
What Is PCI DSS A UK Guide for Contact Centres
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
If you take card payments, you've probably heard of PCI DSS. But what exactly is it?
Put simply, the Payment Card Industry Data Security Standard (PCI DSS) is the essential rulebook for any business that accepts, processes, or even just comes into contact with customer card details. It's not a government law, but a set of mandatory security standards created by the major card brands—think Visa, Mastercard, and American Express—to fight card fraud and prevent data theft.
The Essential Rulebook for Payment Security

Think of it like this: PCI DSS is to card payments what the DVLA's rules are to driving. Not every single rule is a specific law, but if you want to use the road network, you have to follow them. They’re there to prevent accidents. In the same way, PCI DSS gives businesses a clear framework to prevent data breaches—the incredibly costly "accidents" of the payment world.
This standard applies to every single UK business that stores, processes, or transmits cardholder information. It doesn’t matter if you’re a small shop taking a few payments a day or a massive enterprise; if you touch card data, you need to comply. For contact centres that take payments over the phone, this is especially critical, as agents and systems are constantly handling highly sensitive information.
Who Created and Enforces PCI DSS?
The standard was developed by the PCI Security Standards Council (PCI SSC), an independent body formed by American Express, Discover, JCB International, Mastercard, and Visa. But here’s a common misconception: the council itself doesn’t enforce compliance.
So, who does? Your acquiring bank—the financial institution that processes card payments on your behalf. Compliance is enforced through your contract with them. If you fail to meet the standard, your acquirer is the one who will impose penalties, which can range from hefty fines to completely revoking your ability to accept card payments.
The core purpose of PCI DSS is straightforward: to create a secure environment for cardholder data. It outlines the technical and operational requirements needed to protect this information at every single point in the payment process.
Getting to grips with PCI DSS is the first step towards building a secure payment strategy. It’s how you protect your customers, safeguard your hard-earned reputation, and avoid crippling financial penalties. For contact centres, following these rules isn't just about ticking boxes—it's a fundamental part of building and maintaining customer trust.
Understanding the Four PCI DSS Merchant Levels
Your journey to PCI DSS compliance starts with a simple but crucial question: where does your business fit in? The answer lies in your merchant level, a classification based almost entirely on how many card payments you process each year. Think of it like a vehicle's MOT – a heavy goods vehicle needs a far more rigorous inspection than a small city car, and the same logic applies here.
This system isn't about penalising bigger businesses. It's about matching the level of risk with the right level of security validation. A multinational retailer handling millions of payments is a much bigger target for criminals than a local bakery. It only makes sense that their security measures have to withstand tougher scrutiny.
Figuring out which of the four levels applies to you is the first critical step. It dictates exactly what you need to do to prove you're compliant, ranging from a straightforward self-check to a full, independent on-site audit.
Level 1 Merchants: The Highest Scrutiny
This is the top tier, reserved for the largest enterprises. In the UK, a merchant is classed as Level 1 if they process over six million card transactions annually across all channels – whether that’s in-store, online, or over the phone. A company that has suffered a data breach can also be bumped into this category, regardless of its size.
Because of the sheer volume of sensitive data they handle, Level 1 merchants face the most demanding validation process:
- Annual Report on Compliance (ROC): This isn't just a form-filling exercise. It's a comprehensive on-site audit performed by an independent Qualified Security Assessor (QSA), who meticulously checks every aspect of the company's security against the 12 PCI DSS requirements.
- Quarterly Network Scans: These scans must be carried out by an Approved Scanning Vendor (ASV). Their job is to probe the company’s networks from the outside, looking for any security holes that hackers could exploit.
- Attestation of Compliance (AOC): This is the final sign-off, a formal declaration signed by both the business and the QSA, confirming that everything is fully compliant.
Levels 2, 3, and 4: The Self-Assessment Path
For the vast majority of businesses that fall below the six million transaction mark, the process is less intense. The core security rules of PCI DSS still apply to everyone, but how you prove you’re compliant changes. Instead of a QSA audit, you can usually manage it yourself through self-assessment.
For a quick overview of how these levels generally break down for UK businesses, take a look at the table below.
