
Secure Code for Credit Card: PCI-Ready Practices for Your Contact Center
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
When people talk about a credit card's "secure code," they're almost always referring to that little three or four-digit number printed on the card itself. It’s your first line of defence, proving you physically have the card when you're buying something online or over the phone.
What Is a Secure Code for a Credit Card?

That secure code might be small, but it does a massive job. It’s a powerful weapon against fraud for any purchase where you can’t physically swipe or tap your card – what the industry calls a Card-Not-Present (CNP) transaction.
Think of it this way: your long credit card number is like your home address. If a fraudster gets hold of it, they know where you live. But the secure code? That’s like the key to your front door. Just knowing the address isn't enough to get inside. It’s a simple, yet crucial, verification step.
Getting the Terminology Right
While we often use "CVV" as a catch-all term, the official name actually changes depending on who issued your card. This can get a bit confusing, but they all serve the exact same protective function.
To clear things up, here’s a quick breakdown of what the different card networks call their codes.
Understanding Different Card Security Codes
| Code Type | Full Name | Location on Card | Primary Use Case |
|---|---|---|---|
| CVV2 | Card Verification Value 2 | 3 digits on the back (for Visa) | Verifying card is present for CNP sales |
| CVC2 | Card Validation Code 2 | 3 digits on the back (for Mastercard) | Verifying card is present for CNP sales |
| CID | Card Identification Number | 4 digits on the front (for Amex) | Verifying card is present for CNP sales |
Each of these codes is designed to confirm physical possession of the card during a remote transaction.
It’s also vital not to mix up this static, printed number with more dynamic security checks. For example, 3-D Secure (you might recognise it as 'Verified by Visa' or 'Mastercard SecureCode') is a completely different system. It adds another step, usually asking for a one-time password sent to your phone or app.
The CVV proves you have the card. 3-D Secure proves you are you. If you want to explore this further, check out our detailed guide on what a card security code is.
The brilliant part of this printed code is that it’s deliberately hard to steal digitally. It isn't stored in the magnetic stripe or the chip, which means card skimmers can't capture it.
This is exactly why handling the secure code for a credit card with extreme care is so important, especially in places like contact centres where customers have to read their sensitive details out loud.
The Real Dangers of Handling Customer Card Details
When an agent asks a customer to read out their credit card details, it feels routine. It's a standard part of taking a payment over the phone. But behind this everyday interaction lies a minefield of risk for your business, your agents, and, most critically, your customers.
Every time a secure code for a credit card is read aloud or typed into a chat, it leaves a trail. That sensitive data can easily get captured in call recordings, saved in chat transcripts, or even just jotted down on a sticky note on an agent's desk. Suddenly, you have highly valuable information sitting in unsecured places, creating a tempting target for fraudsters both inside and outside your organisation.
The Soaring Threat of CNP Fraud
This kind of manual data handling is a direct contributor to the growth of Card-Not-Present (CNP) fraud. This is where criminals use stolen card information to make purchases online or over the phone. The numbers paint a pretty stark picture of how vulnerable these payment methods have become.
In the UK, card fraud losses recently hit £556.3 million. A jaw-dropping 81% of that total came from CNP fraud. More recent figures show a worrying trend reversal, with CNP fraud cases jumping by 15%. This spike was largely fuelled by attacks on digital wallets and other remote payment systems, showing just how relentlessly criminals are targeting these channels. You can dive into the complete details in UK Finance's annual fraud report.
Your PCI DSS Nightmare Just Got Bigger
Beyond the immediate threat of fraud, manually handling card data massively expands your PCI DSS (Payment Card Industry Data Security Standard) scope. Think of PCI DSS as the rulebook for protecting cardholder information. It's notoriously complex, and meeting its requirements can be a serious drain on time and money.
By allowing card data to enter your environment—your phone systems, your networks, your agents' computers—you are taking on the full responsibility of protecting it. This means your entire contact centre operation is now subject to the demanding rules of PCI DSS.
