down why these legacy approaches are unsustainable. More importantly, we'll walk you through modern, secure solutions that protect your business, safeguard your customers, and transform a high-risk process into a smooth, trust-building experience. We'll explore the technologies that make secure phone payments not just possible, but practical for any organisation.
Comparing Secure vs Insecure Phone Payment Methods
Deciding how to take a card payment over the phone can feel a bit like choosing between a dusty old road map and a modern GPS. Both might get you where you're going, but one path is littered with risks, while the other offers a clear, secure, and much more efficient route. This choice is vital, as it directly impacts your security, compliance, and the trust your customers place in you.
On one side, you have the high-risk, legacy methods that many businesses still cling to, often just out of habit. These old-school approaches force your agents and internal systems to handle sensitive card details directly, creating a massive operational headache. On the other, you have modern, secure technologies designed from the ground up to take that risk completely off your plate.
The Pitfalls of Insecure Legacy Methods
So, what makes a method "insecure"? It all comes down to one critical flaw: they expose raw, sensitive payment data to your people and your infrastructure. Imagine asking someone to whisper their bank PIN to you in a crowded room—even if you mean well, the risk of it being overheard is huge.
Two common but dangerously outdated practices fall squarely into this category:
- "Pause and Resume" Call Recording: This technique involves stopping the call recording when a customer reads out their card details. While it sounds sensible in theory, it’s notoriously unreliable in practice. Human error is a constant risk, and even if the recording is paused correctly, the live agent still hears and processes the card information. Your business remains exposed and non-compliant.
- "Clean Room" or "Clean Desk" Policies: This approach relies on strict office rules that forbid agents from writing down card details. The problem? It's almost impossible to enforce and audit effectively. A single sticky note or an unsaved text file on an agent's desktop is all it takes to cause a major data breach and instantly violate PCI DSS rules.
The fundamental issue with these legacy methods is that they try to manage risk instead of eliminating it. They place an enormous burden of trust on every single agent and every piece of technology, a model that simply isn't sustainable or truly secure in today's world.
When you consider the potential for increased credit card payment defaults, it serves as a stark reminder of why old and insecure phone payment methods just aren't viable anymore.
The Power of Modern Secure Solutions
In stark contrast, modern solutions are built on the principle of data isolation. Their goal is simple: make sure sensitive card information never enters your business environment in the first place. This completely changes the game for both security and compliance.
Here are the key technologies leading the charge:
- DTMF Masking (Keypad Payments): This clever technology lets a customer enter their card number using their telephone keypad. The DTMF (Dual-Tone Multi-Frequency) tones they press are intercepted and masked before they ever reach the agent or the call recording system. The agent just hears a flat, unrecognisable tone, while the data goes straight to the payment processor, completely bypassing your systems.
- Secure IVR Payments: An Interactive Voice Response (IVR) system gives customers a way to pay 24/7 without ever needing to speak to an agent. They simply follow an automated menu to securely enter their payment details, offering total convenience for them and zero data exposure for you.
- Agent-Assisted Digital Payments: While on a call, an agent can send the customer a secure payment link via SMS or email. The customer opens the link on their smartphone or computer and completes the transaction on a secure webpage, with options like Apple Pay or Google Pay. The agent can track the payment's progress in real-time but never sees a single card detail.
This table gives a bird's-eye view of how these different approaches stack up.
Comparing Phone Payment Capture Methods
| Method | Security Level | PCI DSS Scope Impact | Customer Experience | Common Use Case |
|---|---|---|---|---|
| Pause & Resume | Low | High - Full scope applies to agents, networks, and systems. | Poor - Customers are often wary of reading details aloud. | Outdated contact centres. |
| DTMF Masking | High | Very Low - Removes agents and call recordings from scope. | Good - Customers feel more secure using their keypad. | Agent-led payment calls. |
| Secure IVR | High | Very Low - A fully automated and isolated process. | Excellent - Offers self-service convenience and security. | 24/7 automated bill payments. |
| Digital Payment Links | High | Very Low - Payment occurs outside your environment. | Excellent - Modern, fast, and uses familiar digital wallets. | Agent-assisted payments for tech-savvy customers. |
Once you see the fundamental differences laid out like this, it becomes clear why switching to a secure method isn't just about ticking a compliance box. It’s a strategic business decision that protects your reputation and builds lasting customer trust.