PCI DSS Merchant Levels at a Glance (UK)
| Merchant Level | Annual Transaction Volume | Typical Validation Requirement |
|---|---|---|
| Level 1 | Over 6 million transactions | Annual Report on Compliance (ROC) by a QSA |
| Level 2 | 1 to 6 million transactions | Self-Assessment Questionnaire (SAQ) and Attestation of Compliance (AOC) |
| Level 3 | 20,000 to 1 million e-commerce transactions | Self-Assessment Questionnaire (SAQ) and Attestation of Compliance (AOC) |
| Level 4 | Under 20,000 e-commerce transactions | Self-Assessment Questionnaire (SAQ) and Attestation of Compliance (AOC) |
Note: These are general guidelines. Your acquiring bank always has the final say on your specific requirements.
Each of these levels corresponds to different versions of the Self-Assessment Questionnaire (SAQ). This is a crucial document that guides you through a self-evaluation of your security setup. The specific SAQ you need to complete depends not just on your merchant level, but on how you take payments (e.g., online, in-person, over the phone).
Your merchant level isn't a badge of honour—it's a risk indicator. The higher your level, the more rigorously you must prove that your defences are sound, protecting both your customers and your business.
Getting this right is fundamental. Choosing the wrong SAQ can waste a huge amount of time and effort, or worse, leave you non-compliant without realising it. Pinpointing your exact obligations from the start is the key to a manageable and effective security strategy. Our guide can help you understand the different levels of PCI compliance and their requirements in more detail.
Decoding the 12 Core PCI DSS Requirements
At the heart of PCI DSS, you’ll find 12 core requirements. Now, these aren't just arbitrary rules dropped from on high; they form a logical framework designed to protect cardholder data at every turn. For a busy contact centre, that number can sound pretty daunting, but they’re all built on solid, common-sense security principles.
Instead of just giving you a dry, technical checklist, let's group them into six core security goals. Each goal is supported by two specific actions. Thinking about it this way helps clarify the why behind each rule, making them far easier to understand and, more importantly, to implement in your day-to-day operations.
The image below shows how different businesses, or 'merchants', are categorised based on how many card transactions they handle. This 'merchant level' dictates how rigorously they need to prove they're meeting these 12 requirements.
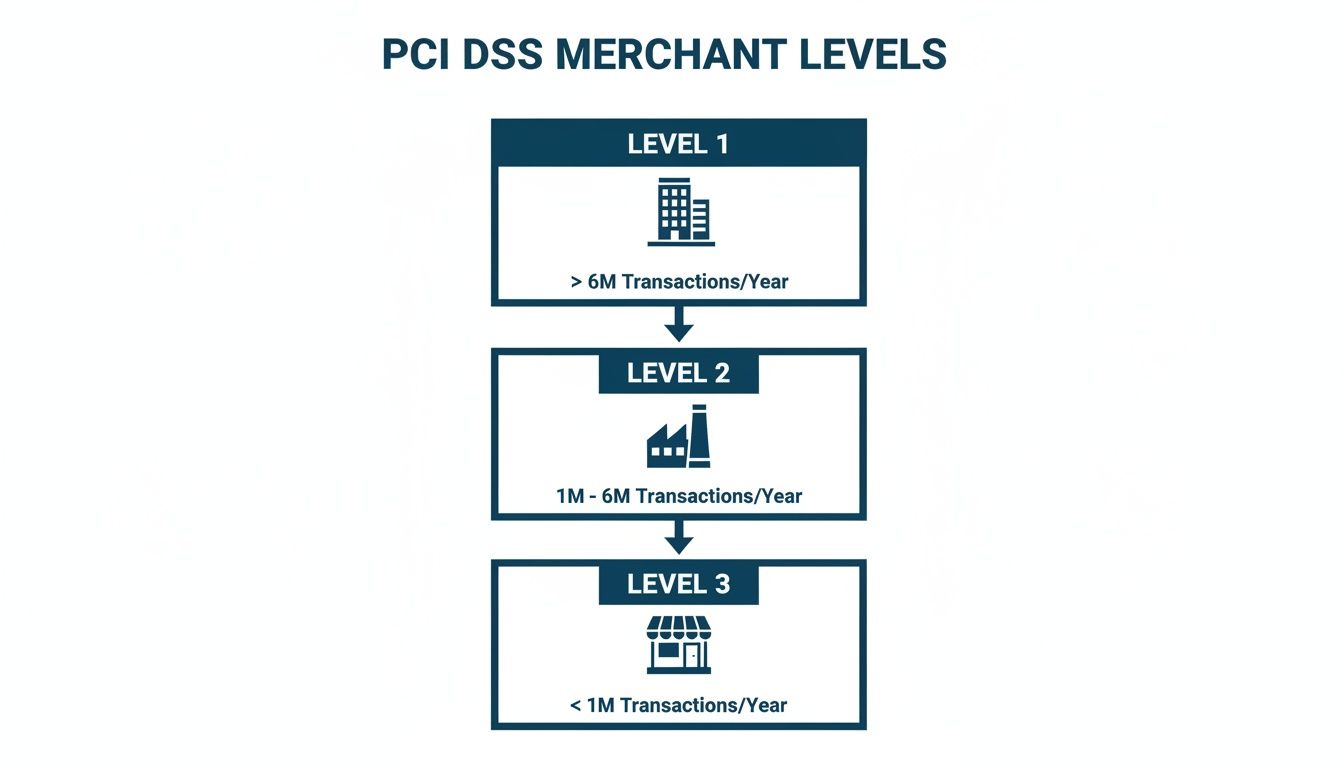
As you can see, the more you process, the more intense the scrutiny. It scales all the way from a straightforward self-assessment for smaller businesses to a full-blown, on-site audit for the big players.