This isn't just a minor headache; it's a huge operational and financial burden. To stay compliant, you'd have to put in place a whole raft of expensive and complicated controls across your entire infrastructure, such as:
- Secure Network Configuration: Rigorously managing firewalls and security protocols.
- Data Encryption: Encrypting any transmission of cardholder data over public networks.
- Strict Access Control: Implementing tight restrictions on who can view or handle card information.
- Regular Monitoring and Testing: Constantly scanning your systems for any potential weaknesses.
Ignoring compliance isn't really an option. The penalties for getting it wrong can include eye-watering fines, devastating damage to your reputation, and even losing the ability to accept card payments at all. It only takes one data breach to destroy the customer trust you've spent years building. That's why figuring out how to process payments without the sensitive data ever touching your systems isn't just a nice-to-have—it's a business essential.
How to Capture Payments Without Touching Card Data
So, how do you sidestep all these risks? The answer isn't about adding more locks and guards; it's about fundamentally changing how you handle payments in the first place. The most effective approach is to ensure your agents never see, hear, or touch sensitive card details at all.
Think of it as creating a protective bubble around the transaction. Instead of card information flowing through your systems where it can be intercepted or accidentally stored, modern payment technologies capture it in a way that completely isolates it from your agents, your call recordings, and your internal networks. This shift dramatically shrinks your security burden and, just as importantly, builds a foundation of trust with your customers.
The diagram below maps out the typical journey of risk when agents are exposed to card data, from the initial conversation to the potential for fraud.
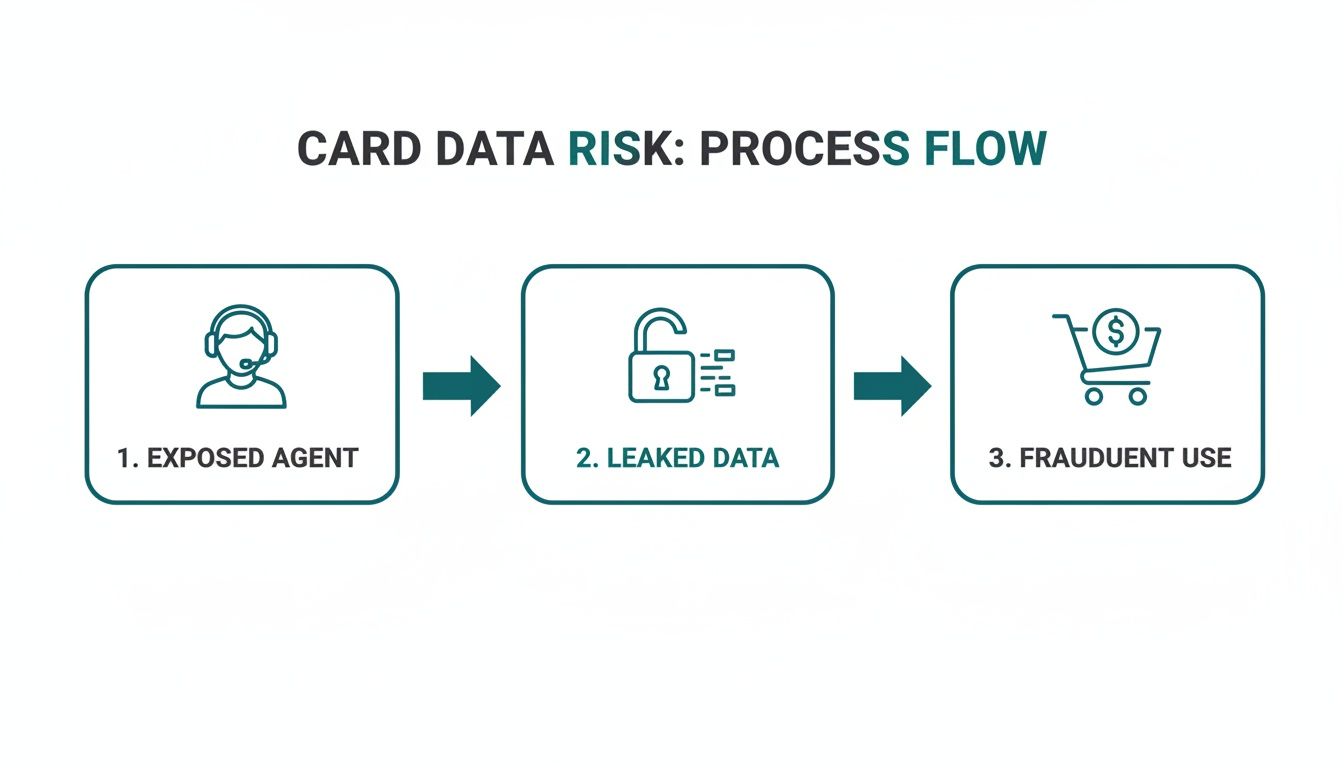
As you can see, direct exposure is the weak link that can lead to data leaks and misuse. This is precisely why secure capture methods are so critical.
