
Understanding what is security code on card and how it protects you
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
You’ve probably seen it a thousand times when buying something online: that little box asking for a three or four-digit security code from your card. This small number is a surprisingly powerful security feature, especially for any purchase where you can’t physically hand your card over.
Think of it as a final checkpoint. Its job is to prove you have the actual, physical card in your possession during an online or over-the-phone transaction. While Visa calls it a CVV and Mastercard uses CVC, they all do the same critical job: protecting you from fraud.
Your Card's Security Code Explained in Simple Terms

Let's use an analogy. When you're in a shop, you prove you're the cardholder by tapping your card or entering your PIN. It's a physical action that verifies ownership. But how do you do that online or over the phone? That’s where the security code steps in.
This unique number is printed on your card, but it’s deliberately not stored on the magnetic stripe or the EMV chip. This separation is the clever bit. If a fraudster manages to get hold of your main card number—say, from a company data breach—they almost certainly won't have the security code too. Without it, the stolen data is far less likely to be useful for making dodgy purchases.
Why Does It Have So Many Names?
One of the biggest sources of confusion is the alphabet soup of acronyms for this little number. Don’t worry, it's simpler than it looks. Different card networks just use their own branding for the exact same security concept.
Here’s a quick guide to help you decode the jargon.
Decoding the Different Security Code Acronyms
| Acronym | Full Name | Card Network | Location |
|---|---|---|---|
| CVV | Card Verification Value | Visa | 3 digits on the back, by the signature |
| CVC | Card Verification Code | Mastercard | 3 digits on the back, by the signature |
| CID | Card Identification Number | American Express | 4 digits on the front of the card |
| CSC | Card Security Code | General Term | N/A |
At the end of the day, whether it's called a CVV, CVC, or CID, its function is always the same: to confirm you’re the genuine cardholder when your card isn't physically present.
The security code's primary role is to protect you during "card-not-present" transactions. It's a simple yet effective tool that confirms possession of the physical card, stopping fraud before it happens.
This code works hand-in-hand with the long number on the front of your card, which is officially known as the Primary Account Number, or PAN. If you’re curious about how they differ, you can learn about the difference between a PAN and other card details in our guide. Understanding these basic concepts is the first step toward making safer payments, whether online or over the phone.
How a Simple Code Stops Sophisticated Fraud
Think of it like this: a thief manages to get a copy of your house key, but they don't know the alarm code. They can unlock the door, but the second they step inside, all hell breaks loose. A card security code works in a very similar way for any payment where you’re not physically handing over your card—like when you’re shopping online or paying over the phone.
For these "card-not-present" transactions, the security code is that essential second check. It’s the digital proof that you actually have the card in your hand at that very moment. This one simple step creates a massive roadblock for fraudsters who primarily deal in stolen data.
Here’s the crucial part: even if criminals get their hands on huge lists of card numbers and expiry dates from a data breach, those lists almost never include the security codes. Why? Because businesses are strictly forbidden from ever storing them. This single rule makes stolen card information far less valuable and much harder for criminals to actually use.
The Missing Piece of the Puzzle
Imagine your card details are a puzzle. A fraudster might have the corner pieces—the long card number and the expiry date—but without that 3 or 4-digit security code, the picture is incomplete. The transaction simply won't go through. It’s the critical piece that makes the whole thing work.
This is especially vital in the UK. According to the latest data from UK Finance, while card fraud still resulted in losses of £572.6 million, the industry’s defences are getting stronger. A record £1.15 billion in attempted card fraud was blocked. That means for every £1 fraudsters tried to steal, 67p was stopped in its tracks. The humble security code is a cornerstone of that success.
A stolen card number is just a string of digits. A stolen card number with its security code is a key to your account. By separating these two elements, the payment system creates a powerful defence.
By demanding this code, merchants and banks can be reasonably sure that the person making the purchase has the physical card. It’s a straightforward check that disrupts a huge amount of criminal activity, protecting both customers from financial loss and businesses from the headache of chargebacks and fraud investigations.