Goal 1: Build and Maintain a Secure Network
First things first: you need to build strong digital walls around your systems. You wouldn’t leave the front door of your office unlocked, and the same logic applies to your network. This is your first line of defence against intruders.
Requirement 1: Install and Maintain Network Security Controls. This is all about using firewalls. In a contact centre environment, a well-configured firewall is critical. It acts as a gatekeeper, ensuring only trusted traffic can get anywhere near your phone systems, CRM, and payment applications, effectively blocking potential threats at the perimeter.
Requirement 2: Apply Secure Configurations to All System Components. Default passwords and out-of-the-box settings are a hacker's dream. This rule is simple: change all vendor-supplied defaults immediately. You also need to strip out any unnecessary software or functions to shrink your "attack surface," leaving fewer potential entry points for criminals to exploit.
Goal 2: Protect Account Data
Once your perimeter is secure, the next job is to protect the crown jewels: the sensitive card information inside your network. This data is what criminals are after, so it has to be shielded, whether it's sitting on a server or moving between systems.
Requirement 3: Protect Stored Account Data. The golden rule here is, if you don't need it, don't store it. If you absolutely have to hold onto card data, it must be rendered unreadable using strong methods like encryption, truncation (masking part of the number), or tokenisation. For call recordings, this means ensuring card details are never captured in the first place.
Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission. When data is on the move across open networks like the internet, it’s incredibly vulnerable. This requirement mandates the use of robust encryption (like TLS) to protect payment details being sent via email links or other digital channels.
Key Takeaway: The whole point of these first four requirements is to make cardholder data completely useless to criminals, even if they somehow manage to get their hands on it. Strong encryption and secure network configurations are non-negotiable.
Goal 3: Maintain a Vulnerability Management Programme
Security isn’t a one-and-done task; it’s a constant process of vigilance. Threats evolve and new technologies bring new risks, so you need a programme to regularly find and fix security weaknesses before they can be exploited.
Requirement 5: Protect All Systems and Networks from Malicious Software. This is your digital immune system. It means installing and, crucially, regularly updating anti-virus and anti-malware software on every system that could be affected. It's your defence against known threats.
Requirement 6: Develop and Maintain Secure Systems and Applications. All software needs looking after, whether you built it yourself or bought it from a vendor. This rule is about applying security updates and patches promptly to close any newly discovered vulnerabilities.
Goal 4: Implement Strong Access Control Measures
Let’s be honest: not everyone in your company needs to see sensitive customer data. This goal is all about the "principle of least privilege"—giving employees access only to the specific information and systems they absolutely need to do their jobs, and nothing more.
Requirement 7: Restrict Access to Cardholder Data by Business Need to Know. Access to cardholder data should be on a strictly need-to-know basis. In a contact centre, that means agents shouldn't see full card numbers unless it is absolutely critical for their specific role.
Requirement 8: Identify and Authenticate Access to System Components. Every single person who logs into your systems needs a unique ID. This rule stamps out the dangerous practice of shared logins and demands strong authentication—like multi-factor authentication (MFA)—to prove users are who they say they are.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you can't see. This goal is about keeping a watchful eye on your network at all times and regularly stress-testing your defences to make sure they're still holding up.
