
Understanding the Credit Card Security Code
Get Secure Payment Solutions
Learn how Paytia can help secure your payment processing.
That little three or four-digit number on your credit card? It’s called a credit card security code, and it’s one of the simplest yet most effective tools for keeping your money safe. When you buy something online or over the phone, merchants ask for this code to prove that you actually have the card in your hand.
Think of it as a quick, digital check-in. It confirms you’re the legitimate cardholder, not just someone who found a lost receipt or stole a card number from a database. This simple step is a critical first line of defence against would-be fraudsters.
Your Guide to Card Security Codes

It’s helpful to think of the difference between your main card number and your security code like this: the 16-digit number is your public address, telling the merchant where to send the bill. The security code, on the other hand, is like a one-time-use key to your front door. It’s a secret you share only at the moment you’re making a purchase.
This distinction becomes absolutely vital in what the industry calls "card-not-present" (CNP) transactions. Whenever you aren't physically tapping your card or inserting its chip, the risk of fraud shoots up. That tiny security code is what bridges the trust gap.
The Different Names for One Important Number
You’ve probably seen a few different acronyms for this code, which can get confusing. While they all do the exact same job, each major card network has its own preferred term:
- CVV or CVV2: Stands for Card Verification Value, the term used by Visa.
- CVC or CVC2: This is the Card Verification Code, which you’ll see associated with Mastercard.
- CID: Short for Card Identification Number, used by American Express (and uniquely placed on the front of the card).
- CSC: A more generic term, Card Security Code, that you might see used.
Here’s the clever bit: this code is only printed on the card. It's not stored on the magnetic stripe and it's not embedded in the EMV chip. This is intentional. It means that even if a criminal manages to "skim" your card data from a dodgy payment terminal, they still won't have the security code, which stops them from using those stolen details for online shopping sprees.
Your Guide to Finding the Security Code
To make it easy to find the code on your own cards, here's a quick reference guide.
| Card Network | Code Name | Number of Digits | Location on Card |
|---|---|---|---|
| Visa | CVV/CVV2 | 3 | On the back, in the signature strip |
| Mastercard | CVC/CVC2 | 3 | On the back, in the signature strip |
| American Express | CID | 4 | On the front, above the card number |
| Discover | CID | 3 | On the back, in the signature strip |
Knowing where to look and what this code does is a great first step towards protecting your payment details. If you're keen to explore this topic further, you can learn more about what is the security code on a card and its vital role in modern transactions.
The Surprising UK Origins of the Security Code
It’s easy to think of that little number on the back of your card as a modern security feature, born from the internet age. But its story actually begins much earlier, in an era of mail-order catalogues and landline phone calls. The entire concept was invented right here in the UK to solve a problem that’s still a huge challenge for businesses: how to safely take a payment when you can’t see the customer or their card.
Back in 1995, a man named Michael Stone, who worked for Equifax, came up with the idea. He created it specifically to secure transactions for mail-order companies and telephone sales — the original “card-not-present” fraud hotspots. His first version wasn't the simple three or four digits we see today; it was a much more complex 11-character alphanumeric code.
From Complex Code to Simple Standard
The first real-world test of this new security system involved Littlewoods Home Shopping and NatWest Bank. The trial was a success, and it didn't take long for the UK's payment authority, the Association for Payment Clearing Services (APACS), to see its potential for stopping the rising tide of fraud.
APACS took the core idea and simplified it, creating the three-digit credit card security code standard that became the global norm. This backstory is more than just a bit of trivia; it shows that the security code was never an afterthought.
It was purpose-built from day one to solve a single, critical problem: proving that the person making a remote purchase actually has the physical card in their hands. That simple principle is still its greatest strength.
When you understand where it came from, you see the security code for what it is—not just a random number, but a clever defence mechanism born out of necessity. The challenges of taking secure payments over the phone in the 90s directly paved the way for protecting the billions of online and contact centre transactions we see every day. This British innovation truly became a cornerstone of global payment security, a journey you can explore by reading more about the history of UK payment milestones.