Key Technologies for Secure Capture
Several clever technologies work behind the scenes to make this hands-off approach possible. Each one plays a specific role in shielding the secure code for a credit card and other details from your business environment, all while keeping the process smooth for both the customer and the agent.
Here’s a look at the core methods that make this possible.
Comparing Secure Payment Capture Methods
This table breaks down the main technologies used to secure card-not-present payments, giving you a quick comparison of how they work and what they achieve.
| Technology | How It Works (Analogy) | Primary Security Benefit |
|---|---|---|
| DTMF Suppression | The customer types their card numbers on their phone keypad. The system muffles the tones, like putting a "soundproof box" around them. | The agent can't hear the numbers, and the tones are never captured in call recordings. |
| Channel Separation | The agent guides the customer to a separate, secure channel (like a web form) to enter their details while staying on the line to help. | Card data completely bypasses the agent and the voice channel, entering directly into a secure payment gateway. |
| Tokenisation | After a payment, the actual card details are swapped for a unique, non-sensitive placeholder, much like a casino chip represents real money. | You can safely store the "token" for recurring payments or refunds without ever holding onto the actual card details. |
| End-to-End Encryption | From the moment the customer enters their details, the data is scrambled into an unreadable code, only to be unscrambled by the payment processor. | Even if intercepted, the data is just gibberish to anyone without the decryption key, protecting it in transit. |
By combining these methods, you create a payment environment where sensitive cardholder data, including the Primary Account Number (PAN) and the secure code, is completely isolated. It never even touches your infrastructure, which is the ultimate goal of PCI DSS compliance.
The Power of Payment Links
Another incredibly effective and popular method is using secure payment links. Instead of an agent taking details over the phone, they can send the customer a unique link via SMS, email, or web chat.
The customer simply clicks the link, which opens a secure, branded payment page where they can enter their card information themselves. It’s a self-service option that’s not only incredibly secure but also offers the kind of modern, convenient experience that many customers now expect.
It's a straightforward yet powerful way to completely de-scope your contact centre from the responsibility of handling payment data. To learn more about this approach, have a read of our complete guide to using payment by link. By adopting these technologies, you can transform payment security from a defensive headache into a real strategic advantage.
Achieving PCI DSS Compliance in Your Contact Centre

Trying to get your head around the Payment Card Industry Data Security Standard (PCI DSS) can feel overwhelming, especially in a bustling contact centre. But it doesn't have to be a headache. By embracing the right secure payment technology, you can shift compliance from a resource-draining chore to a real business asset that strengthens customer trust.
The guiding principle is surprisingly straightforward: if you don’t touch sensitive data, you don’t have to protect it. This is known as de-scoping. By using a platform that stops the secure code for a credit card and other payment details from ever hitting your systems, you dramatically reduce your compliance burden.
Slashing Your Compliance Scope
How much of a difference can it make? Implementing a modern secure payment solution can shrink your PCI DSS scope by a staggering 90-95%. That's because the most stringent parts of the standard are aimed at businesses that store, process, or transmit cardholder data. Take that data out of the equation, and most of those obligations simply vanish.