Requirement 9: Restrict Physical Access to Cardholder Data. This one isn't just about digital security. It also covers physical servers, paper records with card details, and payment terminals. This data must be kept in locked rooms or secure cabinets, with all access logged and monitored.
Requirement 10: Log and Monitor All Access to System Components and Cardholder Data. Good logging creates a digital paper trail. By tracking every time someone accesses network resources or card data, you can spot suspicious activity early and investigate potential breaches effectively.
Goal 6: Maintain an Information Security Policy
Finally, a strong security culture is built on clear rules and responsibilities. This last goal ties everything together. It ensures your security practices are formalised, written down, and properly communicated to everyone in the organisation.
Requirement 11: Test Security of Systems and Networks Regularly. This involves proactive measures like running regular vulnerability scans and hiring ethical hackers for penetration tests to find and fix security holes before the bad guys do.
Requirement 12: Support Information Security with Organisational Policies and Programs. You need a formal, written security policy that clearly defines everyone's role. This covers everything from staff security training and incident response plans to how you manage the security of third-party service providers.
To make sure you’ve got everything covered, you can explore the full PCI DSS requirements checklist for a more detailed breakdown.
How to Drastically Reduce Your PCI Compliance Scope
Think about being asked to secure an entire castle. You’d have to post guards on every wall, watch every tower, and check every secret passage. Now, what if you only had to secure a single, heavily fortified vault tucked away inside that castle? Which job sounds easier, cheaper, and a lot less stressful?
This is the core idea behind PCI scope reduction.

Your PCI scope covers every person, process, and piece of technology in your business that stores, processes, or transmits cardholder data. The bigger that scope, the more systems you have to protect, document, and prove are compliant. That means more work, higher audit costs, and a much larger attack surface for criminals to target.
Reducing your scope is the single most powerful strategy for simplifying PCI DSS compliance. By cleverly removing sensitive data from your environment, you shrink your sprawling "castle" down to a manageable "vault," dramatically cutting the effort and expense needed to stay secure.
The Power of Removing Data from Your Environment
The goal of scope reduction is simple: stop sensitive cardholder data—like the full card number (PAN) and the CVC—from ever entering your systems. If the data isn't there, you don't have to protect it under PCI DSS rules. It’s that straightforward.
For contact centres, this is a total game-changer. Traditionally, agents hearing card numbers over the phone brought the entire telephony system, call recording software, and agent workstations into PCI scope. This created a massive and complex compliance headache.
Modern technology completely flips this model on its head. It intercepts the payment details before they ever reach your business, creating a secure barrier between your environment and the sensitive data.
Practical Technologies for Scope Reduction
So, how do you actually do this? A few proven technologies are designed specifically to take your contact centre out of scope, letting you process payments seamlessly without ever handling the raw card details.
Here are the key players:
- DTMF Masking: When a customer pays over the phone, they use their telephone keypad to enter their card details. Dual-Tone Multi-Frequency (DTMF) masking technology intercepts these tones, stopping them from being heard by the agent or captured by call recording systems. The agent stays on the line to guide the customer, but the sensitive data bypasses your network completely.
- Secure Digital Payment Links: Instead of asking for card details verbally, agents can send the customer a secure, one-time payment link via SMS, email, or web chat. The customer then completes the transaction on their own device through a secure payment page. The data is never spoken, seen, or stored by your business.
By adopting these methods, you effectively de-scope your agents, phone systems, and call recordings. This doesn't just simplify audits; it fundamentally strengthens your security by eliminating the main way data gets stolen in a contact centre.
The Real-World Impact on UK Businesses
Implementing scope reduction isn't just a theoretical exercise; it has a profound impact on your security and your resources. In the UK, PCI DSS compliance remains a huge challenge. Global studies show that only about 32% of organisations fully maintain their compliance year-on-year. That figure highlights the very real risks facing UK contact centres that process card payments.
With the average cost of a data breach running into the millions, the stakes are incredibly high. You can find out more about the state of PCI DSS adoption and enforcement from this study.
Platforms that actively reduce your PCI scope are vital for managing this risk. By preventing sensitive data from ever touching your infrastructure, you can confidently remove entire departments and systems from the scrutiny of an audit. The result is a simpler, more affordable, and far more secure way to meet your compliance obligations.