Of course, this is just one line of defence. Modern security doesn't stop there. Today, this simple verification works alongside advanced fraud detection methods like machine learning that can spot suspicious patterns in real-time. It’s this combination of a simple, mandatory check and intelligent technology that keeps our payments safe.
Where to Find the Security Code on Your Card

Finding your card’s security code is simple once you know where to look. The catch? Its location changes depending on which company issued your card.
For the vast majority of cards, including Visa and Mastercard, the process is identical. Just flip your card over.
You’ll see a three-digit number printed on the back, usually to the right of the signature strip. This is your Card Verification Value (CVV) or Card Verification Code (CVC). It’s often the last group of numbers you see there, making it pretty easy to spot.
Locating the American Express Code
As you might expect, American Express (Amex) does things a little differently. Instead of a three-digit code on the back, Amex uses a four-digit number located right on the front of the card.
Take a look above the main card number, typically on the right-hand side. That four-digit code is the Card Identification Number (CID), and it serves the exact same security purpose as a CVV. This front-facing placement is unique to Amex and the most common point of confusion for new users.
Key Takeaway: For Visa and Mastercard, flip the card over to find the 3-digit CVV/CVC. For American Express, always check the front for the 4-digit CID.
Understanding these simple differences is vital. Whether you're a customer finalising a purchase or a contact centre agent guiding someone through a payment, knowing where to direct them saves time and keeps the process secure.
While the location might differ, the function is always the same: it provides a quick check to prove the card is physically in the hands of the person making the payment. This simple step is a powerful tool in preventing fraud.
The Critical Reason You Must Never Store Security Codes

Think about it this way: imagine a hotel that gives every guest a secure keycard but then leaves a master list of all the keycard codes sitting on the front desk. It would be a security nightmare, making every single room vulnerable.
The payment card industry sees storing security codes in exactly the same light—it’s an unacceptable risk that must be avoided at all costs.
This isn’t just good advice; it's a hard-and-fast rule, enforced by a global standard that every business has to follow.
At the heart of this rule is the Payment Card Industry Data Security Standard (PCI DSS). This is the official rulebook for any business that accepts, processes, stores, or transmits card information. Its entire purpose is to create a secure environment and stamp out card fraud.
Understanding PCI DSS Prohibitions
The PCI DSS is crystal clear on one point: once a transaction has been authorised, you must never store sensitive authentication data. This specific category of data includes the full magnetic stripe details, PINs, and—most importantly for this conversation—the card security code (CVV, CVC, or CID).
This strict prohibition is precisely what gives the security code its power.
Because businesses are forbidden from keeping it, the code remains a piece of information that should only be known by the person physically holding the card. It acts as a dynamic secret, used once for verification and then immediately discarded from the merchant's systems. This is why, even if a company's database gets hacked, the security codes shouldn't be part of the stolen data.
Storing this code, even by accident, shatters this fundamental security model.
A classic—and dangerous—oversight is capturing the security code in call recordings. If an agent asks a customer to read out their card details and your system records that conversation, you’ve just created an illegal and highly vulnerable copy of sensitive data.
The Serious Consequences of Non-Compliance
Ignoring these rules can have devastating consequences, and they go far beyond a simple slap on the wrist. Violating PCI DSS can trigger a cascade of problems that threaten a company's financial stability and its very reputation.
The potential penalties are no joke:
- Crippling Fines: Card networks can impose severe monthly fines, running from thousands to hundreds of thousands of pounds, until the business gets its house in order.
- Loss of Processing Rights: In serious cases, your acquiring bank can terminate your merchant account entirely. That means you lose the ability to accept card payments, period.
- Brand and Reputational Damage: A data breach involving improperly stored card data can vaporise customer trust, leading to lost business and long-term harm to your brand.
Ultimately, the rule couldn't be simpler: the card security code is for verification, not for storage. For any organisation handling payments, understanding and respecting this rule is non-negotiable.
To dig deeper into the specific requirements, our detailed guide provides essential information on achieving and maintaining PCI DSS compliance.
Taking Secure Payments in a Contact Centre
Here's the golden rule: you must never store a card security code.