How Your Security Code Stops Fraudsters

The real magic of the security code happens when a payment is made remotely. In any situation where your customer isn't physically there to tap or insert their card, that little three or four-digit number becomes your most important defence against fraud.
Think of it as a digital handshake. A fraudster might buy a list of stolen credit card numbers and expiry dates from a data breach—sadly, this information is all too common on the dark web. But without the security code, those stolen details are often completely useless for making online or phone purchases.
That's because the security code is deliberately kept separate from all other card data. It's printed on the physical card but isn't stored in the magnetic stripe or the chip. Crucially, businesses are strictly forbidden from ever storing it after a transaction is authorised. This single rule makes huge databases of stolen card numbers far less of a goldmine for criminals.
The Rise of Card-Not-Present Fraud
This simple security feature is more vital today than ever before. The single biggest threat facing UK businesses is card-not-present (CNP) fraud, which is the official term for any transaction made online, by mail order, or over the phone.
And the scale of the problem is staggering. In 2022, total card fraud losses in the UK hit £556.3 million. A massive 81% of that—or £396 million—came directly from CNP fraud, where getting the security code is often the final step for a criminal. These UK finance fraud statistics highlight a huge vulnerability for any business that takes payments remotely, especially contact centres.
The security code acts as a firewall. It separates the static data that gets stolen so often (card number, expiry date) from the proof that someone actually has the card in their hand. It’s the difference between knowing someone’s address and having the key to their front door.
Why It Is Your Last Line of Defence
For a fraudster, getting that security code is the final piece of the puzzle. Once they have it, they can sail past the main security checks on most e-commerce and telephone payment systems. This is why protecting the CVV during the payment process itself is an absolute priority.
If a criminal cons a customer into revealing it through a phishing scam, or if an employee handles it insecurely over the phone, that protective barrier is completely gone. You can learn more about these risks in our guide on what card-not-present fraud means for your business. Getting to grips with this is the first step toward building a payment process that is genuinely secure.
The Golden Rule of Handling Security Codes
When it comes to handling customer payments, there’s one non-negotiable, absolute golden rule for the credit card security code. This isn't just a best practice; it's a strict mandate from the Payment Card Industry Data Security Standard (PCI DSS), the global framework that dictates how every business must protect cardholder data.
Put simply, the rule is this: you are strictly forbidden from storing the security code (CVV, CVC, or CID) after a transaction has been authorised.
That means nowhere. Not on a piece of paper, not in a spreadsheet, not in your CRM, and certainly not in any database. The moment that payment gets the green light, that three or four-digit code must be gone for good.
This isn't just bureaucratic red tape. It's the very core of what makes the security code such a powerful weapon against fraud. By making it illegal for merchants to store this code, the PCI DSS ensures that even if a criminal hacks a company’s database and makes off with millions of card numbers, they still won’t have the one piece of the puzzle they need to use those cards online or over the phone.
Why This Rule Is So Critical
Think about it. The entire security model is built to make stolen card databases less valuable. A list of card numbers and expiry dates is certainly a threat, but a list that also includes the security codes is a fraud catastrophe just waiting to happen. The "no storage" rule effectively pulls the rug out from under fraudsters by devaluing the data they work so hard to steal.
PCI DSS Requirement 3.2.2 puts it in no uncertain terms: "Do not store the card verification code or value (three- or four-digit number printed on the front or back of a payment card used to verify card-not-present transactions) after authorisation."
This single requirement is what turns the security code from just another piece of static, stealable information into a dynamic defence. It forces the code to be a "live" verification, proving the customer has the physical card in their hands at the very moment of purchase.
Where Businesses Often Go Wrong
For businesses with contact centres, this rule presents a unique and constant challenge. The fast-paced environment of taking payments over the phone can easily lead to accidental—and highly dangerous—compliance breaches.