How DTMF Masking Makes Phone Payments Secure
When a customer needs to make a card payment over the phone, the single biggest hurdle is protecting their sensitive information. How do you securely capture their details while an agent is live on the call? The answer is a clever bit of technology called DTMF masking.
Think of it as a secure, private tunnel created just for payment details. DTMF stands for Dual-Tone Multi-Frequency—the unique sounds each number on your phone's keypad makes. This technology intercepts those tones the moment a customer presses a key, stopping them before they can ever reach your agent, your call recordings, or anywhere else on your network.
The Secure Tunnel Analogy
Let’s use an analogy. Imagine your customer needs to send a highly sensitive package (their card details) to the bank (your payment processor). An insecure way to do this would be to give the package to your agent, who then has to walk it through your office before sending it on. Along that route, anyone could potentially see or handle it.
DTMF masking, on the other hand, is like giving the customer a pneumatic tube, just like the ones at a drive-through bank. The customer places their package directly into this tube, and it shoots straight to the bank's vault, completely bypassing your agent and your office. Your agent can still talk to the customer and confirm the package arrived safely, but they never once touch or see its contents. This is exactly how DTMF technology isolates and protects payment data.
The graphic below shows the difference between a risky, insecure process and a secure one using DTMF.
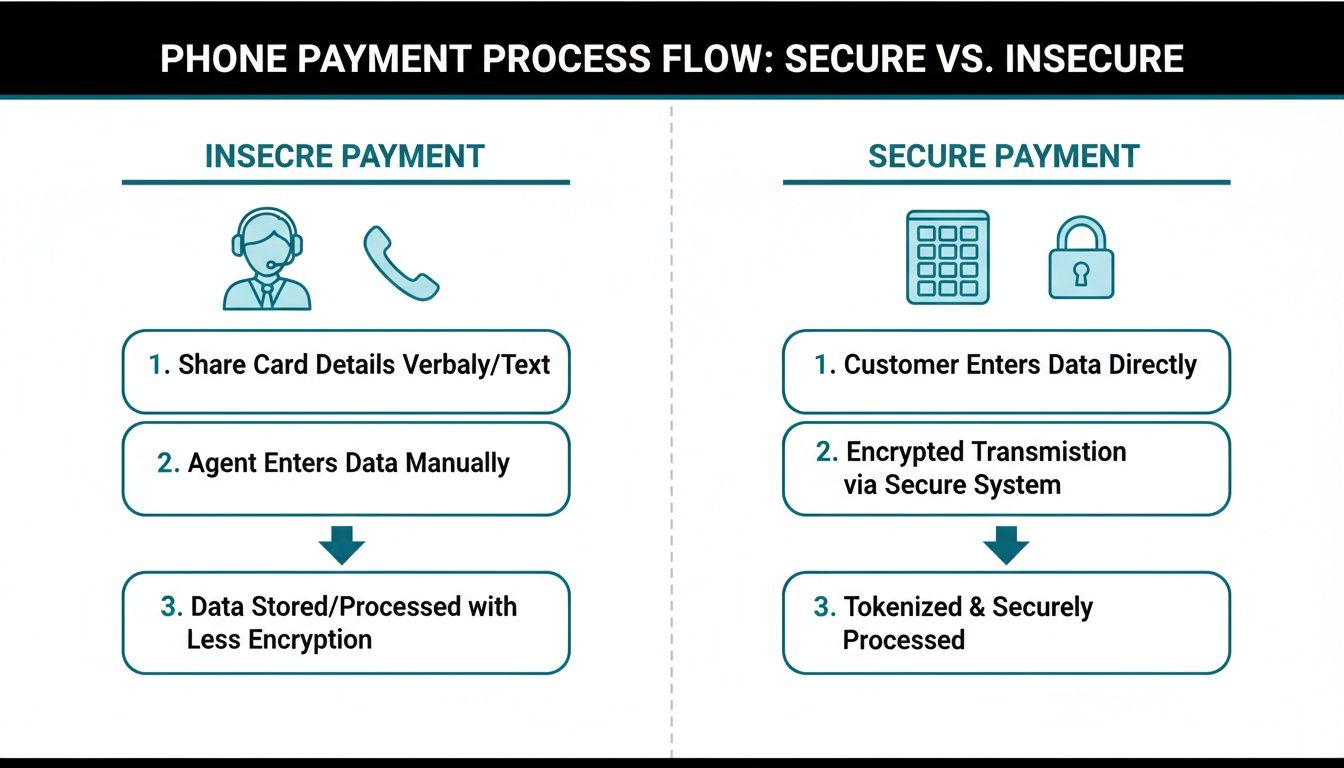
This side-by-side comparison makes it clear. The secure flow on the right removes the agent from the equation of handling sensitive data, creating a direct and protected path for the information to travel.