But for a contact centre, that simple rule creates a massive headache. After all, conversations are routinely recorded for training and quality assurance. How can you possibly take a payment over the phone without accidentally capturing sensitive card details and breaking PCI DSS rules?
The answer isn't about trying to scrub the data after the fact. It's about preventing the security code from ever entering your business environment in the first place. Modern payment technologies act like a digital shield, creating a secure bubble around the transaction that keeps your agents, systems, and call recordings completely separate from those sensitive numbers.
Think of it as creating a secure, soundproof room just for the payment details. Your agent is still on the line, guiding the customer through the process, but the sensitive numbers are never spoken aloud or captured on your side.
How Technology Shields Your Business
Several key technologies work in concert to make this happen, each playing a vital role in removing your contact centre from the scope of the most demanding PCI DSS requirements. By bringing these tools into your workflow, you can slash your compliance burden and build deeper trust with your customers.
Best of all, these methods are designed to be seamless for both the agent and the customer.
- DTMF Suppression: This clever tech lets customers type their card details, including the security code, using their telephone keypad. The system masks the tones (Dual-Tone Multi-Frequency, or DTMF) so they sound like flat, unrecognisable beeps on the call recording. The agent stays on the line to help, but they never hear or see the actual numbers.
- Channel Separation: This technique intelligently diverts the sensitive part of the payment away from your agent and call recording system. For instance, the system might send the customer a secure link via SMS or chat to enter their details on their own device, all while they stay connected to the agent for support.
- Tokenization: This is like creating a secure stand-in for the real card data. Once a secure provider processes the payment, the sensitive information is swapped out for a unique, non-sensitive "token." This token can be safely stored and used for future transactions (like recurring payments) without ever exposing the original card number or security code.
These technologies are cornerstones of modern payment security. For a wider view of secure payment processing and industry best practices, digging into payment security insights from payments experts can offer a wealth of knowledge.
Putting Secure Payments into Practice
You really can't overstate how important these solutions are in the UK payment world. While fraud prevention is getting better, criminals are always finding new angles.
In a recent year, the industry managed to prevent £1.45 billion in unauthorised fraud—a 16% increase on the previous period. That breaks down to blocking about 67p of every £1 of attempted fraud, which just goes to show how critical robust security measures have become.
By adopting these modern methods, contact centres can completely transform how they handle payments. Instead of agents manually handling sensitive data and management worrying about compliance, they can focus on what they do best: providing excellent customer service. This approach not only protects your business from hefty fines and reputational damage but also proves to your customers that you take their security seriously.
For businesses ready to put these strategies into action, our guide on how to accept card payments over the phone provides practical steps and more detail.
Your Top Questions About Card Security Answered
As we've walked through what the security code is and why it matters, a few common questions always pop up. Let’s tackle those head-on to clear up any lingering confusion and give you a complete picture of how modern card security works in practice.
Is the Security Code the Same as My PIN?
Not at all – they’re designed for completely different jobs. Your PIN (Personal Identification Number) is the secret code you use for in-person transactions, like getting cash from an ATM or using a chip-and-PIN machine in a shop. It should never, ever be shared online.
The security code (CVV/CVC), on the other hand, is built specifically for payments where the card isn’t physically there, like over the phone or on a website. It’s your way of proving you have the actual card in your hand.
What Should I Do if My Security Code Is Stolen?
If you have even the slightest suspicion that your card details, including the security code, have been compromised, you need to contact your bank or card issuer immediately. Don't wait.
They will block your current card to stop any fraudulent payments and send you a new one with a fresh security code. Acting fast is the single best thing you can do to protect your money.
Key Takeaway: The security code is a powerful layer of defence, but it's not a magic shield. If you think it's been stolen, report it to your bank right away to secure your account.
Can a Business Legally Store My Security Code?
Absolutely not. It's a huge no-no. Global payment security rules, known as the PCI DSS, strictly forbid any business from storing the security code after a transaction is authorised.
This ban covers everything—databases, text files, and even call recordings. This is why proper secure payment platforms are designed to ensure this data never even touches a company’s systems, protecting both you and the business from risk.
This diagram shows how modern payment solutions create a secure bubble around this sensitive data.