Here’s a look at some of the most common mistakes we see:
- The Sticky Note Scramble: An agent quickly jots down the security code on a sticky note to type it into the payment system, but then forgets to shred it immediately.
- Accidental Call Recordings: Standard call recordings capture the customer saying their security code out loud, storing it in audio files that are often kept for years for quality assurance purposes.
- CRM and Note-Taking Traps: Staff might type the full card details, security code included, into an order notes field in their customer management software out of habit.
Each of these scenarios creates a serious security vulnerability and puts your business in direct violation of PCI DSS rules. Understanding this golden rule isn't just about avoiding hefty fines; it's about fundamentally protecting your customers and preserving the trust they place in your business every time they pay.
Security Code Handling Do's and Don'ts
To make this crystal clear, here’s a simple breakdown of what is and isn't allowed when your team handles security codes.
| Action | Compliant Practice (Do) | Non-Compliant Practice (Don't) |
|---|---|---|
| Data Entry | Enter the code directly into a validated, PCI-compliant payment system that immediately uses and discards it after authorisation. | Write the code down on paper, in a text file, or on a whiteboard, even for a few seconds. |
| Verbal Payments | Use a secure system (like DTMF masking) that prevents the agent from hearing or seeing the code and stops it from being recorded. | Allow the customer to read their security code out loud on a recorded phone line. |
| Digital Notes | Ensure no field in your CRM, order system, or internal chat allows for the security code to be typed or saved. | Type the full card number, expiry, and security code into a "notes" or "comments" field in any software. |
| Data Storage | Ensure your systems are configured to reject or immediately delete the security code post-authorisation. | Store the security code in any database, log file, or call recording archive. |
Following these "Do's" isn't just about compliance; it's about building a secure foundation for your payment processes. The "Don'ts" aren't just bad habits—they are critical security risks that expose your business and your customers to fraud.
Why Stolen Security Codes Are a Goldmine for Criminals
To really grasp why a simple three or four-digit credit card security code is so valuable to a criminal, you have to think bigger than just a single fraudulent purchase. Stolen card details aren't just used once and then discarded. They’re part of a massive, well-oiled illegal economy on the dark web where data is bought, sold, and traded like any other commodity. This isn't some distant threat; it's a bustling marketplace operating 24/7.
The moment your card number, expiry date, and security code are out in the wild, they become a product. Cybercriminals package this information into lists and sell them off for shockingly small amounts to fraudsters all over the world. For the buyers, it's a low-risk, high-reward business model that powers everything from dodgy online shopping sprees to full-scale identity theft.
The Dark Web Marketplace for Stolen UK Cards
This black market is a particularly big problem for anyone with a UK bank card. One eye-opening piece of research sifted through a database of 6 million stolen cards and found that Britain was the most targeted country in Europe. The study flagged a staggering 164,143 UK payment card details up for sale.
Even more worrying was the price. The average cost for a set of UK card details was just £4.61—far cheaper than the global average. This makes UK card data a bargain for criminals and directly fuels card-not-present fraud, which hit the UK for £396 million in 2022 alone. You can read more about the UK's vulnerability to card fraud to see the full picture.
The data becomes exponentially more valuable when the security code is part of the package. A card number on its own is difficult to use, but adding the CVV instantly unlocks it for online and phone-based fraud.
A stolen credit card security code is the key that turns a useless string of numbers into instant cash for a fraudster. It completes the package they need to bypass the most common online security checks.
How Your Data Ends Up for Sale
So, how do these security codes and card details get swiped in the first place? Criminals have a whole playbook of tricks they use to get their hands on this information, ensuring a steady supply for the dark web economy.
- Phishing Scams: These are the classic bait-and-switch emails or texts that lure you to a fake website—one that looks just like your bank or a favourite online shop—and trick you into typing in your details.
- Malware and Skimmers: Nasty software hiding on your computer can log everything you type, including card details. In the physical world, criminals attach "skimming" devices to ATMs or payment terminals to clone your card when you use it.