Preparing Your Business for PCI DSS 4.0
The world of payment security doesn't stand still, and the arrival of PCI DSS 4.0 is the biggest shake-up to the standard we’ve seen in years. For UK businesses, this isn't just a minor version update; it's a fundamental shift in how you need to think about and manage compliance. The transition is already well underway, so getting to grips with what's new is essential for staying ahead of the curve.
Version 4.0 officially moves us away from the old, rigid, "tick-box" mentality that often dominated compliance efforts. In its place is a more flexible, goal-oriented framework. This means you can now implement security controls that genuinely fit your specific technology stack and business model, as long as you can prove they meet the standard's core security objectives. It’s a welcome change from prescriptive rules to objective-based security.
This evolution acknowledges that a one-size-fits-all approach just doesn't work anymore in a world of cloud services and diverse payment channels. It empowers businesses to innovate securely, but it also dials up the responsibility, placing a greater emphasis on conducting thorough risk analyses to justify the security measures you choose.
The Shift to a Customised Approach
One of the headline changes in PCI DSS 4.0 is the introduction of the Customised Approach. This new pathway lets you meet a requirement's objective using a different method than the one spelled out in the standard. Think of it like being given a destination but having the freedom to choose your own route to get there, rather than being forced to follow a single, prescribed map.
To go down this road, you'll need to:
- Conduct a targeted risk analysis for each control you customise.
- Document everything meticulously to prove your solution meets the original goal.
- Test and validate that your custom control is actually effective in practice.
This flexibility is a game-changer, especially for businesses using modern cloud technologies or unique operational setups. It does, however, demand a mature understanding of risk management. For many, sticking with the traditional, defined approach will still be the simpler and more straightforward path.
Key New Requirements and Deadlines
The transition to v4.0 isn't an overnight switch. While the new standard was published back in early 2022, businesses have been given a grace period to adapt. Many of the new requirements were considered best practice until 31 March 2025, at which point they become mandatory.
PCI DSS 4.0 introduces a whopping 64 new requirements. Of those, 51 become mandatory on that key date. These changes mean UK firms will have to perform more rigorous penetration testing annually or after significant changes, bringing the standard more in line with frameworks like UK GDPR and Cyber Essentials. You can discover more insights about PCI DSS 4.0 facts and compliance for 2025 to really dig into the details.
Let’s break down some of the most impactful changes that UK businesses, particularly contact centres, need to be ready for.
Key Changes from PCI DSS 3.2.1 to 4.0
The move to PCI DSS 4.0 introduces several critical updates. The table below highlights some of the most significant changes and what they mean for UK contact centres grappling with payment security.
| Requirement Area | What's New in PCI DSS 4.0 | Impact on UK Contact Centres |
|---|---|---|
| Authentication | Stronger multi-factor authentication (MFA) is now required for all access into the cardholder data environment, not just for administrators. | Every user, from agents to managers, will need to use MFA to access payment systems or CRMs that handle card data. |
| E-commerce Security | New requirements to manage all payment page scripts and protect against client-side attacks like e-skimming. | If you use web chat or payment links, you must have controls to detect and prevent unauthorised scripts from running on your payment pages. |
| Risk Analysis | A greater emphasis on conducting regular, targeted risk analyses to define the frequency of certain security activities. | Your business will need to formally document why certain security tasks (e.g., log reviews) are performed at their chosen frequency, based on risk. |
As you can see, these aren't just minor tweaks. The new standard requires a more thoughtful and proactive approach to security across the board.
PCI DSS 4.0 isn't just an update; it's a strategic realignment. It demands that businesses move from a passive, checklist-driven compliance model to a proactive, risk-aware security posture.
The most effective way to prepare is to proactively adopt modern security tools. For instance, using a platform like Paytia to de-scope your contact centre from ever handling card data directly can dramatically simplify your transition to v4.0. By preventing sensitive data from entering your systems in the first place, you make it far easier to meet the stricter authentication and security requirements and future-proof your entire compliance strategy.
The True Cost of PCI DSS Non-Compliance
Thinking of PCI DSS as just another box-ticking exercise is a dangerous mistake. It’s like seeing a "Danger: High Voltage" sign and deciding to ignore it. The consequences aren't just theoretical; they can be sudden, severe, and send shockwaves through your entire business, causing damage that lasts for years.