Think about it. Technologies like DTMF suppression and tokenisation mean you satisfy several key PCI DSS requirements right out of the box:
- Requirement 3: Protect Stored Cardholder Data: This becomes a non-issue. Your systems never store the data, so there’s nothing for you to protect.
- Requirement 4: Encrypt Transmission of Cardholder Data: The data is encrypted from end-to-end, completely bypassing your own networks.
- Requirement 7: Restrict Access to Cardholder Data: Problem solved. Your agents and internal systems never see or access the card details.
This is a far smarter and more watertight approach than trying to build a fully compliant environment from the ground up. For a more detailed breakdown, you can read our complete guide to the 12 PCI DSS requirements.
Solving Common Contact Centre Headaches
Beyond making audits less painful, a secure payment platform tackles real, everyday operational challenges. Call recording is a perfect example. If your standard recording system captures a customer reading out their card details, you're in direct breach of PCI DSS rules, which strictly forbid storing authentication data like the CVV.
Secure payment solutions neatly sidestep this conflict. By masking the keypad tones or using a separate, secure channel for the payment itself, the problem disappears. You can keep your full call recordings for quality and training, safe in the knowledge that no sensitive card data was ever captured.
With fraud on the rise, these protections are more crucial than ever. In the UK, fraudsters managed to steal £629.3 million in just the first half of a recent year, with over 2.09 million confirmed cases of fraud—a 17% jump. For any contact centre taking payments over the phone, these figures are a stark reminder of the risks. Exposing card details, even accidentally, can lead to a compliance nightmare.
Ultimately, de-scoping isn't just about ticking boxes for an annual audit. It's about fundamentally designing risk out of your business operations. It protects your customers, safeguards your reputation, and frees up your team to focus on what really matters: delivering fantastic service.
Choosing the Right Secure Payment Solution
Now that we’ve unpacked the risks and the tech designed to counter them, the next question is a practical one: how do you choose the right platform for your business? The market is crowded, and it’s easy to get bogged down in feature lists. But making the right call means looking past the sales pitch to the core capabilities that will genuinely protect your customers and make life easier for your team.
A truly great solution has to be flexible. Your customers might want to pay over the phone today, but through a web chat tomorrow, or even a video call next week. The platform you choose must handle all these channels without missing a beat, delivering a secure and consistent experience every single time.
This flexibility needs to extend to your own technology, too. The last thing you want is a clunky, isolated system that forces your team into awkward workarounds.
Evaluating Key Integration Capabilities
The best solutions slot neatly into the tools you already use every day. Look for platforms that offer seamless, out-of-the-box integrations, because this is what keeps your workflows humming and ensures you get real value from your investment.
When you're comparing options, make sure you can tick these boxes:
- CRM System: Can it link payment data (or, better yet, secure tokens) directly to your customer records?
- PBX and Telephony Platform: Will it play nicely with your current phone system without causing call-flow chaos?
- Payment Gateways: Does it support the payment processor you already work with, so you can avoid switching and extra costs?
Without these connections, you're just creating data silos and manual headaches—the very things you’re trying to eliminate.
Verifying Security and Compliance Credentials
Vendor promises are one thing, but independent certifications are what really count. These credentials are proof that a provider has been put through its paces by third-party auditors and meets the industry’s highest security standards. Think of them as non-negotiable.
The need for proven security has never been greater. Cifas, the UK’s fraud prevention service, recorded a staggering 217,000 fraudulent cases in just the first six months of a recent year. A huge part of this is identity fraud, with cases involving synthetic, AI-generated identities now making up 42% of all instances. This surge shows just how critical it is to work with platforms that have validated, robust defences. You can dig into the latest trends over at Fraudscape.co.uk.
When you're assessing a potential provider, always ask to see their certificates. The big ones to look for are PCI DSS Level 1, the top tier of compliance, and Cyber Essentials Plus, a UK government-backed scheme that shows a serious commitment to cyber security.