- Major Data Breaches: Hackers go after the big fish, targeting large companies to steal massive databases filled with millions of customer payment details in one fell swoop.
Once a credit card security code is exposed through any of these routes, it’s almost guaranteed to be used for fraud. That's precisely why being proactive about security is so incredibly important.
Modern Solutions for Securing Payment Data
After seeing how easily a stolen credit card security code can fuel fraud, it's pretty clear that old-school ways of handling payments just don't cut it anymore. The risk of an agent seeing or hearing sensitive details—or having them captured on a call recording—is simply too high. Thankfully, modern security technology gives us a much safer path forward.
These solutions are built on a simple but powerful idea: sensitive payment data should never even enter your business environment. It’s all about creating a secure bubble around the transaction, shielding your organisation from ever having to touch the data itself.
How Technology Shields Sensitive Codes
Two key pieces of technology make this happen: DTMF suppression and channel separation. They might sound a bit technical, but the concepts are actually quite straightforward.
Think of DTMF suppression as a smart 'digital mute button'. When a customer taps their security code into their telephone keypad, this technology cleverly masks the tones. Your agent can stay on the line to help, but all they hear is a flat, monotonous sound—not the distinct beeps that correspond to the numbers. The system captures the details securely without a human ever hearing them or a call recording ever storing them.
This process is designed to break the chain of fraud, which often starts with a single data breach and escalates quickly, as this diagram shows.
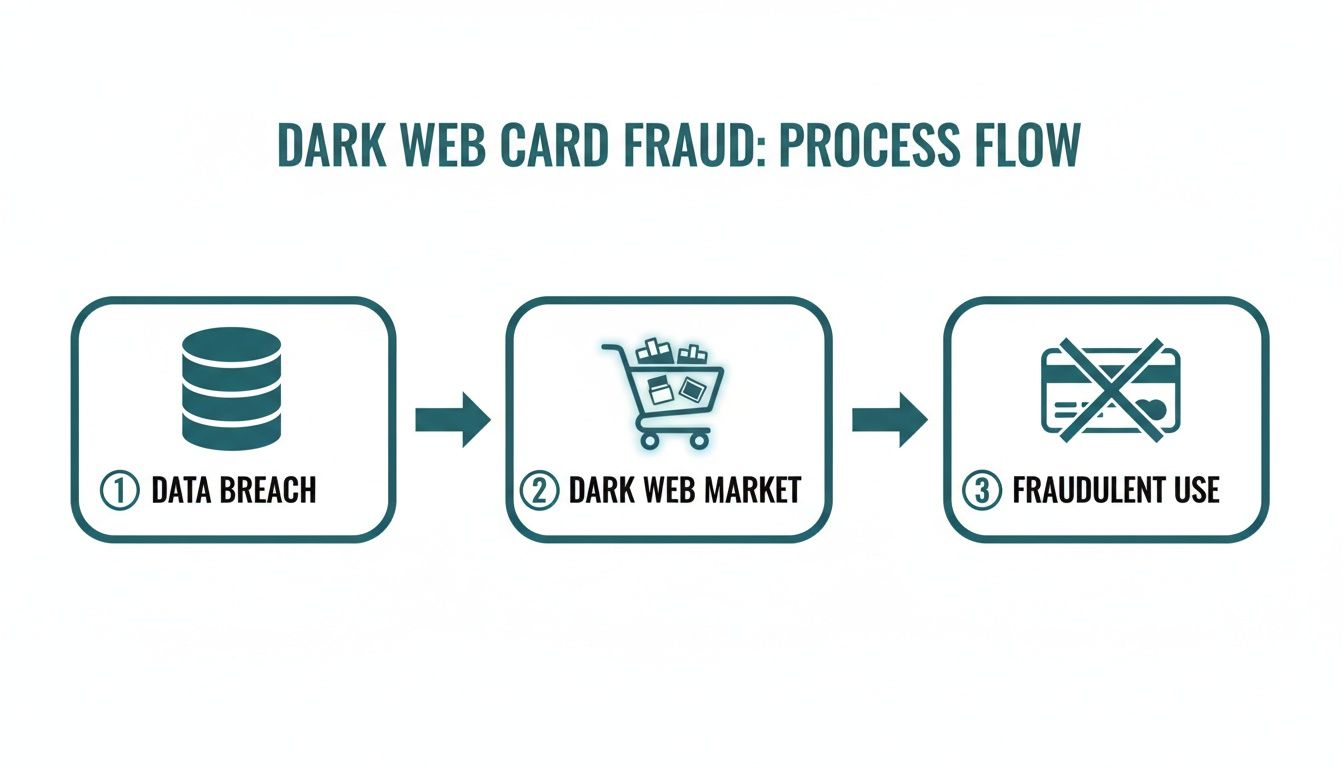
As you can see, once card details land on the dark web, they can be used for widespread fraudulent activity. Preventing that initial theft is everything.