Many organisations get fixated on the initial fines, but that’s only the beginning of the story. The real cost is a brutal mix of immediate penalties, crippling reputational damage, and long-term operational chaos.
The Immediate Financial Penalties
The first hit comes directly from your acquiring bank. If a breach happens on your watch, or even if you just miss your compliance validation deadline, your acquirer can—and will—impose some hefty penalties. These are not gentle warnings.
Fines for non-compliance can range from £4,000 to £80,000 per month. The final figure depends on the size of your business and just how serious the compliance failure is. In a worst-case scenario, they can pull the plug entirely by terminating your merchant account. For most businesses, losing the ability to take card payments is game over.
A single data breach does more than just leak data; it shatters the trust you’ve spent years building with your customers. Rebuilding that confidence is often a much harder and more expensive fight than covering the initial financial losses.
The Hidden Costs That Cripple Businesses
Beyond the fines from your bank and the card brands, a compliance failure opens the floodgates to a whole host of other costs that can be even more damaging. These are the expenses that don’t show up on the initial penalty invoice but can slowly bleed a business dry.
This is where the real pain is felt:
- Forensic Investigations: After a suspected breach, you’ll be mandated to hire a specialist Payment Forensic Investigator (PFI) to figure out what went wrong. These investigations are meticulous, intrusive, and incredibly expensive, often running into tens of thousands of pounds before you even know the full extent of the damage.
- Brand and Reputation Damage: Trust is your most valuable asset, and a data breach destroys it in an instant. Customers will leave, and attracting new ones becomes a monumental challenge when your company name is associated with a security failure.
- Legal and Regulatory Action: In the UK, a card data breach almost always triggers an investigation by the Information Commissioner's Office (ICO) under GDPR. The potential fines are staggering—up to 4% of your annual global turnover. On top of that, you could be facing lawsuits from the very customers whose data was compromised.
When you add it all up, the financial case becomes crystal clear. Investing in a solid, proactive security strategy isn't just another business expense; it's the most critical insurance policy you can have against financial ruin.
How to Make Your PCI DSS Compliance Journey Easier
Feeling swamped by the complexities of PCI DSS? It's a common feeling, but getting compliant doesn't have to be an uphill battle. The secret isn't about ticking more boxes; it's about making your 'box' smaller. It all comes down to one core idea: drastically reducing your PCI scope.
The most straightforward way to do this? Stop sensitive card data from ever touching your business environment in the first place.

This is precisely what modern, scope-reducing payment platforms are built for. Think of them as a secure shield standing between your contact centre and your customer's raw payment details. When your systems, agents, and even your call recordings never come into contact with that data, the entire compliance conversation changes.
Turning Compliance from a Chore into an Asset
By bringing in the right technology, you can effectively "de-scope" huge chunks of your operation. Suddenly, what felt like a complex regulatory headache becomes a real strategic advantage, securing your payments and protecting your hard-earned reputation.
Here are a couple of powerful ways to shrink your scope:
- DTMF Suppression: This clever tech intercepts the tones a customer taps into their phone keypad. It masks the card details, meaning your agents and call recordings are never exposed to them. Your agent can stay on the line to help the customer, but the sensitive data completely bypasses your systems.
- Secure Payment Links: Instead of asking for card details over the phone, an agent can simply send a secure payment link via chat or SMS. The customer enters their information on their own device, keeping it completely separate from your contact centre.
By removing the data, you remove the risk. This proactive strategy not only makes achieving compliance simpler and cheaper but also strengthens your security posture against potential breaches and aligns perfectly with the goal-oriented principles of PCI DSS 4.0.
The benefits for UK contact centres are immediate and significant. Your audit costs can plummet, and the day-to-day management of compliance becomes far less of a burden. Most importantly, you build deeper trust with your customers by showing you’re serious about protecting their information. A detailed PCI DSS compliance checklist can be a huge help in guiding you through the process.
This shift in approach changes what PCI DSS is all about. It’s no longer just a set of rules to follow; it becomes about building a secure, efficient, and trustworthy payment experience for everyone.
Ready to take the complexity out of PCI DSS compliance? Paytia's secure payment platform removes sensitive card data from your contact centre, reducing scope by up to 95%. Discover how to lower costs, simplify audits, and build customer trust at https://www.paytia.com.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