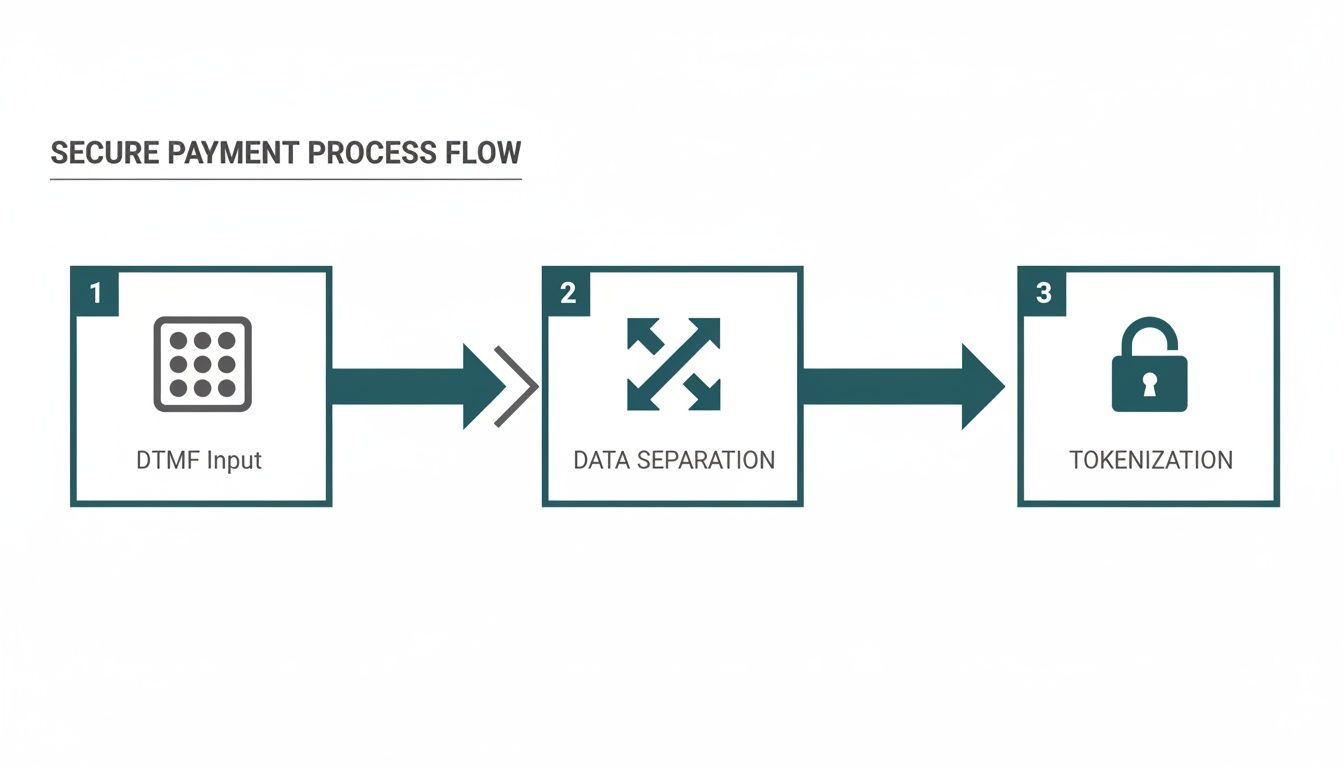
This process uses a combination of technologies like DTMF masking and tokenisation to keep those crucial three or four digits completely out of the business's environment.
Why Do Some Websites Not Ask for the Security Code?
It’s a balancing act for merchants. While asking for the code is a security best practice, some online stores might skip it to make the checkout process faster and smoother. This is usually because they have other advanced fraud detection tools running in the background.
However, choosing to process a payment without a CVV check often means the merchant accepts a higher risk. If fraud occurs, the liability usually falls on them. For any payment taken over the phone, though, verifying the code is an absolutely essential security step.
At Paytia, we build secure payment environments that take the risk out of the equation, protecting businesses and their customers from fraud. Learn how Paytia can de-scope your contact centre from PCI DSS and build trust with every transaction.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