Creating a Secure Payment Tunnel
Next up is channel separation, which you can picture as a secure, invisible tunnel. When it’s time to pay, this tech redirects the sensitive part of the conversation—like entering the security code or the long card number—straight from the customer to the payment processor.
The payment data completely bypasses your agents, your call recordings, and all your computer systems. It travels through its own encrypted channel, never once touching your network. This approach delivers some massive wins:
- Drastically Reduced PCI Scope: Because sensitive data never enters your environment, your PCI DSS compliance burden can shrink by as much as 90-95%.
- Elimination of Insider Threat: Agents can't see, hear, or access card details, which removes the risk of accidental exposure or internal fraud.
- Enhanced Customer Trust: Customers feel more confident knowing they aren't reading their private information aloud to a person.
The real game-changer here is that your business can process a payment without ever possessing the sensitive data. This neatly sidesteps the PCI DSS rule against storing security codes and protects you from the fallout of a data breach.
By bringing these solutions on board, you’re not just ticking a compliance box. You're fundamentally rebuilding your payment process to be secure by design. These techniques are often paired with other powerful tools. To explore another layer of protection, you can learn more about what tokenization is in payments and how it adds yet another safeguard for customer data.
Got Questions About Security Codes? We've Got Answers
Even when you think you have a handle on security codes, some practical questions always seem to pop up. Let's tackle a few of the most common ones so you can feel completely confident when dealing with payment details.
One of the biggest questions we hear is, "Can we save the security code for a customer's next purchase?" The answer is a hard no. Storing the security code after a transaction is authorised is strictly forbidden by PCI DSS rules, without exception. For things like subscriptions or repeat billing, businesses rely on a far more secure method called tokenization, where the real card data is swapped out for a unique, unusable placeholder.
But Why Don't Some Websites Ask For It?
You’ve probably noticed that some major online shops don't always ask for the security code, especially if you're a regular customer. So, what's going on there?
These retailers are often using sophisticated fraud prevention systems that look at far more than just your card number. They analyse hundreds of different signals in the background—things like the device you're using, your location, and your past buying habits. If their system flags the transaction as extremely low-risk, they might skip the CVV step to make checkout a bit smoother for you.
This risk-based approach shows that while the security code is a crucial defence, it’s just one tool in a much bigger toolbox that businesses use to keep payments safe.
What If I Think My Security Code Has Been Stolen?
Finally, the most critical question: what do you do if you think your security code has been compromised? The key is to act fast.
- Call your bank immediately. Let them know what you suspect. They can put a watch on your account for any strange activity or just cancel the card and issue a new one.
- Scour your recent statements. Look carefully for any transactions, big or small, that you don't recognise.
- Change your passwords. If you have a hunch that a specific online shop was the source of the breach, change your password on that site right away.
Taking these simple steps can be the difference between a close call and a serious financial headache.
Secure your customer payments and simplify your compliance with Paytia. Discover our solutions for protecting payment data over the phone and other channels.
Ready to Get Started?
Contact Paytia to learn how we can help secure your payment processing.