At the end of the day, picking a partner is about more than just software; it’s about entrusting a vital part of your business to an expert. By focusing on multi-channel support, smooth integrations, and top-tier certifications, you can confidently choose a solution that protects every secure code for a credit card and strengthens the trust your customers have in you.
What’s Next on Your Journey to Secure Payments?
We’ve covered a lot of ground, showing why protecting credit card secure codes isn’t just a good idea—it’s absolutely essential. We've also seen how the right technology can make this happen without turning your daily operations upside down. The main takeaway? Standing still is now the biggest risk to your business and your customers.
Bringing in a secure payment solution is about more than just ticking a compliance box. It’s a powerful way to build trust with your customers, make your contact centre more efficient, and create a business that's ready for whatever threats come next. Your first move should be to take an honest look at how you handle payments right now.
The real aim here is to get a clear picture of your current PCI DSS scope. This initial review will shine a light on where you're exposed and give you a solid starting point for making things better.
Once you have that baseline, you’ll be in a much better position to find a solution that properly secures every single transaction. Thinking ahead like this doesn't just fix today's security headaches; it prepares your entire payment system for the future. By getting sensitive data out of your environment completely, you’re not just protecting your reputation—you’re investing in the long-term health and integrity of your entire organisation.
Got Questions About Secure Card Handling? We've Got Answers
Stepping into the world of secure payments can feel like navigating a minefield of acronyms and rules. It’s natural to have questions, especially when you’re trying to do right by your customers and stay compliant. Let's tackle some of the most common ones we hear from businesses just like yours.
Can Our Agents Ask for the Security Code Over the Phone?
This is a big one, and the short answer is: you really, really shouldn't.
Asking a customer to read out their three-digit security code (CVV) over the phone is fraught with risk. If you record your calls for training or quality purposes—as most contact centres do—you’ve just stored sensitive authentication data. That’s a direct violation of the PCI DSS rules.
Even if you don't record calls, the code is still exposed to the agent. They might jot it down on a notepad or enter it into an unsecure chat window. It just creates a weak link in your security chain that fraudsters are all too happy to exploit.
The only truly safe and compliant path is to use technology that stops this data from ever reaching your environment in the first place. That way, your agent never sees, hears, or has to handle the customer's card details at all.
What’s the Difference Between a CVV and 3-D Secure?
It's easy to get these two mixed up, but they play very different roles in keeping a transaction safe.
CVV (Card Verification Value): This is the static, three or four-digit secure code for a credit card that's physically printed on the card. Think of it as a quick check to prove that the person making the payment actually has the card in their hand.
3-D Secure: This is a completely separate, interactive layer of security for online payments. You’ve probably seen it in action—it’s often branded as 'Verified by Visa' or 'Mastercard SecureCode'. It works by briefly sending you to your bank's website to enter a password or a one-time code sent to your phone.
So, to put it simply: the CVV proves you have the card, while 3-D Secure proves you are the person who owns it.
How Does Tokenisation Shrink Our PCI DSS Scope?
Tokenisation is a clever process that swaps out sensitive card data for a unique, non-sensitive placeholder called a 'token'. Imagine you're at a funfair and you swap your cash for ride tokens. Those tokens have value inside the fairground, but they're useless anywhere else. It’s the same principle.
This token can't be mathematically reversed to figure out the original card number or its security code. When you use a system that tokenises this information before it even touches your business systems, you've effectively walled off the sensitive data.
This has a huge impact on your PCI DSS compliance. The toughest rules are for systems that store or handle raw card details. By using tokens instead, you drastically reduce the parts of your business that fall under that intense scrutiny. Your teams only ever deal with the safe tokens, making your compliance journey a whole lot simpler.
Paytia offers a PCI DSS Level 1 certified platform that ensures sensitive payment data, including the secure code for credit card payments, never enters your environment. Discover how our secure payment solutions can take compliance headaches off your plate and build lasting customer trust. Find out more at https://www.paytia.com.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