How the DTMF Process Works Step by Step
The beauty of DTMF masking lies in its simplicity for both the customer and the agent, even with all the sophisticated work happening behind the scenes. The whole process feels seamless and fits naturally into the live conversation.
Here’s what a typical workflow for a secure card payment over the phone looks like:
- Agent Initiates Payment: When it’s time to pay, the agent informs the customer they are about to securely capture their card details and activates the secure payment mode in their system.
- Customer Enters Details: The customer uses their telephone keypad to type in their 16-digit card number, expiry date, and CVC code.
- Tones are Intercepted and Masked: As the customer presses each key, the DTMF masking solution instantly intercepts the tones. The agent and call recording system only hear a flat, monotonous beep for each keypress, making it impossible to identify the numbers.
- Data is Encrypted and Sent: Those intercepted tones are immediately converted into encrypted data.
- Direct Transmission to Processor: This encrypted data is sent directly to your payment processor for authorisation. Crucially, it never travels through your company’s phone lines, networks, or computer systems.
- Agent Receives Confirmation: A real-time notification pops up on the agent’s screen confirming if the payment was successful or declined. They can then relay this to the customer and wrap up the call.
The core benefit here is profound: sensitive cardholder data is completely removed from your environment. By preventing this data from ever touching your systems, you dramatically shrink your PCI DSS compliance scope. You can learn more about how DTMF masking is a cornerstone of PCI compliance.
The Impact on Your Business and Agents
Putting DTMF masking in place has a powerful, positive ripple effect across your entire operation. Your agents can stay on the line to guide and support customers through the payment without ever being exposed to their financial information. This single change eliminates the risk of both accidental data leaks and internal fraud.
Ultimately, this technology lets your contact centre do what it does best—be a hub for excellent customer service—while completely removing the liability and complexity of handling raw payment data. It transforms a high-risk interaction into a secure, compliant, and trust-building experience for everyone involved.
Getting to Grips with PCI DSS for Phone Payments
The moment your business takes a card payment over the phone, you’ve entered the world of the Payment Card Industry Data Security Standard (PCI DSS). This isn't just another bit of corporate admin; it’s a vital set of security rules with a single, crucial mission: to keep your customers' card details safe from fraudsters and data thieves.
For any company, but especially for contact centres, getting these rules right is non-negotiable. Think of PCI DSS as the blueprint for building a secure payment environment. Ignoring it is like leaving your front door unlocked – you’re inviting huge financial penalties, brand damage, and a complete breakdown of customer trust.
Why Contact Centres are a Unique Challenge
A typical contact centre is a real minefield when it comes to PCI DSS compliance. As soon as a customer reads out their card number, that sensitive information starts a journey through a complex web of systems and human interactions, with each step being a potential security weak spot.
Here’s where things often go wrong:
- Unsecured Call Recordings: Do you record calls for training or quality checks? If so, any recording that captures payment details becomes a toxic asset. You're essentially storing sensitive data in an unprotected format, making it a goldmine for anyone looking to steal it.
- Vulnerable Agent Desktops: An agent's computer is another major risk area. Card numbers can easily end up in notepad files, unsaved documents, or even just sitting in the system's memory – all of which fall under the microscope of a PCI audit.
- Human Error and Insider Threats: Relying on manual workarounds like "Pause and Resume" for recordings or enforcing clean desk policies is fundamentally unreliable. All it takes is one mistake—an agent forgetting to hit pause or scribbling a CVC number on a sticky note—to cause a major compliance breach.
These vulnerabilities don't just create risk; they massively expand what's known as your PCI DSS scope. This term covers all the people, processes, and technology that touch cardholder data in any way. The bigger your scope, the more complicated, time-consuming, and expensive it becomes to secure and audit everything properly.
How Technology Can Solve the Compliance Puzzle
The good news? Modern payment technology is built to tackle these risks head-on. Instead of trying to bolt security onto a leaky process, solutions like DTMF masking stop the sensitive data from ever entering your environment in the first place.
This idea of isolating the data is a complete game-changer for compliance. When card details are captured and sent directly to the payment processor—bypassing your agents, your call recordings, and your internal network entirely—it dramatically shrinks your compliance footprint. It’s important to understand how to meet these security mandates; similarly, you can find a comprehensive resource in a technical guide to SOC 2 compliance requirements, which shares many of the same data protection principles.
By implementing a secure phone payment solution, you can systematically pull your entire contact centre out of PCI DSS scope. This can slash the number of systems you need to audit and protect by as much as 95%.
This isn't just a technical win; it delivers huge real-world benefits. We're talking about fewer systems to secure, much simpler audits, and a significant drop in compliance costs. You can learn more by exploring our detailed guide on the core PCI DSS requirements and what they mean for your business.
Ultimately, making your voice channels PCI DSS compliant isn’t about piling more rules and restrictions onto your agents. It's about putting the right technology in place to remove the risk completely. This frees you up to focus on what really matters: giving your customers brilliant service, with total peace of mind.
Bridging The Gap: Digital Payments in a Voice Call

While keypad payments offer rock-solid security, we can't ignore the world outside the contact centre. Customers are now completely at home with the one-tap ease of digital wallets, and that expectation is changing the game. This shift gives us a brilliant opportunity to blend the human touch of a phone call with the slick security of a modern digital payment. So, instead of being limited to keypad entry, agents can now guide a customer through a payment that happens entirely on their own device.
It works like this: while still on the call, the agent triggers a secure payment link and sends it straight to the customer's phone via SMS, email or even a web chat window. The customer just clicks the link, which opens a secure, branded payment page. From there, they can pay how they want — whether that’s with Apple Pay, Google Pay, or by typing in their card details.
What This Looks Like in Practice
Let’s imagine a customer calls up to settle an overdue bill. Rather than the old routine of asking them to fish out their credit card and read the numbers aloud, the whole process becomes far more elegant and secure.
- The Agent Initiates: After confirming the amount with the customer, the agent starts the process.
- A Secure Link is Sent: With a click, a unique, single-use payment link is sent to the customer’s mobile phone.
- The Customer Pays Digitally: The customer taps the link, and a secure payment page opens. They can then use their phone's built-in security, like Face ID or a fingerprint, to authorise the payment instantly with their digital wallet.
- Real-Time Confirmation: Back on the agent's screen, the system updates in real-time to confirm the payment was successful. The agent can then confirm this with the customer and wrap up the call.
The beauty of this is how smooth it is. The agent stays on the line the whole time, ready to help if needed, but they never see or hear any sensitive card information. This keeps the entire interaction secure and fully compliant.
Meeting Customers Where They Are
This move towards agent-guided digital payments isn't just a gimmick; it’s a direct response to a massive shift in how people manage their money. The use of digital and mobile wallets by UK adults skyrocketed from just 14% in 2017 to 47% by 2022. With 11.8 million people in the UK regularly using contactless mobile payments, it’s obvious that reading card numbers over the phone feels increasingly outdated and insecure to many. You can read more about the UK's mobile payment market.
When you offer a digital payment link during a phone call, you’re doing more than just offering convenience. You’re building trust. You’re showing your customers that you take their data security seriously and are giving them the power to pay in a way that feels comfortable and familiar.
This kind of flexibility is key. Giving customers a choice between secure options—like DTMF keypad tones and digital payment links—shows you understand and respect their preferences. To learn more, you can check out our guide on how to implement alternative payment methods.
Ultimately, this modern take on a card payment over phone elevates a routine transaction into a positive experience, strengthening customer satisfaction and loyalty without ever compromising on security.
How to Implement a Secure Phone Payment System
Making the move to a modern, secure way of taking a card payment over the phone doesn’t have to be a massive headache. It's less about a huge technical overhaul and more about choosing the right partner and following a clear path. The goal is simple: protect your customers and your business without grinding your operations to a halt.
It all starts with sizing up potential providers. The first thing you need to look at is how well their solution will slot into what you’re already using. A great system should play nicely with your existing telephony (like VoIP or CCaaS) and your Customer Relationship Management (CRM) software. This way, the new payment process feels like a natural part of an agent's daily routine, not some clunky, bolted-on task.
Finding the Right Technology Partner
Beyond just plugging things in, security certifications are an absolute must. Don't even consider a provider that isn't Level 1 PCI DSS certified—it’s the highest stamp of approval available. This certification is your guarantee that they meet the most rigorous security standards, giving you peace of mind that your payment process is built on a rock-solid foundation of trust.
As you weigh your options, keep these points in mind:
- Payment Gateway Support: Can the provider work with your current payment gateway, or are they going to force you to switch? A bit of flexibility here can make the transition a whole lot smoother.
- Scalability: You need a system that can keep up as your business grows. Will it handle more agents or cope with those crazy seasonal spikes in call volume?
- Reporting and Analytics: Good data is gold. You'll need access to detailed reports to keep an eye on performance, track how many payments go through successfully, and make reconciliation less of a chore.
The Implementation Journey, Step by Step
Once you've picked your partner, the rollout usually follows a pretty straightforward plan designed to get your team up and running quickly with minimal disruption. While every setup has its own quirks, the journey typically looks something like this.
- Initial Chat and Discovery: The first step is a proper deep dive into how you work now. Your provider will sit down with you to get a handle on your specific call flows, the tech you're using, and your compliance needs.
- System Setup and Configuration: Armed with that knowledge, the tech team gets to work configuring the platform to fit your world. This is where they’ll link it up with your phone system and payment gateway.
- Agent Training and Onboarding: This part is key. Training should be quick and to the point, showing agents exactly how to kick off a secure payment, talk the customer through it, and understand what they’re seeing on their screen. Honestly, the best systems are so intuitive they barely require any training at all.
- Testing and Go-Live: Before you flick the switch for everyone, the system gets a thorough test run in a safe environment to catch any gremlins. Once everyone gives it the thumbs-up, you’re live. From that moment on, you’re processing phone payments that are fully secure and compliant.
The whole point is to take the mystery out of upgrading your payment security. With a bit of planning, it’s a perfectly manageable project that improves how you work from day one, giving you an immediate win on both compliance and security without throwing a spanner in the works.
Your Questions Answered: Getting Phone Payments Right
As you start looking into better ways to handle a card payment over the phone, a few questions are bound to pop up. Let's walk through some of the most common ones with clear, straightforward answers to help you navigate the world of secure and compliant phone payments.
Is It Actually Compliant to Take Card Payments Over the Phone?
Yes, it absolutely is—if you use a PCI DSS validated solution. The old way of asking a customer to read out their card details to an agent is a massive compliance risk, especially if calls are recorded or the agent's desk isn't a completely sterile environment.
Modern tools like DTMF masking or secure payment links are built for this very reason. They work by ensuring sensitive card information never even enters your business environment. That's the key to a genuinely secure process.
What’s the Difference Between DTMF Masking and 'Pause and Resume'?
Honestly, they're worlds apart in terms of real security. 'Pause and Resume' is a manual workaround where someone physically stops the call recording while a customer shares their card details. It's notoriously prone to human error and still leaves the live agent, and your entire network, exposed to raw payment data.
DTMF masking, on the other hand, is an automated technology. It cleverly captures the tones from a customer's keypad and sends them straight to the payment gateway. This means the card details never touch your systems at all. It's a far more robust approach that provides guaranteed compliance in a way manual methods simply can't.
Think of it like this: 'Pause and Resume' tries to manage a risk, and often fails. DTMF masking eliminates the risk completely by taking sensitive data out of the equation.
How Does a Secure Payment System Affect My Customer Experience?
It improves it, massively. Customers feel far more comfortable when they know their card details aren't being heard by an agent or jotted down on a piece of paper. This instantly builds a huge amount of trust. The process is also quicker and just feels more professional all around.
When you offer up-to-date options, like secure links that let customers use digital wallets like Apple Pay, you're sending a powerful message. You're showing that you take their data security seriously, which is a major factor in winning and keeping customer loyalty these days.
Can These Secure Systems Integrate with the Software I Already Use?
Absolutely. The leading secure payment platforms are designed to play nicely with others. They are built to connect with a wide range of telephony systems (like VoIP or CCaaS platforms), CRMs, and payment gateways, so they slot into your existing workflows without causing disruption.
The best providers will offer solid APIs and pre-built connectors to make the whole implementation process smooth. It allows you to add that essential layer of security and compliance without having to rip out and replace the systems your team already knows and uses every day.
Ready to eliminate risk and build customer trust with every single transaction? Paytia provides a PCI DSS Level 1 certified platform that removes sensitive payment data from your environment, making every card payment over the phone secure and compliant. Learn more and see how it works at https://www.paytia.com.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
